FTP Clients - Part 10: FTP Voyager
21 October 2011 • by Bob • FTP
For this installment in my series about FTP Clients, I'd like to take a look at FTP Voyager from Rhino Software. For this blog I used FTP Voyager 15.2.0.17, and it is available from the following URL:
FTP Voyager is a great FTP client that supports a wide array of features and connection options, but I shouldn't get ahead of myself and talk about everything in my introduction. ;-]
At the time of this blog post, FTP Voyager is a for-retail product that is available in two different versions:
- FTP Voyager
- FTP Voyager Secure
You should take a look at the FTP Voyager Versions page for a description of the features that are available in each version.
FTP Voyager Overview
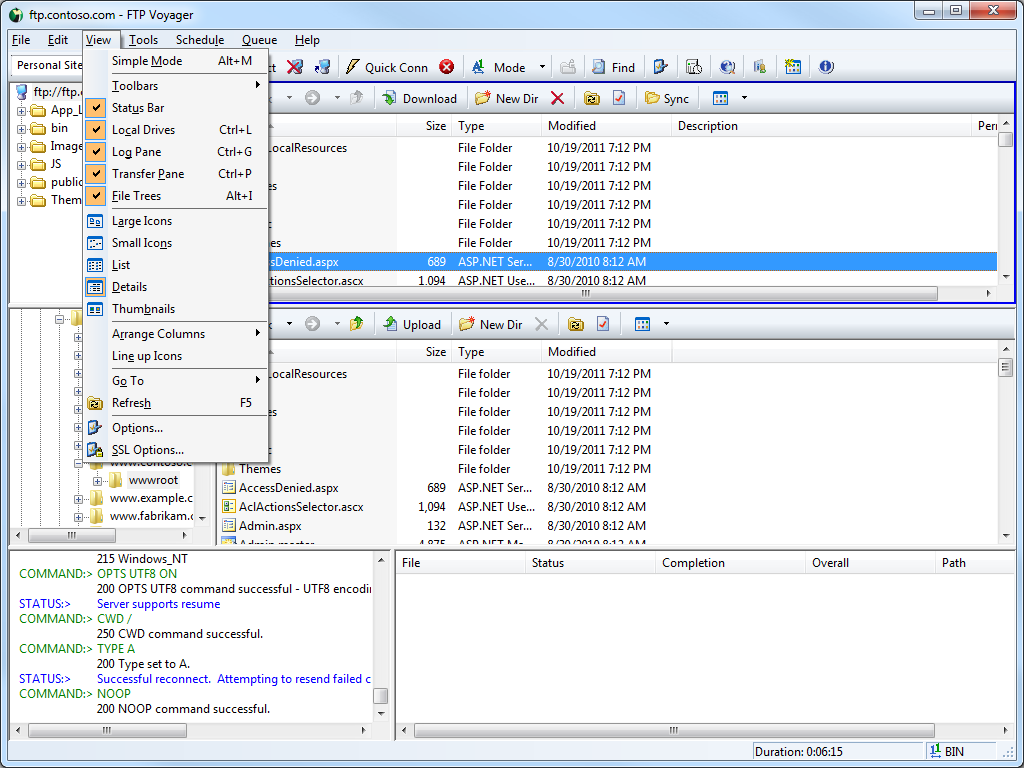
The FTP Voyager user interface is uncluttered, easy to understand, and allows you to customize which panes you want to see displayed.
If you want a really uncluttered display, FTP Voyager offers a Simple Mode, which narrows down the number of panes that are displayed. (Sometimes this is a handy feature to have.)
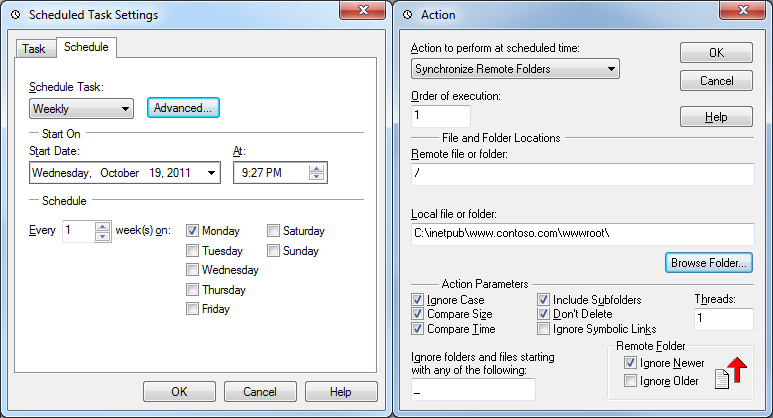
FTP Voyager doesn't have a command-line interface, but it has web browser integration; and it has a really cool scheduler, which allows you to configure FTP jobs to run at scheduled times.
