FTP and LDAP - Part 2: How to Set Up an Active Directory Lightweight Directory Services (AD LDS) Server
16 September 2011 • by Bob • FTP, Extensibility
This blog is designed as a complement to my FTP and LDAP - Part 1: How to Use Managed Code (C#) to Create an FTP Authentication Provider that uses an LDAP Server blog post. In this second blog, I'll walk you through the steps to set up an Active Directory Lightweight Directory Services (AD LDS) server, which you can use with the custom FTP LDAP Authentication provider that I discussed in my last blog.
In This Blog
Step 1: Installing AD LDS
The following steps will walk you through installing Active Directory Lightweight Directory Services on a computer that is running Windows Server 2008.
Adding the AD LDS Role
- Open the Windows Server 2008 Server Manager, click Roles in the navigation pane, and then click Add Roles.

- Check the box for Active Directory Lightweight Directory Services, and then click Next.

- Read the information on the Introduction to Active Directory Lightweight Directory Services page, and then click Next.

- Verify the Confirmation Installation Settings, and then click Next.

- The installation will start; this may take several minutes to complete.

- When the installation has completed, click Close.

Creating an AD LDS instance
Note: Before completing these steps I created a local user account named "LdapAdmin" that I would specify the administrative account for managing my LDAP instance. This user account was only a member of the local "Users" group, and not a member of the local "Administrators" group.
- Click Start, then click Administrative Tools, and then click Active Directory Lightweight Directory Services Setup Wizard.

- When the Active Directory Lightweight Directory Services Setup Wizard appears, click Next.

- Select A unique instance, and then click Next.

- Enter a name for your instance, for example "MyTestInstance," and then click Next.

- Verify the port numbers for LDAP connections, and then click Next.

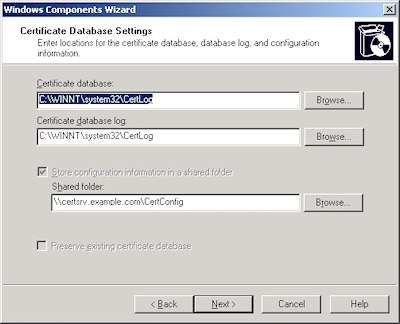
- Choose Yes, create an application directory partition, and then enter a unique partition name by using X.500 path syntax. For example: "CN=MyServer,DC=MyDomain,DC=local". When you have finished entering your partition name, click Next.

- Verify the paths to the AD LDS files for this instance, and then click Next.

- Choose an account for your service account. (Note: Because I was creating a standalone LDAP server, I chose to use the network service account.) Once you have chosen an account, click Next.

- If you choose to use the network service account, the AD LDS wizard will prompt you about replication. Click Yes to continue.

- Choose an account as your AD LDS administrator. (Note: In my situation I chose the LdapAdmin account that I had created earlier; I did this so that I wouldn't be storing the credentials for an administrative account.) Once you have chosen an account, click Next.

- Choose one of the following LDIF files to import; these will be used to create user accounts. Note: I tested my FTP LDAP authentication provider with both LDIF files.
- Verify your installation options, and then click Next.

- When prompted for your AD LDS credentials, enter the credentials for the account that you chose to administer your AD LDS instance.

- The wizard will begin to install the requisite files and create your instance; this may take several minutes to complete.


- When the wizard has completed, click Finish.

Step 2: Using ADSI Edit to add Users and Groups
Connecting to your AD LDS Server
- Click Start, and then Administrative Tools, and then ADSI Edit.
- Click Action, and then click Connect to...

- When the Connection Settingsdialog box is displayed:
- Enter the LDAP path for your AD LDS server in the Select or type a Distinguished Name or Naming Contexttext box. For example:
- CN=MyServer,DC=MyDomain,DC=local
- Enter the server name and port in the Select or type a domain or servertext box. For example:
- MYSERVER:389
- The preceding steps should create the following path in the Pathtext box:
- LDAP://MYSERVER:389/CN=MyServer,DC=MyDomain,DC=local

- Click the Advanced button; when the Advanceddialog box is displayed:
- Check the Specify Credentials box.
- Enter the user name and password for your AD LDS server.
- Click OK.

- Enter the LDAP path for your AD LDS server in the Select or type a Distinguished Name or Naming Contexttext box. For example:
- Click OK.
Adding a User Object
- Expand the tree until you have highlighted the correct LDAP path for your server. For example:
- CN=MyServer,DC=MyDomain,DC=local.

- Click Action, and then New, and then Object...

- Highlight the appropriate user class, and then click Next.

- Enter the common name for your user, and then click Next. For example: enter FtpUser for the common name.

- Click Finish.

- Right-click the user that you created, and then click Properties.

- Select msDS-UserAccountDisabled in the list of attributes, and then click Edit.

- Select False, and then click OK.

- Select userPrincipalName in the list of attributes, and then click Edit.

- Enter your user's common name for the value, and then click OK. For example: enter FtpUser for the common name.

- Click OK to close the user properties dialog box.
- Right-click the user that you created, and then click Reset Password...

- Enter and confirm the password for your user.

- Click OK.
Adding Users to Groups
- Retrieve the Distinguished Name (DN) for a user:
- Add the user to a group:
- Expand the tree until you have highlighted a group in your server. For example, you could use the built-in CN-Users group.

- Right-click the group, and then click Properties.

- Select member in the list of attributes, and then click Edit.

- When the editor dialog box is displayed, click Add DN...

- When the Add Distinguished Name (DN) dialog box appears, paste the user DN syntax that you copied earlier. For example: CN=FtpUser,CN=MyServer,DC=MyDomain,DC=local.

- Click OK to close the Add DN dialog box.