FTP Voyager also supports sending custom FTP commands, and it has an extensibility interface for creating add-ons. I didn't experiment with creating any add-ons, but you can find details about creating your own add-ons through RhinoSoft's FTP Voyager Add-Ons page.
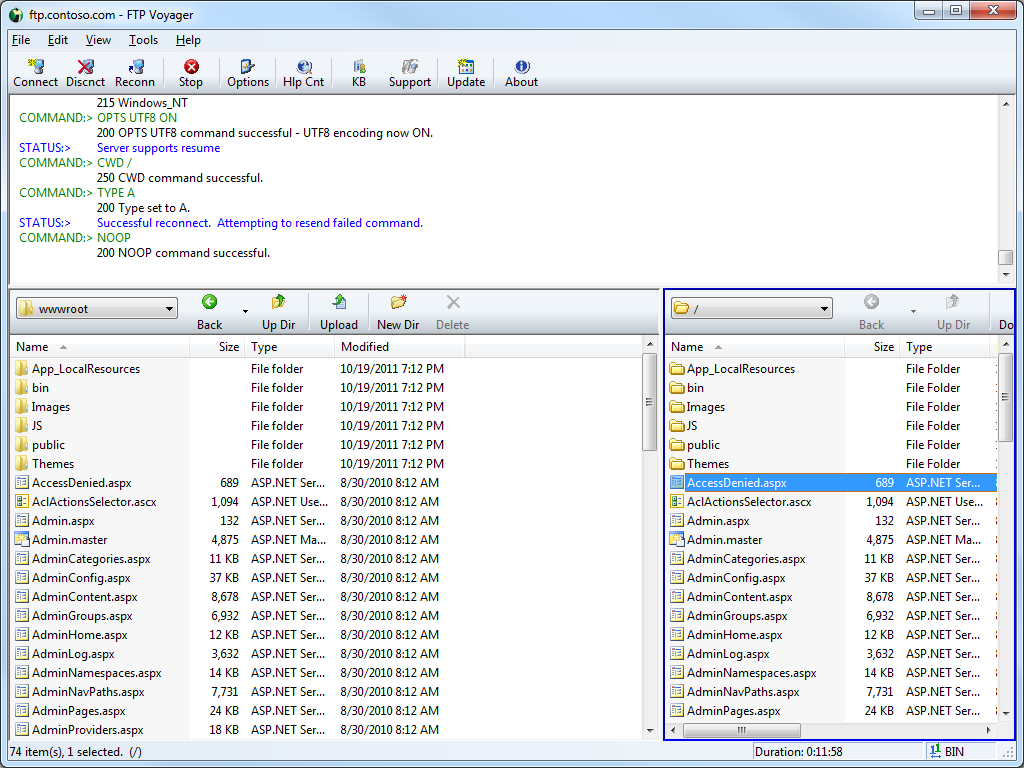
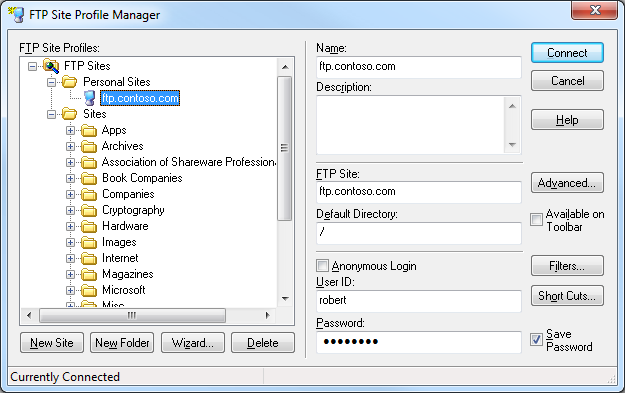
FTP connections are created and edited through FTP Voyager's Site Profile Manager, which is comparable to the site management features that I have found in many of the better GUI-based FTP clients.
That concludes my summary for some of the general features - so now we'll take a look at the FTP7-specific features that I've discussed in my other FTP client blog posts.
Using FTP Voyager with FTP over SSL (FTPS)
FTP Voyager supports both Implicit and Explicit FTPS, so the choice is up to you to decide which method to use. As I have mentioned in my previous blogs, the FTPS method in FTP7 is specified by the port number that you choose when you are creating your bindings. Once again, I realize that I have posted the following information in almost all of my posts in this FTP client series, but it needs to be mentioned that the following rules apply for FTP7 when determining whether you are using Implicit or Explicit FTPS:
- If you enable SSL in FTP7 and you assign the FTP site to port 990, you are using Implicit FTPS.
- If you enable SSL in FTP7 and you assign the FTP site to any port other than port 990, you are using Explicit FTPS.
To configure the security options for a connection in FTP Voyager, you need to open the Advanced Settings dialog for the connection in FTP Voyager's Site Profile Manager.
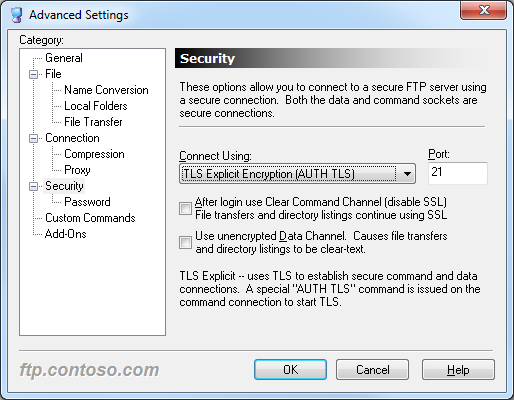 |
| Fig. 6 - FTP Voyager's Security Options |
The additional security options in FTP Voyager's Security Options allow you to configure the SSL environment to match FTP7's Advanced SSL Policy settings.
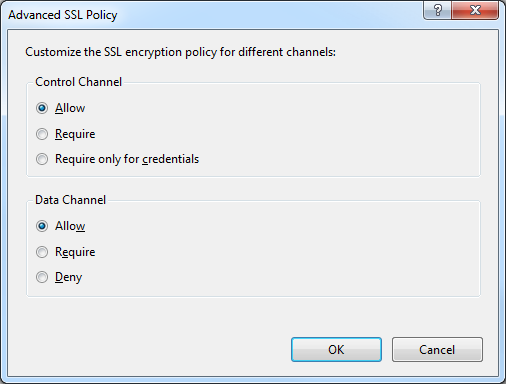 |
| Fig. 7 - FTP7's Advanced SSL Policy Settings |
Note: I was able to use FTP Voyager's FTPS features with FTP7's virtual host names, but I should mention that I had to configure a Global Listener FTP Site in order to get that to work.
Using FTP Voyager with True FTP Hosts
FTP Voyager has built-in for the HOST command, so you can use true FTP host names when using FTP Voyager to connect to FTP7 sites that are configured with host names. This feature is enabled by default, but if you needed to disable it for some reason, that feature can be accessed through FTP Voyager's Advanced Settings dialog.
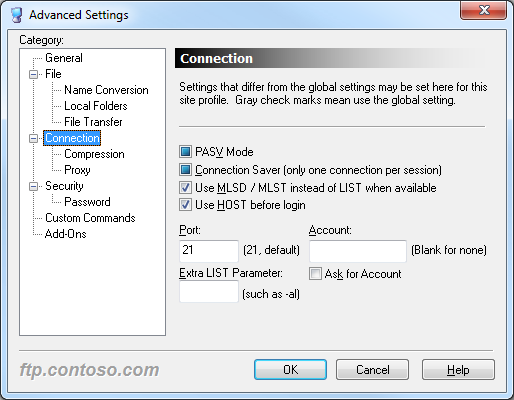 |
| Fig. 7 - FTP Voyager's Advanced Connection Settings |
The following excerpt from the Log Pane of an FTP Voyager session shows the HOST command in action:
STATUS:> |
Connecting to "ftp.contoso.com" on port 21. |
|
220 Microsoft FTP Service |
STATUS:> |
Connected. Logging into the server |
COMMAND:> |
HOST ftp.contoso.com |
|
220 Host accepted. |
COMMAND:> |
USER robert |
|
331 Password required for robert. |
COMMAND:> |
PASS ********** |
|
230 User logged in. |
STATUS:> |
Login successful |
Using FTP Voyager with FTP Virtual Host Names
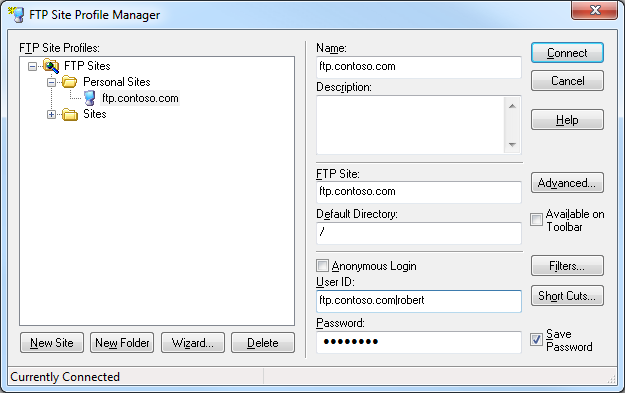
FTP Voyager's login settings allow you to specify the virtual host name as part of the user credentials by using syntax like "ftp.example.com|username" or "ftp.example.com\username", but since FTP Voyager allows you to use true FTP hosts this is really a moot point. Just the same, there's nothing to stop you from disabling the HOST command for a connection and specifying an FTP virtual host as part of your username, although I'm not sure why you would want to do that.