- Click OK to close the group's properties dialog box.
- Expand the tree until you have highlighted a group in your server. For example, you could use the built-in CN-Users group.
More Information
For additional information about working with AD LDS instances, see the following URLs:
- Manage an AD LDS Instance Using ADSI Edit
http://technet.microsoft.com/en-us/library/cc794959.aspx - Managing Directory Security Principals in the .NET Framework 3.5
http://msdn.microsoft.com/en-us/magazine/cc135979.aspx
Enabling the Custom FTP LDAP Authentication Provider for an FTP site
While this is technically outside the scope of setting up the LDAP server, I'm reposting the notes from my last blog about adding the FTP LDAP Authentication provider and adding authorization rules for FTP users or groups.
- Add the custom authentication provider for an FTP site:
- Open an FTP site in the Internet Information Services (IIS) Manager.
- Double-click FTP Authentication in the main window.
- Click Custom Providers... in the Actions pane.
- Check FtpLdapAuthentication in the providers list.
- Click OK.
- Add an authorization rule for the authentication provider:
- Double-click FTP Authorization Rules in the main window.
- Click Add Allow Rule... in the Actions pane.
- You can add either of the following authorization rules:
- For a specific user:
- Select Specified users for the access option.
- Enter a user name that you created in your AD LDS partition.
- For a role or group:
- Select Specified roles or user groups for the access option.
- Enter the role or group name that you created in your AD LDS partition.
- Select Read and/or Write for the Permissions option.
- For a specific user:
- Click OK.
Once these settings are configured and users connect to your FTP site, the FTP service will attempt to authenticate users from your LDAP server by using the custom FTP LDAP Authentication provider.
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
FTP and LDAP - Part 1: How to Use Managed Code (C#) to Create an FTP Authentication Provider that uses an LDAP Server
16 September 2011 • by Bob • FTP, Extensibility
Over the past few years I've created a series of authentication providers for the FTP 7.5 service that ships with Windows Server 2008 R2 and Windows 7, and is available for download for Windows Server 2008. Some of these authentication providers are available on the http://learn.iis.net/page.aspx/590/developing-for-ftp-75/ website, while others have been in my blog posts.
With that in mind, I had a question a little while ago about using an LDAP server to authenticate users for the FTP service, and it seemed like that would make a great subject for another custom FTP authentication provider blog post.
The steps in this blog will lead you through the steps to use managed code to create an FTP authentication provider that uses a server running Active Directory Lightweight Directory Services (AD LDS) that is located on your local network.
Note: I wrote and tested the steps in this blog using both Visual Studio 2010 and Visual Studio 2008; if you use an different version of Visual Studio, some of the version-specific steps may need to be changed.
In This Blog
- Step 1: Set up the Project Environment
- Step 2: Create the Extensibility Class
- Step 3: Add the Demo Provider to FTP
- Summary
Prerequisites
The following items are required to complete the procedures in this blog:
- The following version of IIS must be installed on your Windows computer, and the Internet Information Services (IIS) Manager must also be installed:
- IIS 7.0 must be installed on Windows Server 2008
- IIS 7.5 must be installed on Windows Server 2008 R2 or Windows 7
- The new FTP 7.5 service must be installed. To install FTP 7.5, follow the instructions in the following topic:
- You must have FTP publishing enabled for a site. To create a new FTP site, follow the instructions in the following topic:
- You must have an AD LDS server available on your local network. Note: See my How to Set Up an Active Directory Lightweight Directory Services (AD LDS) Server blog post for more information.
Note: To test this blog, I used AD LDS on Windows Server 2008; if you use a different LDAP server, you may need to change some of the LDAP syntax in the code samples. To get started using AD LDS, see the following topics:
- AD LDS Getting Started Step-by-Step Guide
http://technet.microsoft.com/en-us/library/cc770639.aspx - Create a New AD LDS Instance
http://technet.microsoft.com/en-us/library/cc816778.aspx
I tested this blog by using the user objects from both the MS-User.LDF and MS-InetOrgPerson.LDF Lightweight Directory interchange Format (LDIF) files.
Important
To help improve the performance for authentication requests, the FTP service caches the credentials for successful logins for 15 minutes by default. This means that if you change the password in your AD LDS server, this change may not be reflected for the cache duration. To alleviate this, you can disable credential caching for the FTP service. To do so, use the following steps:
- Open a command prompt.
- Type the following commands:
cd /d "%SystemRoot%\System32\Inetsrv" Appcmd.exe set config -section:system.ftpServer/caching /credentialsCache.enabled:"False" /commit:apphost Net stop FTPSVC Net start FTPSVC
- Close the command prompt.
Step 1: Set up the Project Environment
In this step, you will create a project in Visual Studio 2008 for the demo provider.
- Open Microsoft Visual Studio 2008.
- Click the File menu, then New, then Project.
- In the New Projectdialog box:
- Choose Visual C# as the project type.
- Choose Class Library as the template.
- Type FtpLdapAuthentication as the name of the project.
- Click OK.
- When the project opens, add a reference path to the FTP extensibility library:
- Click Project, and then click FtpLdapAuthentication Properties.
- Click the Reference Paths tab.
- Enter the path to the FTP extensibility assembly for your version of Windows, where C: is your operating system drive.
- For Windows Server 2008 and Windows Vista:
- C:\Windows\assembly\GAC_MSIL\Microsoft.Web.FtpServer\7.5.0.0__31bf3856ad364e35
- For 32-bit Windows 7 and Windows Server 2008 R2:
- C:\Program Files\Reference Assemblies\Microsoft\IIS
- For 64-bit Windows 7 and Windows Server 2008 R2:
- C:\Program Files (x86)\Reference Assemblies\Microsoft\IIS
- For Windows Server 2008 and Windows Vista:
- Click Add Folder.
- Add a strong name key to the project:
- Click Project, and then click FtpLdapAuthentication Properties.
- Click the Signing tab.
- Check the Sign the assembly check box.
- Choose <New...> from the strong key name drop-down box.
- Enter FtpLdapAuthenticationKey for the key file name.
- If desired, enter a password for the key file; otherwise, clear the Protect my key file with a password check box.
- Click OK.
- Note: FTP 7.5 Extensibility does not support the .NET Framework 4.0; if you are using Visual Studio 2010, or you have changed your default framework version, you may need to change the framework version. To do so, use the following steps:
- Click Project, and then click FtpLdapAuthentication Properties.
- Click the Application tab.
- Choose .NET Framework 3.5 in the Target framework drop-down menu.
- Save, close, and re-open the project.
- Optional: You can add a custom build event to add the DLL automatically to the Global Assembly Cache (GAC) on your development computer:
- Click Project, and then click FtpLdapAuthentication Properties.
- Click the Build Events tab.
- Enter the appropriate commands in the Post-build event command linedialog box, depending on your version of Visual Studio:
- If you are using Visual Studio 2010:
net stop ftpsvc
call "%VS100COMNTOOLS%\vsvars32.bat">null
gacutil.exe /if "$(TargetPath)"
net start ftpsvc - If you are using Visual Studio 2008:
net stop ftpsvc
call "%VS90COMNTOOLS%\vsvars32.bat">null
gacutil.exe /if "$(TargetPath)"
net start ftpsvc
- If you are using Visual Studio 2010:
- Save the project.
Step 2: Create the Extensibility Class
In this step, you will implement the authentication and role extensibility interfaces for the demo provider.
- Add the necessary references to the project:
- Click Project, and then click Add Reference...
- On the .NET tab, click Microsoft.Web.FtpServer.
- Click OK.
- Repeat the above steps to add the following references to the project:
- System.Configuration
- System.DirectoryServices
- System.DirectoryServices.AccountManagement
- Add the code for the authentication class:
- In Solution Explorer, double-click the Class1.cs file.
- Remove the existing code.
- Paste the following code into the editor:
using System; using System.Collections.Specialized; using System.Configuration.Provider; using System.DirectoryServices; using System.DirectoryServices.AccountManagement; using Microsoft.Web.FtpServer; public class FtpLdapAuthentication : BaseProvider, IFtpAuthenticationProvider, IFtpRoleProvider { private static string _ldapServer = string.Empty; private static string _ldapPartition = string.Empty; private static string _ldapAdminUsername = string.Empty; private static string _ldapAdminPassword = string.Empty; // Override the default initialization method. protected override void Initialize(StringDictionary config) { // Retrieve the provider settings from configuration. _ldapServer = config["ldapServer"]; _ldapPartition = config["ldapPartition"]; _ldapAdminUsername = config["ldapAdminUsername"]; _ldapAdminPassword = config["ldapAdminPassword"]; // Test for the LDAP server name (Required). if (string.IsNullOrEmpty(_ldapServer) || string.IsNullOrEmpty(_ldapPartition)) { throw new ArgumentException( "Missing LDAP server values in configuration."); } } public bool AuthenticateUser( string sessionId, string siteName, string userName, string userPassword, out string canonicalUserName) { canonicalUserName = userName; // Attempt to look up the user and password. return LookupUser(true, userName, string.Empty, userPassword); } public bool IsUserInRole( string sessionId, string siteName, string userName, string userRole) { // Attempt to look up the user and role. return LookupUser(false, userName, userRole, string.Empty); } private static bool LookupUser( bool isUserLookup, string userName, string userRole, string userPassword) { PrincipalContext _ldapPrincipalContext = null; DirectoryEntry _ldapDirectoryEntry = null; try { // Create the context object using the LDAP connection information. _ldapPrincipalContext = new PrincipalContext( ContextType.ApplicationDirectory, _ldapServer, _ldapPartition, ContextOptions.SimpleBind, _ldapAdminUsername, _ldapAdminPassword); // Test for LDAP credentials. if (string.IsNullOrEmpty(_ldapAdminUsername) || string.IsNullOrEmpty(_ldapAdminPassword)) { // If LDAP credentials do not exist, attempt to create an unauthenticated directory entry object. _ldapDirectoryEntry = new DirectoryEntry("LDAP://" + _ldapServer + "/" + _ldapPartition); } else { // If LDAP credentials exist, attempt to create an authenticated directory entry object. _ldapDirectoryEntry = new DirectoryEntry("LDAP://" + _ldapServer + "/" + _ldapPartition, _ldapAdminUsername, _ldapAdminPassword, AuthenticationTypes.Secure); } // Create a DirectorySearcher object from the cached DirectoryEntry object. DirectorySearcher userSearcher = new DirectorySearcher(_ldapDirectoryEntry); // Specify the the directory searcher to filter by the user name. userSearcher.Filter = String.Format("(&(objectClass=user)(cn={0}))", userName); // Specify the search scope. userSearcher.SearchScope = SearchScope.Subtree; // Specify the directory properties to load. userSearcher.PropertiesToLoad.Add("distinguishedName"); // Specify the search timeout. userSearcher.ServerTimeLimit = new TimeSpan(0, 1, 0); // Retrieve a single search result. SearchResult userResult = userSearcher.FindOne(); // Test if no result was found. if (userResult == null) { // Return false if no matching user was found. return false; } else { if (isUserLookup == true) { try { // Attempt to validate credentials using the username and password. return _ldapPrincipalContext.ValidateCredentials(userName, userPassword, ContextOptions.SimpleBind); } catch (Exception ex) { // Throw an exception if an error occurs. throw new ProviderException(ex.Message); } } else { // Retrieve the distinguishedName for the user account. string distinguishedName = userResult.Properties["distinguishedName"][0].ToString(); // Create a DirectorySearcher object from the cached DirectoryEntry object. DirectorySearcher groupSearcher = new DirectorySearcher(_ldapDirectoryEntry); // Specify the the directory searcher to filter by the group/role name. groupSearcher.Filter = String.Format("(&(objectClass=group)(cn={0}))", userRole); // Specify the search scope. groupSearcher.SearchScope = SearchScope.Subtree; // Specify the directory properties to load. groupSearcher.PropertiesToLoad.Add("member"); // Specify the search timeout. groupSearcher.ServerTimeLimit = new TimeSpan(0, 1, 0); // Retrieve a single search result. SearchResult groupResult = groupSearcher.FindOne(); // Loop through the member collection. for (int i = 0; i < groupResult.Properties["member"].Count; ++i) { string member = groupResult.Properties["member"][i].ToString(); // Test if the current member contains the user's distinguished name. if (member.IndexOf(distinguishedName, StringComparison.OrdinalIgnoreCase) > -1) { // Return true (role lookup succeeded) if the user is found. return true; } } // Return false (role lookup failed) if the user is not found for the role. return false; } } } catch (Exception ex) { // Throw an exception if an error occurs. throw new ProviderException(ex.Message); } } }
- Save and compile the project.
Note: If you did not use the optional steps to register the assemblies in the GAC, you will need to manually copy the assemblies to your IIS 7 computer and add the assemblies to the GAC using the Gacutil.exe tool. For more information, see the following topic on the Microsoft MSDN Web site:
Step 3: Add the Demo Provider to FTP
In this step, you will add your provider to the list of providers for your FTP service, configure your provider for your LDAP server, and enable your provider to authenticate users for an FTP site.
Adding your Provider to FTP
- Determine the assembly information for your extensibility provider:
- In Windows Explorer, open your "C:\Windows\assembly" path, where C: is your operating system drive.
- Locate the FtpLdapAuthentication assembly.
- Right-click the assembly, and then click Properties.
- Copy the Culture value; for example: Neutral.
- Copy the Version number; for example: 1.0.0.0.
- Copy the Public Key Token value; for example: 426f62526f636b73.
- Click Cancel.
- Add the extensibility provider to the global list of FTP authentication providers:
- Open the Internet Information Services (IIS) Manager.
- Click your computer name in the Connections pane.
- Double-click FTP Authentication in the main window.
- Click Custom Providers... in the Actions pane.
- Click Register.
- Enter FtpLdapAuthentication for the provider Name.
- Click Managed Provider (.NET).
- Enter the assembly information for the extensibility provider using the information that you copied earlier. For example:
FtpLdapAuthentication,FtpLdapAuthentication,version=1.0.0.0,Culture=neutral,PublicKeyToken=426f62526f636b73 - Click OK.
- Clear the FtpLdapAuthentication check box in the providers list.
- Click OK.
Configuring your Provider's Settings
- Determine the connection information for your LDAP server; there are four pieces of information that you will need to know in order to configure the extensibility provider to talk to your LDAP server:
- Server Name and TCP/IP Port: This is the name (or IP address) of the server that is hosting your LDAP service; the port is usually 389. These will be added to your provider using the "SERVERNAME:PORT" syntax.
- LDAP Partition: This is the LDAP path within your LDAP service to your data, for example: "CN=ServerName,DC=DomainName,DC=DomainExtension."
- LDAP Username: This is a username that has access to your LDAP server; this is not the name of an account that you will use for FTP access, and it does not have to be a Windows account.
- LDAP Password: This is the password that is associated with the LDAP username.
- Using the information from the previous steps, configure the options for the provider:
- At the moment there is no user interface that enables you to add properties for a custom authentication module, so you will have to use the following command line. You will need to update the highlighted areas with the information from the previous steps and the information for your LDAP server:
cd %SystemRoot%\System32\Inetsrv
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpLdapAuthentication']" /commit:apphost
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpLdapAuthentication'].[key='ldapServer',value='MYSERVER:389']" /commit:apphost
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpLdapAuthentication'].[key='ldapPartition',value='CN=MyServer,DC=MyDomain,DC=local']" /commit:apphost
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpLdapAuthentication'].[key='ldapAdminUsername',encryptedValue='MyAdmin']" /commit:apphost
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpLdapAuthentication'].[key='ldapAdminPassword',encryptedValue='MyPassword1']" /commit:apphost - Note: The highlighted areas are the values for the ldapServer, ldapPartition, ldapAdminUsername, and ldapAdminPassword settings, which configure your network environment for your LDAP server.
- At the moment there is no user interface that enables you to add properties for a custom authentication module, so you will have to use the following command line. You will need to update the highlighted areas with the information from the previous steps and the information for your LDAP server:
Enabling your Provider for an FTP site
- Add the custom authentication provider for an FTP site:
- Open an FTP site in the Internet Information Services (IIS) Manager.
- Double-click FTP Authentication in the main window.
- Click Custom Providers... in the Actions pane.
- Check FtpLdapAuthentication in the providers list.
- Click OK.
- Add an authorization rule for the authentication provider:
- Double-click FTP Authorization Rules in the main window.
- Click Add Allow Rule... in the Actions pane.
- You can add either of the following authorization rules:
- For a specific user:
- Select Specified users for the access option.
- Enter a user name that you created in your AD LDS partition.
- For a role or group:
- Select Specified roles or user groups for the access option.
- Enter the role or group name that you created in your AD LDS partition.
- Select Read and/or Write for the Permissions option.
- For a specific user:
- Click OK.
Summary
In this blog I showed you how to:
- Create a project in Visual Studio 2010 or Visual Studio 2008 for a custom FTP authentication provider.
- Implement the extensibility interface for custom FTP authentication.
- Add a custom authentication provider to your FTP service.
When users connect to your FTP site, the FTP service will attempt to authenticate users from your LDAP server by using your custom authentication provider.
Additional Information
The PrincipalContext.ValidateCredentials() method will validate the user name in the userName parameter with the value of the userPrincipalName attribute of the user object in AD LDS. Because of this, the userPrincipalName attribute for a user object is expected to match the name of the user account that an FTP client will use to log in, which will should be the same value as the cn attribute for the user object. Therefore, when you create a user object in AD LDS, you will need to set the corresponding userPrincipalName attribute for the user object. In addition, when you create a user object in AD LDS, the msDS-UserAccountDisabled attribute is set to TRUE by default, so you will need to change the value of that attribute to FALSE before you attempt to log in.
For more information, see my follow-up blog that is titled FTP and LDAP - Part 2: How to Set Up an Active Directory Lightweight Directory Services (AD LDS) Server.
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
The Days Grow Shorter...
15 September 2011 • by Bob • Ponderings
Back in the 1980s I was a big fan of the Canadian Power Trio named "Triumph." As far as arena rock was concerned, few bands could put on a show that was anywhere near as entertaining as a Triumph concert. It wasn't just about being a fan - there are any number of great bands out there who could put on a good show if you already liked them; but Triumph put on a killer show whether you liked them or not.
At the height of their popularity, Triumph recorded what was to become one of their greatest hits, which was a song that was titled "Fight the Good Fight." Many guitar players - myself included - spent a good deal of time learning that song, and I always enjoyed playing it live in the various rock bands that I played in throughout my teenage years.
As the first official day of Autumn is just around the corner here in Seattle, the opening lines to "Fight the Good Fight" seem to take on special meaning:
"The days grow shorter,
And the nights are getting long.
Feels like we're running out of time."
As I look out of my office window, that's exactly what I see:
Our short-lived Pacific Northwest Summer appears to have come to a close, and the clouds seem like they're here for the duration. The sun is setting a little earlier each day, and within a few months the choleric combination of miserable mists and depressing dusk will shorten the average day to six hours or less of daylight. And yet the most discouraging fact that I have to wrestle with today is the knowledge that the weather will be this way for the next nine months.
[I exhale a deep sigh...] ![]()
Three months from now is the Winter Solstice, at which time we will confront the shortest day of the year; after that, we will at least have the small consolation that each day will be a little longer than the last, but we still won't see much of the sun until sometime next June or July.
[I heave another deep sigh...] ![]()
I wonder how much a plane ticket to Hawaii would cost in January? ![]()
Sometimes I Make My Day...
08 September 2011 • by Bob • Scripting
This past weekend I was writing a quick piece of Windows Script Host (WSH) code to clean up some files on one of my servers, and I had populated a Scripting.Dictionary object with a bunch of string data that I was going to write to a log file. Obviously it's much easier to read through the log file if the data is sorted, but the Scripting.Dictionary object does not have a built-in Sort() method.
With this in mind, I set out to write a sorting function for my script, when I decided that it would might be more efficient to see if someone out in the community had already written such a function. I quickly discovered that someone had - and it turns out, that particular someone was me!
Way back in 1999 I published Microsoft Knowledge Base (KB) article 246067, which was titled "Sorting a Scripting Dictionary Populated with String Data." This KB article contained the following code, which took care of everything for me:
Const dictKey = 1 Const dictItem = 2 Function SortDictionary(objDict,intSort) ' declare our variables Dim strDict() Dim objKey Dim strKey,strItem Dim X,Y,Z ' get the dictionary count Z = objDict.Count ' we need more than one item to warrant sorting If Z > 1 Then ' create an array to store dictionary information ReDim strDict(Z,2) X = 0 ' populate the string array For Each objKey In objDict strDict(X,dictKey) = CStr(objKey) strDict(X,dictItem) = CStr(objDict(objKey)) X = X + 1 Next ' perform a a shell sort of the string array For X = 0 to (Z - 2) For Y = X to (Z - 1) If StrComp(strDict(X,intSort),strDict(Y,intSort),vbTextCompare) > 0 Then strKey = strDict(X,dictKey) strItem = strDict(X,dictItem) strDict(X,dictKey) = strDict(Y,dictKey) strDict(X,dictItem) = strDict(Y,dictItem) strDict(Y,dictKey) = strKey strDict(Y,dictItem) = strItem End If Next Next ' erase the contents of the dictionary object objDict.RemoveAll ' repopulate the dictionary with the sorted information For X = 0 to (Z - 1) objDict.Add strDict(X,dictKey), strDict(X,dictItem) Next End If End Function
Sometimes I make my day.
I Must Have Grown Up at Some Point, but I Don't Remember When
22 August 2011 • by Bob • Ponderings
My middle daughter turned 24 last week. This was a significant occasion by itself, but it was made even more significant because I had just walked her down the aisle only three weeks earlier when she married a great guy from Vancouver, BC.
It seems like only yesterday that I was teaching her how to brush her teeth, how to ride a bicycle, and how to write an English paper that didn't sound like she was talking to one of her friends on the telephone.
Momentous events like these will often motivate you sit back and wonder where the time went. It's been nearly thirty years since I became a "legal adult," but I still don't feel like I'm a "grown up." I still want to believe that my dad is the grown-up and I am just some long-haired kid from Arizona.
But it's easy for me to do the math - in a few short years my oldest daughter will turn thirty, so I must have grown up at some point; I just can't remember when.
![]()
IIS 6: Setting up SSL - Appendix C: Processing a Certificate Request using Windows 2003 Certificate Services
03 August 2011 • by Bob • IIS, SSL
In this last appendix for my blog series about using SSL with IIS 6, I'll discuss processing a certificate request by using Windows 2003 Certificate Services. When you are running a certificate server for your network environment, you will need to physically issue the certificates that clients will request from your certificate server. There is a way that you can configure certificate services to automatically issue certificates, but I'd advise against that, unless you are only issuing certificates for testing purposes. If so, then you should read the Set the default action upon receipt of a certificate request topic on Microsoft's TechNet website.
That being said, the procedure to approve and issue a certificate is relatively easy; to do so, use the following steps:
- Open the "Certificate Authority" administrative tool:
- Click on "Pending Requests":
- Right-click the pending request and choose "All Tasks", then click "Issue":
- The certificate will now show up under "Issued Certificates":
That wraps up the last post in this blog series about using Secure Sockets Layer (SSL) with IIS 6.0, as well as some related information about using Windows 2003 Certificate Services. I hope this information helps administrators that have yet to upgrade to Windows Server 2008 or Windows Server 2008 R2. ;-]
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
IIS 6: Setting up SSL - Appendix B: Obtaining a Root Certificate from Windows Server 2003 Certificate Services
29 July 2011 • by Bob • IIS, SSL
In this second appendix for my blog series about using SSL with IIS 6, I'm going to discuss obtaining the root certificate from Windows Server 2003 Certificate Services. By way of explanation, obtaining a root certificate is one of the most important steps for servers or clients that will use certificates that you issue. While this step is not necessary on the server where you installed Certificate Services, it is absolutely essential on your other servers or clients, because this step will allow those computers to trust your certificate server as a Certificate Authority (CA). Without that trust in place, you will either receive error messages or SSL simply won't work.
I've broken this process into two steps:
Downloading the Root Certificate
- Browse to your certificate server's address, (e.g. http://<server-name>/certsrv/), and choose to retrieve the CA certificate:
- Click the link to download the CA certificate:
- Choose to save the certificate file to disk:

- Save the file to your desktop:
Note: If you were to bring up the properties for the root certificate, the certificate's icon should show an error; this is because the certificate has not been imported.
Installing the Root Certificate
Before using any certificates that you issue on a computer, you need to install the Root Certificate. (This includes web servers and clients.)
- Double-click the file on your desktop:

- Click the "Install Certificate" button:
- Click "Next" to start the Certificate Import Wizard:
- Choose to automatically choose the store:
- Click the "Finish" button:
- Click "Yes" when asked if you want to add the certificate: NOTE: This step is very important. If you do not see this dialog, something went wrong, and you may need to manually place the certificate in the correct store.
- Click "OK" when informed that the import was successful.

Note: If you were to bring up the properties for the root certificate after you have installed it on your computer, you should see that the icon for the certificate no longer shows an error.
That's it for this post. In my next blog post, I'll discuss processing a certificate request.
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
IIS 6: Setting up SSL - Appendix A: Installing Windows Server 2003 Certificate Services
28 July 2011 • by Bob • IIS, SSL
I needed to take a short break from my blog series about using SSL with IIS 6 in order to work on some other projects, but I wanted to finish the series by giving you a few appendices that give you some additional details that you might want to know if you are using SSL with IIS 6.
In this first appendix, I'll discuss how to install Certificate Services for Windows Server 2003. Installing Certificate Services will allow you to have your own Certificate Authority (CA), and thereby you will be able to issue certificates for your organization. It should be noted that Internet clients that are not part of your organization will not inherently trust your certificates - you will need to export your Root CA certificate, which I will describe in a later appendix for this blog series.
There are four different configurations that you can choose from when you are installing Certificate Services:
| Enterprise root CA | Integrated with Active Directory Acts as the root CA for your organization |
|---|---|
| Enterprise subordinate CA | Integrated with Active Directory Child of your organization's root CA |
| Stand-alone root CA | Not integrated with Active Directory Acts as the root CA for your certificate chain |
| Stand-alone subordinate CA | Not integrated with Active Directory Child of your certificate chain's root CA |
Note: More information about these options is available at http://technet.microsoft.com/en-us/library/cc756989.aspx
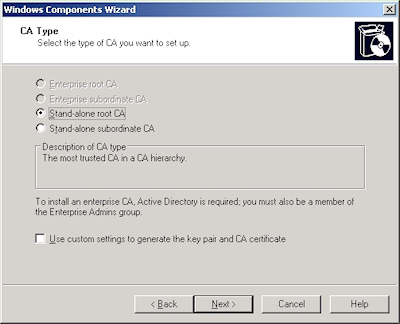
For this blog, I will discuss setting up a Stand-alone root CA.
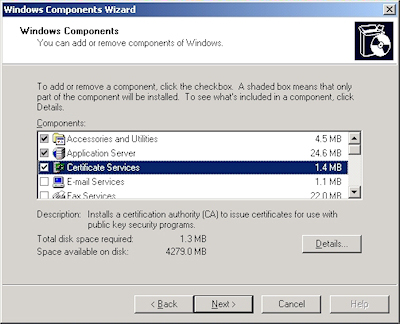
- Run the "Windows Component Wizard" in "Add/Remove Programs", choose "Certificate Services", and click "Next":
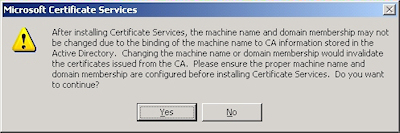
- Click "Yes" when prompted to continue:
- Accept the defaults, then click "Next":
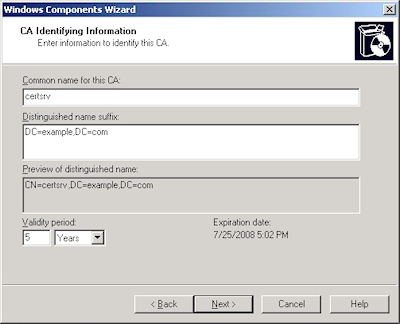
- Enter all requested information, then click "Next":
- Accept the defaults for the data locations and click "Next":
- The wizard will step through installing the services:
- When the wizard has completed, click "Finish" to exit the wizard:
That wraps up this blog post. In my next post I'll discuss obtaining the root certificate for your certificate server so you can install it on a client computer or an IIS server; this will allow other computers to trust the certificates that you issue.
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
Dogs Versus Cats
20 July 2011 • by Bob • Humor
I freely admit that I am a "Dog Person." What's more, I am blessed to have married another dog person - we both love dogs, and this is generally a good thing. My wife grew up surrounded by dogs, as did I.
My wife and I spent the first ten years of our marriage in poverty or in the military, and unfortunately being in the military is a lot like being in poverty. ![]() Just the same, we had been married ten years before the two of us were finally able to get a dog. Our first dog was a yellow Labrador Retriever named "Barney." Unfortunately, Barney had been mistreated by a previous owner and we were not able to keep him.
Just the same, we had been married ten years before the two of us were finally able to get a dog. Our first dog was a yellow Labrador Retriever named "Barney." Unfortunately, Barney had been mistreated by a previous owner and we were not able to keep him.
Our next dog was wonderful - we got a Bouvier des Flandres, who became a part of our family for the next eleven years. We named him "Ruff Waldo Emerson," which we shortened to Emerson. I had never owned a herding dog before, and it was a lot of fun to watch the way that he took care of our family: he would patiently wait by the door for the kids to arrive home safely from school, and he would try to push me out of my desk chair when he decided that it was time for me to go to bed.
Our most recent dog was a red-haired Golden Retriever, who our son named "Rook." (Our son, Peter, was heavily into chess at the time.) Rook was a great dog, and I now see why so many people love Golden Retrievers. Sadly, Rook died of a fast-acting bone cancer when he was just eight years old. ![]()
All of this is simply an introduction in order to offer proof that I am a dog lover. But that being said, I am decidedly not a "Cat Person." I am allergic to cats, which I think is God's way of saying that man isn't meant to coexist with cats. My daughter has a cat, and her cat seems to like me more than anyone else that comes to visit - which seems to be due to the fact that I ignore it.
Here are several of my thoughts on dogs versus cats:
- Dogs have masters, cats have servants.
- When stranded in an avalanche, no one looks for a cat to rescue them.
- Who cares if cats kill mice? Why not just raise mice and skip a step? My friend has cats which drag live mice into the house - ostensibly to kill them - but eventually the cats lose the mice somewhere inside the house.
- Dogs are faithful and loyal; cats are selfish and fickle.
- If you pet a dog, the dog thinks, "Wow - he likes me; he's so wonderful." If you pet a cat, the cat thinks, "Wow - he likes me; I'm so wonderful."
- No one takes a cat hiking.
- Dogs can be trained to search for explosives, provide eyesight for the blind, haul loaded sleds across hundreds of miles of hostile terrain, sense a variety of medical conditions, guide herds of animals without supervision, and a host of other important tasks. Cats can be trained to poop in a box.
The debate over which is better – dogs or cats - is ages old, and not likely to ever be resolved. But in my estimation, dogs will always be man's best friend, while cats will remain - at best - frenemies.
How to Create an Authentication Provider for FTP 7.5 using BlogEngine.NET's XML Membership Files
30 June 2011 • by Bob • FTP, BlogEngine.NET, Extensibility
I ran into an interesting situation recently with BlogEngine.NET that I thought would make a good blog post.