Scorecard for FTP Voyager
This concludes our quick look at some of the FTP features that are available with FTP Voyager, and here are the scorecard results:
| Client Name | Directory Browsing | Explicit FTPS | Implicit FTPS | Virtual Hosts | True HOSTs | Site Manager | Extensibility |
|---|---|---|---|---|---|---|---|
| Rich | Y | Y | Y | Y | Y | Y | |
| As noted earlier, FTP Voyager supports the FTP HOST command, and is enabled by default for new connections. | |||||||
In closing, FTP Voyager is a great GUI-based FTP client that has first-class support for all of the features that I have been examining in detail throughout my FTP client blog series. But that being said, I included the following disclaimer in all of my preceding posts, so this post will be no exception: there are a great number of additional features that FTP Voyager provides - but once again I only focused on a few specific topic areas that apply to FTP7. ;-]
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
Sending WebDAV Requests in .NET Revisited
18 October 2011 • by Bob • WebDAV
I recently spoke with a great customer in India, and he was experimenting with the code from my Sending WebDAV Requests in .NET blog post. He had a need to send the WebDAV LOCK/UNLOCK commands, so I wrote a quick addition to the code in my original blog post to send those commands, and I thought that I'd share that code in an updated blog post.
Using WebDAV Locks
First of all, you may need to enable WebDAV locks on your server. To do so, follow the instructions in the following walkthrough:
How to Use WebDAV Locks
http://learn.iis.net/page.aspx/596/how-to-use-webdav-locks/
If you were writing a WebDAV client, sending the LOCK/UNLOCK commands would help to avoid two clients attempting to author the same resource. So if your WebDAV client was editing a file named "foo.txt", the flow of events would be something like the following:
- LOCK foo.txt
- GET foo.txt
- [make some changes to foo.txt]
- PUT foo.txt
- UNLOCK foo.txt
Description for the Sample Application
The updated code sample in this blog post shows how to send most of the common WebDAV requests using C# and common .NET libraries. In addition to adding the LOCK/UNLOCK commands to this version, I also changed the sample files to upload/download Classic ASP pages instead of text files; I did this so you can see that the WebDAV requests are correctly accessing the source code of the ASP pages instead of the translated output.
Having said that, I need to mention once again that I create more objects than are necessary for each section of the sample, which creates several intentional redundancies; I did this because I wanted to make each section somewhat self-sufficient, which helps you to copy and paste a little easier. I present the WebDAV methods the in the following order:
| WebDAV Method | Notes |
|---|---|
| PUT | This section of the sample writes a string as a text file to the destination server as "foobar1.asp". Sending a raw string is only one way of writing data to the server, in a more common scenario you would probably open a file using a steam object and write it to the destination. One thing to note in this section of the sample is the addition of the "Overwrite" header, which specifies that the destination file can be overwritten. |
| LOCK | This section of the sample sends a WebDAV request to lock the "foobar1.asp" before downloading it with a GET request. |
| GET | This section of the sample sends a WebDAV-specific form of the HTTP GET method to retrieve the source code for the destination URL. This is accomplished by sending the "Translate: F" header and value, which instructs IIS to send the source code instead of the processed URL. In this specific sample I am using Classic ASP, but if the requests were for ASP.NET or PHP files you would also need to specify the "Translate: F" header/value pair. |
| PUT | This section of the sample sends an updated version of the "foobar1.asp" script to the server, which overwrites the original file. The purpose of this PUT command is to simulate creating a WebDAV client that can update files on the server. |
| GET | This section of the sample retrieves the updated version of the "foobar1.asp" script from the server, just to show that the updated version was saved successfully. |
| UNLOCK | This section of the sample uses the lock token from the earlier LOCK request to unlock the "foobar1.asp" |
| COPY | This section of the sample copies the file from "foobar1.asp" to "foobar2.asp", and uses the "Overwrite" header to specify that the destination file can be overwritten. One thing to note in this section of the sample is the addition of the "Destination" header, which obviously specifies the destination URL. The value for this header can be a relative path or an FQDN, but it may not be an FQDN to a different server. |
| MOVE | This section of the sample moves the file from "foobar2.asp" to "foobar1.asp", thereby replacing the original uploaded file. As with the previous two sections of the sample, this section of the sample uses the "Overwrite" and "Destination" headers. |
| DELETE | This section of the sample deletes the original file, thereby removing the sample file from the destination server. |
| MKCOL | This section of the sample creates a folder named "foobar3" on the destination server; as far as WebDAV on IIS is concerned, the MKCOL method is a lot like the old DOS MKDIR command. |
| DELETE | This section of the sample deletes the folder from the destination server. |
Source Code for the Sample Application
Here is the source code for the updated sample application:
using System; using System.Net; using System.IO; using System.Text; class WebDavTest { static void Main(string[] args) { try { // Define the URLs. string szURL1 = @"http://localhost/foobar1.asp"; string szURL2 = @"http://localhost/foobar2.asp"; string szURL3 = @"http://localhost/foobar3"; // Some sample code to put in an ASP file. string szAspCode1 = @"<%=Year()%>"; string szAspCode2 = @"<%=Time()%>"; // Some XML to put in a lock request. string szLockXml = "<?xml version=\"1.0\" encoding=\"utf-8\" ?>" + "<D:lockinfo xmlns:D='DAV:'>" + "<D:lockscope><D:exclusive/></D:lockscope>" + "<D:locktype><D:write/></D:locktype>" + "<D:owner><D:href>mailto:someone@example.com</D:href></D:owner>" + "</D:lockinfo>"; // Define username, password, and lock token strings. string szUsername = @"username"; string szPassword = @"password"; string szLockToken = null; // --------------- PUT REQUEST #1 --------------- // // Create an HTTP request for the URL. HttpWebRequest httpPutRequest1 = (HttpWebRequest)WebRequest.Create(szURL1); // Set up new credentials. httpPutRequest1.Credentials = new NetworkCredential(szUsername, szPassword); // Pre-authenticate the request. httpPutRequest1.PreAuthenticate = true; // Define the HTTP method. httpPutRequest1.Method = @"PUT"; // Specify that overwriting the destination is allowed. httpPutRequest1.Headers.Add(@"Overwrite", @"T"); // Specify the content length. httpPutRequest1.ContentLength = szAspCode1.Length; // Optional, but allows for larger files. httpPutRequest1.SendChunked = true; // Retrieve the request stream. Stream putRequestStream1 = httpPutRequest1.GetRequestStream(); // Write the string to the destination as text bytes. putRequestStream1.Write( Encoding.UTF8.GetBytes((string)szAspCode1), 0, szAspCode1.Length); // Close the request stream. putRequestStream1.Close(); // Retrieve the response. HttpWebResponse httpPutResponse1 = (HttpWebResponse)httpPutRequest1.GetResponse(); // Write the response status to the console. Console.WriteLine(@"PUT Response #1: {0}", httpPutResponse1.StatusDescription); // --------------- LOCK REQUEST --------------- // // Create an HTTP request for the URL. HttpWebRequest httpLockRequest = (HttpWebRequest)WebRequest.Create(szURL1); // Set up new credentials. httpLockRequest.Credentials = new NetworkCredential(szUsername, szPassword); // Pre-authenticate the request. httpLockRequest.PreAuthenticate = true; // Define the HTTP method. httpLockRequest.Method = @"LOCK"; // Specify the request timeout. httpLockRequest.Headers.Add(@"Timeout", "Infinite"); // Specify the request content type. httpLockRequest.ContentType = "text/xml; charset=\"utf-8\""; // Retrieve the request stream. Stream lockRequestStream = httpLockRequest.GetRequestStream(); // Write the lock XML to the destination. lockRequestStream.Write( Encoding.UTF8.GetBytes((string)szLockXml), 0, szLockXml.Length); // Close the request