Here's the background for the environment: I host several blog sites for friends of mine, and they BlogEngine.NET for their blogging engine. From a security perspective this works great for me, because I can give them accounts for blogging that are kept in the XML files for each of their respective blogs that aren't real user accounts on my Windows servers.
The problem that I ran into: BlogEngine.NET has great support for uploading files to your blog, but it doesn't provide a real way to manage the files that have been uploaded. So when one of my friends mentioned that they wanted to update one of their files, I was left in a momentary quandary.
My solution: I realized that I could write a custom FTP provider that would solve all of my needs. For my situation the provider needed to do three things:
- The provider needed to perform username/password validation.
- The provider needed to perform role lookups.
- The provider needed to return a custom home directory.
Here's why item #3 was so important - my users have no idea about the underlying functionality for their blog, so I didn't want to simply enable FTP publishing for their website and give them access to their ASP.NET files - there's no telling what might happen. Since all of their files are kept in the path ~/App_Data/files, it made sense to have the custom FTP provider return home directories for each of their websites that point to their files instead of the root folders of their websites.
Prerequisites
The following items are required to complete the steps in this blog:
- The following version of IIS must be installed on your Windows server, and the Internet Information Services (IIS) Manager must also be installed:
- IIS 7.0 must be installed on Windows Server 2008
- IIS 7.5 must be installed on Windows Server 2008 R2
- The FTP 7.5 service must be installed. To install FTP 7.5, follow the instructions in the following topic:
- You must have FTP publishing enabled for a site. To create a new FTP site, follow the instructions in the following topic:
Step 1: Set up the Project Environment
Note: I used Visual Studio 2008 when I created my custom provider and wrote the steps that appear in this blog, although since then I have upgraded to Visual Studio 2010, and I have successfully recompiled my provider using that version. In any event, the steps should be similar whether you are using Visual Studio 2008 or Visual Studio 2010.;-]
In this step, you will create a project inVisual Studio 2008for the demo provider.
- Open MicrosoftVisual Studio 2008.
- Click the File menu, then New, then Project.
- In the New Projectdialog box:
- Choose Visual C# as the project type.
- Choose Class Library as the template.
- Type FtpBlogEngineNetAuthentication as the name of the project.
- Click OK.
- When the project opens, add a reference path to the FTP extensibility library:
- Click Project, and then click FtpBlogEngineNetAuthentication Properties.
- Click the Reference Paths tab.
- Enter the path to the FTP extensibility assembly for your version of Windows, where C: is your operating system drive.
- For Windows Server 2008 and Windows Vista:
- C:\Windows\assembly\GAC_MSIL\Microsoft.Web.FtpServer\7.5.0.0__31bf3856ad364e35
- For Windows Server 2008 R2 and Windows 7:
- C:\Program Files\Reference Assemblies\Microsoft\IIS
- For Windows Server 2008 and Windows Vista:
- Click Add Folder.
- Add a strong name key to the project:
- Click Project, and then click FtpBlogEngineNetAuthentication Properties.
- Click the Signing tab.
- Check the Sign the assembly check box.
- Choose <New...> from the strong key name drop-down box.
- Enter FtpBlogEngineNetAuthenticationKey for the key file name.
- If desired, enter a password for the key file; otherwise, clear the Protect my key file with a password check box.
- Click OK.
- Optional: You can add a custom build event to add the DLL automatically to the Global Assembly Cache (GAC) on your development computer:
- Click Project, and then click FtpBlogEngineNetAuthentication Properties.
- Click the Build Events tab.
- Enter the following in the Post-build event command linedialog box for your version of Visual Studio:
- If you have Visual Studio 2008:
net stop ftpsvc call "%VS90COMNTOOLS%\vsvars32.bat">nul gacutil.exe /if "$(TargetPath)" net start ftpsvc
- If you have Visual Studio 2010:
net stop ftpsvc call "%VS100COMNTOOLS%\vsvars32.bat">nul gacutil.exe /if "$(TargetPath)" net start ftpsvc
- If you have Visual Studio 2008:
- Save the project.
Step 2: Create the Extensibility Class
In this step, you will implement the logging extensibility interface for the demo provider.
- Add the necessary references to the project:
- Click Project, and then click Add Reference...
- On the .NET tab, click Microsoft.Web.FtpServer.
Note: If Microsoft.Web.FtpServer does not show up on the .NETtab, then use the following steps:- Click the Browse tab.
- Navigate to the reference path where Microsoft.Web.FtpServer.dll is located. (See the paths that were listed earlier in Step #1 for the location.)
- Highlight Microsoft.Web.FtpServer.dll.
- Click OK.
- Repeat the above steps to add the following reference to the project:
- System.Configuration
- Add the code for the authentication class:
- In Solution Explorer, double-click the Class1.cs file.
- Remove the existing code.
- Paste the following code into the editor:
using System; using System.Collections.Specialized; using System.Collections.Generic; using System.Configuration.Provider; using System.IO; using System.Security.Cryptography; using System.Text; using System.Xml; using System.Xml.XPath; using Microsoft.Web.FtpServer; public class FtpBlogEngineNetAuthentication : BaseProvider, IFtpAuthenticationProvider, IFtpRoleProvider, IFtpHomeDirectoryProvider { // Create strings to store the paths to the XML files that store the user and role data. private string _xmlUsersFileName; private string _xmlRolesFileName; // Create a string to store the FTP home directory path. private string _ftpHomeDirectory; // Create a file system watcher object for change notifications. private FileSystemWatcher _xmlFileWatch; // Create a dictionary to hold user data. private Dictionary<string, XmlUserData> _XmlUserData = new Dictionary<string, XmlUserData>( StringComparer.InvariantCultureIgnoreCase); // Override the Initialize method to retrieve the configuration settings. protected override void Initialize(StringDictionary config) { // Retrieve the paths from the configuration dictionary. _xmlUsersFileName = config[@"xmlUsersFileName"]; _xmlRolesFileName = config[@"xmlRolesFileName"]; _ftpHomeDirectory = config[@"ftpHomeDirectory"]; // Test if the path to the users or roles XML file is empty. if ((string.IsNullOrEmpty(_xmlUsersFileName)) || (string.IsNullOrEmpty(_xmlRolesFileName))) { // Throw an exception if the path is missing or empty. throw new ArgumentException(@"Missing xmlUsersFileName or xmlRolesFileName value in configuration."); } else { // Test if the XML files exist. if ((File.Exists(_xmlUsersFileName) == false) || (File.Exists(_xmlRolesFileName) == false)) { // Throw an exception if the file does not exist. throw new ArgumentException(@"The