stream. lockRequestStream.Close(); // Retrieve the response. HttpWebResponse httpLockResponse = (HttpWebResponse)httpLockRequest.GetResponse(); // Retrieve the lock token for the request. szLockToken = httpLockResponse.GetResponseHeader("Lock-Token"); // Write the response status to the console. Console.WriteLine( @"LOCK Response: {0}", httpLockResponse.StatusDescription); Console.WriteLine( @" LOCK Token: {0}", szLockToken); // --------------- GET REQUEST #1 --------------- // // Create an HTTP request for the URL. HttpWebRequest httpGetRequest1 = (HttpWebRequest)WebRequest.Create(szURL1); // Set up new credentials. httpGetRequest1.Credentials = new NetworkCredential(szUsername, szPassword); // Pre-authenticate the request. httpGetRequest1.PreAuthenticate = true; // Define the HTTP method. httpGetRequest1.Method = @"GET"; // Specify the request for source code. httpGetRequest1.Headers.Add(@"Translate", "F"); // Retrieve the response. HttpWebResponse httpGetResponse1 = (HttpWebResponse)httpGetRequest1.GetResponse(); // Retrieve the response stream. Stream getResponseStream1 = httpGetResponse1.GetResponseStream(); // Create a stream reader for the response. StreamReader getStreamReader1 = new StreamReader(getResponseStream1, Encoding.UTF8); // Write the response status to the console. Console.WriteLine( @"GET Response #1: {0}", httpGetResponse1.StatusDescription); Console.WriteLine( @" Response Length: {0}", httpGetResponse1.ContentLength); Console.WriteLine( @" Response Text: {0}", getStreamReader1.ReadToEnd()); // Close the response streams. getStreamReader1.Close(); getResponseStream1.Close(); // --------------- PUT REQUEST #2 --------------- // // Create an HTTP request for the URL. HttpWebRequest httpPutRequest2 = (HttpWebRequest)WebRequest.Create(szURL1); // Set up new credentials. httpPutRequest2.Credentials = new NetworkCredential(szUsername, szPassword); // Pre-authenticate the request. httpPutRequest2.PreAuthenticate = true; // Define the HTTP method. httpPutRequest2.Method = @"PUT"; // Specify that overwriting the destination is allowed. httpPutRequest2.Headers.Add(@"Overwrite", @"T"); // Specify the lock token. httpPutRequest2.Headers.Add(@"If", String.Format(@"({0})",szLockToken)); // Specify the content length. httpPutRequest2.ContentLength = szAspCode1.Length; // Optional, but allows for larger files. httpPutRequest2.SendChunked = true; // Retrieve the request stream. Stream putRequestStream2 = httpPutRequest2.GetRequestStream(); // Write the string to the destination as a text file. putRequestStream2.Write( Encoding.UTF8.GetBytes((string)szAspCode2), 0, szAspCode1.Length); // Close the request stream. putRequestStream2.Close(); // Retrieve the response. HttpWebResponse httpPutResponse2 = (HttpWebResponse)httpPutRequest2.GetResponse(); // Write the response status to the console. Console.WriteLine(@"PUT Response #2: {0}", httpPutResponse2.StatusDescription); // --------------- GET REQUEST #2 --------------- // // Create an HTTP request for the URL. HttpWebRequest httpGetRequest2 = (HttpWebRequest)WebRequest.Create(szURL1); // Set up new credentials. httpGetRequest2.Credentials = new NetworkCredential(szUsername, szPassword); // Pre-authenticate the request. httpGetRequest2.PreAuthenticate = true; // Define the HTTP method. httpGetRequest2.Method = @"GET"; // Specify the request for source code. httpGetRequest2.Headers.Add(@"Translate", "F"); // Retrieve the response. HttpWebResponse httpGetResponse2 = (HttpWebResponse)httpGetRequest2.GetResponse(); // Retrieve the response stream. Stream getResponseStream2 = httpGetResponse2.GetResponseStream(); // Create a stream reader for the response. StreamReader getStreamReader2 = new StreamReader(getResponseStream2, Encoding.UTF8); // Write the response status to the console. Console.WriteLine( @"GET Response #2: {0}", httpGetResponse2.StatusDescription); Console.WriteLine( @" Response Length: {0}", httpGetResponse2.ContentLength); Console.WriteLine( @" Response Text: {0}", getStreamReader2.ReadToEnd()); // Close the response streams. getStreamReader2.Close(); getResponseStream2.Close(); // --------------- UNLOCK REQUEST --------------- // // Create an HTTP request for the URL. HttpWebRequest httpUnlockRequest = (HttpWebRequest)WebRequest.Create(szURL1); // Set up new credentials. httpUnlockRequest.Credentials = new NetworkCredential(szUsername, szPassword); // Pre-authenticate the request. httpUnlockRequest.PreAuthenticate = true; // Define the HTTP method. httpUnlockRequest.Method = @"UNLOCK"; // Specify the lock token. httpUnlockRequest.Headers.Add(@"Lock-Token", szLockToken); // Retrieve the response. HttpWebResponse httpUnlockResponse = (HttpWebResponse)httpUnlockRequest.GetResponse(); // Write the response status to the console. Console.WriteLine( @"UNLOCK Response: {0}", httpUnlockResponse.StatusDescription); // --------------- COPY REQUEST --------------- // // Create an HTTP request for the URL. HttpWebRequest httpCopyRequest = (HttpWebRequest)WebRequest.Create(szURL1); // Set up new credentials. httpCopyRequest.Credentials = new NetworkCredential(szUsername, szPassword); // Pre-authenticate the request. httpCopyRequest.PreAuthenticate = true; // Define the HTTP method. httpCopyRequest.Method = @"COPY"; // Specify the destination URL. httpCopyRequest.Headers.Add(@"Destination", szURL2); // Specify that overwriting the destination is allowed. httpCopyRequest.Headers.Add(@"Overwrite", @"T"); // Retrieve the response. HttpWebResponse httpCopyResponse = (HttpWebResponse)httpCopyRequest.GetResponse(); // Write the response status to the console. Console.WriteLine(@"COPY Response: {0}", httpCopyResponse.StatusDescription); // --------------- MOVE REQUEST --------------- // // Create an HTTP request for the URL. HttpWebRequest httpMoveRequest = (HttpWebRequest)WebRequest.Create(szURL2); // Set up new credentials. httpMoveRequest.Credentials = new NetworkCredential(szUsername, szPassword); // Pre-authenticate the request. httpMoveRequest.PreAuthenticate = true; // Define the HTTP method. httpMoveRequest.Method = @"MOVE"; // Specify the destination URL. httpMoveRequest.Headers.Add(@"Destination", szURL1); // Specify that overwriting the destination is allowed. httpMoveRequest.Headers.Add(@"Overwrite", @"T"); // Retrieve the response. HttpWebResponse httpMoveResponse = (HttpWebResponse)httpMoveRequest.GetResponse(); // Write the response status to the console. Console.WriteLine(@"MOVE Response: {0}", httpMoveResponse.StatusDescription); // --------------- DELETE FILE REQUEST --------------- // // Create an HTTP request for the URL. HttpWebRequest httpDeleteFileRequest = (HttpWebRequest)WebRequest.Create(szURL1); // Set up new credentials. httpDeleteFileRequest.Credentials = new NetworkCredential(szUsername, szPassword); // Pre-authenticate the request. httpDeleteFileRequest.PreAuthenticate = true; // Define the HTTP method. httpDeleteFileRequest.Method = @"DELETE"; // Retrieve the response. HttpWebResponse httpDeleteFileResponse = (HttpWebResponse)httpDeleteFileRequest.GetResponse(); // Write the response status to the console. Console.WriteLine(@"DELETE File Response: {0}", httpDeleteFileResponse.StatusDescription); // --------------- MKCOL REQUEST --------------- // // Create an HTTP request for the URL. HttpWebRequest httpMkColRequest = (HttpWebRequest)WebRequest.Create(szURL3); // Set up new credentials. httpMkColRequest.Credentials = new NetworkCredential(szUsername, szPassword); // Pre-authenticate the request. httpMkColRequest.PreAuthenticate = true; // Define the HTTP method. httpMkColRequest.Method = @"MKCOL"; // Retrieve the response. HttpWebResponse httpMkColResponse = (HttpWebResponse)httpMkColRequest.GetResponse(); // Write the response status to the console. Console.WriteLine(@"MKCOL Response: {0}", httpMkColResponse.StatusDescription); // --------------- DELETE FOLDER REQUEST --------------- // // Create an HTTP request for the URL. HttpWebRequest httpDeleteFolderRequest = (HttpWebRequest)WebRequest.Create(szURL3); // Set up new credentials. httpDeleteFolderRequest.Credentials = new NetworkCredential(szUsername, szPassword); // Pre-authenticate the request. httpDeleteFolderRequest.PreAuthenticate = true; // Define the HTTP method. httpDeleteFolderRequest.Method = @"DELETE"; // Retrieve the response. HttpWebResponse httpDeleteFolderResponse = (HttpWebResponse)httpDeleteFolderRequest.GetResponse(); // Write the response status to the console. Console.WriteLine(@"DELETE Folder Response: {0}", httpDeleteFolderResponse.StatusDescription); } catch (Exception ex) { Console.WriteLine(ex.Message); } } }