specified XML file does not exist."); } } try { // Create a file system watcher object for the XML file. _xmlFileWatch = new FileSystemWatcher(); // Specify the folder that contains the XML file to watch. _xmlFileWatch.Path = _xmlUsersFileName.Substring(0, _xmlUsersFileName.LastIndexOf(@"\")); // Filter events based on the XML file name. _xmlFileWatch.Filter = @"*.xml"; // Filter change notifications based on last write time and file size. _xmlFileWatch.NotifyFilter = NotifyFilters.LastWrite | NotifyFilters.Size; // Add the event handler. _xmlFileWatch.Changed += new FileSystemEventHandler(this.XmlFileChanged); // Enable change notification events. _xmlFileWatch.EnableRaisingEvents = true; } catch (Exception ex) { // Raise an exception if an error occurs. throw new ProviderException(ex.Message,ex.InnerException); } } // Define the event handler for changes to the XML files. public void XmlFileChanged(object sender, FileSystemEventArgs e) { // Verify that the changed file is one of the XML data files. if ((e.FullPath.Equals(_xmlUsersFileName, StringComparison.OrdinalIgnoreCase)) || (e.FullPath.Equals(_xmlRolesFileName, StringComparison.OrdinalIgnoreCase))) { // Clear the contents of the existing user dictionary. _XmlUserData.Clear(); // Repopulate the user dictionary. ReadXmlDataStore(); } } // Override the Dispose method to dispose of objects. protected override void Dispose(bool IsDisposing) { if (IsDisposing) { _xmlFileWatch.Dispose(); _XmlUserData.Clear(); } } // Define the AuthenticateUser method. bool IFtpAuthenticationProvider.AuthenticateUser( string sessionId, string siteName, string userName, string userPassword, out string canonicalUserName) { // Define the canonical user name. canonicalUserName = userName; // Validate that the user name and password are not empty. if (String.IsNullOrEmpty(userName) || String.IsNullOrEmpty(userPassword)) { // Return false (authentication failed) if either are empty. return false; } else { try { // Retrieve the user/role data from the XML file. ReadXmlDataStore(); // Create a user object. XmlUserData user = null; // Test if the user name is in the dictionary of users. if (_XmlUserData.TryGetValue(userName, out user)) { // Retrieve a sequence of bytes for the password. var passwordBytes = Encoding.UTF8.GetBytes(userPassword); // Retrieve a SHA256 object. using (HashAlgorithm sha256 = new SHA256Managed()) { // Hash the password. sha256.TransformFinalBlock(passwordBytes, 0, passwordBytes.Length); // Convert the hashed password to a Base64 string. string passwordHash = Convert.ToBase64String(sha256.Hash); // Perform a case-insensitive comparison on the password hashes. if (String.Compare(user.Password, passwordHash, true) == 0) { // Return true (authentication succeeded) if the hashed passwords match. return true; } } } } catch (Exception ex) { // Raise an exception if an error occurs. throw new ProviderException(ex.Message,ex.InnerException); } } // Return false (authentication failed) if authentication fails to this point. return false; } // Define the IsUserInRole method. bool IFtpRoleProvider.IsUserInRole( string sessionId, string siteName, string userName, string userRole) { // Validate that the user and role names are not empty. if (String.IsNullOrEmpty(userName) || String.IsNullOrEmpty(userRole)) { // Return false (role lookup failed) if either are empty. return false; } else { try { // Retrieve the user/role data from the XML file. ReadXmlDataStore(); // Create a user object. XmlUserData user = null; // Test if the user name is in the dictionary of users. if (_XmlUserData.TryGetValue(userName, out user)) { // Search for the role in the list. string roleFound = user.Roles.Find(item => item == userRole); // Return true (role lookup succeeded) if the role lookup was successful. if (!String.IsNullOrEmpty(roleFound)) return true; } } catch (Exception ex) { // Raise an exception if an error occurs. throw new ProviderException(ex.Message,ex.InnerException); } } // Return false (role lookup failed) if role lookup fails to this point. return false; } // Define the GetUserHomeDirectoryData method. public string GetUserHomeDirectoryData(string sessionId, string siteName, string userName) { // Test if the path to the home directory is empty. if (string.IsNullOrEmpty(_ftpHomeDirectory)) { // Throw an exception if the path is missing or empty. throw new ArgumentException(@"Missing ftpHomeDirectory value in configuration."); } // Return the path to the home directory. return _ftpHomeDirectory; } // Retrieve the user/role data from the XML files. private void ReadXmlDataStore() { // Lock the provider while the data is retrieved. lock (this) { try { // Test if the dictionary already has data. if (_XmlUserData.Count == 0) { // Create an XML document object and load the user data XML file XPathDocument xmlUsersDocument = GetXPathDocument(_xmlUsersFileName); // Create a navigator object to navigate through the XML file. XPathNavigator xmlNavigator = xmlUsersDocument.CreateNavigator(); // Loop through the users in the XML file. foreach (XPathNavigator userNode in xmlNavigator.Select("/Users/User")) { // Retrieve a user name. string userName = GetInnerText(userNode, @"UserName"); // Retrieve the user's password. string password = GetInnerText(userNode, @"Password"); // Test if the data is empty. if ((String.IsNullOrEmpty(userName) == false) && (String.IsNullOrEmpty(password) == false)) { // Create a user data class. XmlUserData userData = new XmlUserData(password); // Store the user data in the dictionary. _XmlUserData.Add(userName, userData); } } // Create an XML document object and load the role data XML file XPathDocument xmlRolesDocument = GetXPathDocument(_xmlRolesFileName); // Create a navigator object to navigate through the XML file. xmlNavigator = xmlRolesDocument.CreateNavigator(); // Loop through the roles in the XML file. foreach (XPathNavigator roleNode in xmlNavigator.Select(@"/roles/role")) { // Retrieve a role name. string roleName = GetInnerText(roleNode, @"name"); // Loop through the users for the role. foreach (XPathNavigator userNode in roleNode.Select(@"users/user")) { // Retrieve a user name. string userName = userNode.Value; // Create a user object. XmlUserData user = null; // Test if the user name is in the dictionary of users. if (_XmlUserData.TryGetValue(userName, out user)) { // Add the role name for the user. user.Roles.Add(roleName); } } } } } catch (Exception ex) { // Raise an exception if an error occurs. throw new ProviderException(ex.Message,ex.InnerException); } } } // Retrieve an XPathDocument object from a file path. private static XPathDocument GetXPathDocument(string path) { Exception _ex = null; // Specify number of attempts to create an XPathDocument. for (int i = 0; i < 8; ++i) { try { // Create an XPathDocument object and load the user data XML file XPathDocument xPathDocument = new XPathDocument(path); // Return the XPathDocument if successful. return xPathDocument; } catch (Exception ex) { // Save the exception for later. _ex = ex; // Pause for a brief interval. System.Threading.Thread.Sleep(250); } } // Throw the last exception if the function fails to this point. throw new ProviderException(_ex.Message,_ex.InnerException); } // Retrieve data from an XML element. private static string GetInnerText(XPathNavigator xmlNode, string xmlElement) { string xmlText = string.Empty; try { // Test if the XML element exists. if (xmlNode.SelectSingleNode(xmlElement) != null) { // Retrieve the text in the XML element. xmlText = xmlNode.SelectSingleNode(xmlElement).Value.ToString(); } } catch (Exception ex) { // Raise an exception if an error occurs. throw new ProviderException(ex.Message,ex.InnerException); } // Return the element text. return xmlText; } } // Define the user data class. internal class XmlUserData { // Create a private string to hold a user's password. private string _password = string.Empty; // Create a private string array to hold a user's roles. private List<String> _roles = null; // Define the class constructor requiring a user's password. public XmlUserData(string Password) { this.Password = Password; this.Roles = new List<String>(); } // Define the password property. public string Password { get { return _password; } set { try { _password = value; } catch (Exception ex) { throw new ProviderException(ex.Message,ex.InnerException); } } } // Define the roles property. public List<String> Roles { get { return _roles; } set { try { _roles = value; } catch (Exception ex) { throw new ProviderException(ex.Message,ex.InnerException); } } } }
- Save and compile the project.
Note: If you did not use the optional steps to register the assemblies in the GAC, you will need to manually copy the assemblies to your IIS 7 computer and add the assemblies to the GAC using the Gacutil.exe tool. For more information, see the following topic on the Microsoft MSDN Web site:
Step 3: Add the custom FTP provider to IIS
In this step, you will add the provider to your FTP service. These steps obviously assume that you are using BlogEngine.NET on your Default Web Site, but these steps can be easily amended for any other website where BlogEngine.NET is installed.
- Determine the assembly information for the extensibility provider:
- In Windows Explorer, open your "C:\Windows\assembly" path, where C: is your operating system drive.
- Locate the FtpBlogEngineNetAuthentication assembly.
- Right-click the assembly, and then click Properties.
- Copy the Culture value; for example: Neutral.
- Copy the Version number; for example: 1.0.0.0.
- Copy the Public Key Token value; for example: 426f62526f636b73.
- Click Cancel.
- Using the information from the previous steps, add the extensibility provider to the global list of FTP providers and configure the options for the provider:
- At the moment there is no user interface that enables you to add properties for a custom authentication module, so you will have to use the following command line:
cd %SystemRoot%\System32\Inetsrv
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"[name='FtpBlogEngineNetAuthentication',type='FtpBlogEngineNetAuthentication,FtpBlogEngineNetAuthentication,version=1.0.0.0,Culture=neutral,PublicKeyToken=426f62526f636b73']" /commit:apphost
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpBlogEngineNetAuthentication']" /commit:apphost
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpBlogEngineNetAuthentication'].[key='xmlUsersFileName',value='C:\inetpub\wwwroot\App_Data\Users.xml']" /commit:apphost
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpBlogEngineNetAuthentication'].[key='xmlRolesFileName',value='C:\inetpub\wwwroot\App_Data\Roles.xml']" /commit:apphost
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpBlogEngineNetAuthentication'].[key='ftpHomeDirectory',value='C:\inetpub\wwwroot\App_Data\files']" /commit:apphost - Note: You will need to update the values for the xmlUsersFileName, xmlRolesFileName, and ftpHomeDirectory settings for your environment.
- At the moment there is no user interface that enables you to add properties for a custom authentication module, so you will have to use the following command line:
Step 4: Use the Custom Authentication Provider with your BlogEngine.NET Website
Just like the steps that I listed earlier, these steps assume that you are using BlogEngine.NET on your Default Web Site, but these steps can be easily amended for any other website where BlogEngine.NET is installed.
Add FTP publishing to your BlogEngine.NET website
- In the IIS 7 Manager, in the Connections pane, expand the Sites node in the tree, then highlight the Default Web Site.
- Click Add FTP Publishing in the Actions pane.
- When the Add FTP Site Publishingwizard appears:
- Choose an IP address for your FTP site from the IP Address drop-down, or choose to accept the default selection of "All Unassigned."
- Accept the default port of 21 for the FTP site, or enter a custom TCP/IP port in the Port box.
- Click Next.
- Do no choose any authentication or authorization options for now; you will set those later.
- Click Finish.
- Hit F5 to refresh the view in IIS 7 Manager.
Specify the custom authentication provider for your BlogEngine.NET website
- Double-click FTP Authentication in the main window for your website.
- Click Custom Providers... in the Actions pane.
- Check FtpBlogEngineNetAuthentication in the providers list.
- Click OK.
Add authorization rules for the authentication provider
- Double-click FTP Authorization Rules in the main window for your website.
- Click Add Allow Rule... in the Actions pane.
- You can add either of the following authorization rules:
- For a specific user from your BlogEngine.NET website:
- Select Specified users for the access option.
- Enter a user name that you created in your BlogEngine.NET website.
- For a role or group from your BlogEngine.NET website:
- Select Specified roles or user groups for the access option.
- Enter the role or group name that you created in your BlogEngine.NET website.
- Select Read and/or Write for the Permissions option.
- For a specific user from your BlogEngine.NET website:
- Click OK.
Specify a custom home directory provider for your BlogEngine.NET website
At the moment there is no user interface that enables you to add custom home directory providers, so you will have to use the following command line:
cd %SystemRoot%\System32\Inetsrv
appcmd.exe set config -section:system.applicationHost/sites /+"[name='Default Web Site'].ftpServer.customFeatures.providers.[name='FtpBlogEngineNetAuthentication']" /commit:apphost
appcmd.exe set config -section:system.applicationHost/sites /"[name='Default Web Site'].ftpServer.userIsolation.mode:Custom" /commit:apphost
Additional Information
To help improve the performance for authentication requests, the FTP service caches the credentials for successful logins for 15 minutes by default. This means that if you change your passwords, this change may not be reflected for the cache duration. To alleviate this, you can disable credential caching for the FTP service. To do so, use the following steps:
- Open a command prompt.
- Type the following commands:
cd /d "%SystemRoot%\System32\Inetsrv" Appcmd.exe set config -section:system.ftpServer/caching /credentialsCache.enabled:"False" /commit:apphost Net stop FTPSVC Net start FTPSVC
- Close the command prompt.
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/