Running the Sample Application
When you run the code sample, if there are no errors you should see something like the following output:
If you looked at the IIS logs after running the sample application, you should see entries like the following example:
#Software: Microsoft Internet Information Services 7.5
#Version: 1.0
#Date: 2011-10-18 06:49:07
#Fields: date time s-ip cs-method cs-uri-stem cs-uri-query s-port cs-username c-ip sc-status sc-substatus sc-win32-status
2011-10-18 06:49:07 ::1 PUT /foobar1.asp - 80 - ::1 401 2 5
2011-10-18 06:49:07 ::1 PUT /foobar1.asp - 80 username ::1 201 0 0
2011-10-18 06:49:07 ::1 LOCK /foobar1.asp - 80 username ::1 200 0 0
2011-10-18 06:49:07 ::1 GET /foobar1.asp - 80 username ::1 200 0 0
2011-10-18 06:49:07 ::1 PUT /foobar1.asp - 80 username ::1 204 0 0
2011-10-18 06:49:07 ::1 GET /foobar1.asp - 80 username ::1 200 0 0
2011-10-18 06:49:07 ::1 UNLOCK /foobar1.asp - 80 username ::1 204 0 0
2011-10-18 06:49:07 ::1 COPY /foobar1.asp http://localhost/foobar2.asp 80 username ::1 201 0 0
2011-10-18 06:49:07 ::1 MOVE /foobar2.asp http://localhost/foobar1.asp 80 username ::1 204 0 0
2011-10-18 06:49:07 ::1 DELETE /foobar1.asp - 80 username ::1 200 0 0
2011-10-18 06:49:07 ::1 MKCOL /foobar3 - 80 username ::1 201 0 0
2011-10-18 06:49:07 ::1 DELETE /foobar3 - 80 username ::1 200 0 0
Closing Notes
Since the code sample cleans up after itself, you should not see any files or folders on the destination server when it has completed executing. To see the files and folders that are actually created and deleted on the destination server, you would need to step through the code in a debugger.
This updated version does not include examples of the WebDAV PROPPATCH/PROPFIND methods in this sample for the same reason that I did not do so in my previous blog - those commands require processing the XML responses, and that is outside the scope of what I wanted to do with this sample.
I hope this helps!
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
How to create an HTML Application to configure your WebDAV Redirector settings
07 October 2011 • by Bob • IIS, Scripting, WebDAV
I've mentioned in previous blog posts that I use the Windows WebDAV Redirector a lot. (And believe me, I use it a lot.) Having said that, there are a lot of registry settings that control how the Windows WebDAV Redirector operates, and I tend to tweak those settings fairly often.
I documented all of those registry settings in my Using the WebDAV Redirector walkthrough, but unfortunately there isn't a built-in interface for managing the settings. With that in mind, I decided to write my own user interface.
I knew that it would be pretty simple to create a basic Windows Form application that does everything, but my trouble is that I would want to share the code in a blog, and the steps create a Windows application are probably more than I would want to write in such a short space. So I decided to reach into my scripting past and create an HTML Application for Windows that configures all of the Windows WebDAV Redirector settings.
It should be noted, like everything else these days, that this code is provided as-is. ;-]
Using the HTML Application
When you run the application, it will present you with the following user interface, which allows you to configure most of the useful Windows WebDAV Redirector settings:
Creating the HTML Application
To create this HTML Application, save the following HTMLA code as "WebDAV Redirector Settings.hta" to your computer, and then double-click its icon to run the application.
<html> <head> <title>WebDAV Redirector Settings</title> <HTA:APPLICATION APPLICATIONNAME="WebDAV Redirector Settings" ID="WebDAV Redirector Settings" VERSION="1.0" BORDER="dialog" BORDERSTYLE="static" INNERBORDER="no" SYSMENU="no" MAXIMIZEBUTTON="no" MINIMIZEBUTTON="no" SCROLL="no" SCROLLFLAT="yes" SINGLEINSTANCE="yes" CONTEXTMENU="no" SELECTION="no"/> <script language="vbscript"> ' ---------------------------------------- ' Start of main code section. ' ---------------------------------------- Option Explicit Const intDialogWidth = 700 Const intDialogHeight = 620 Const HKEY_LOCAL_MACHINE = &H80000002 Const strWebClientKeyPath = "SYSTEM\CurrentControlSet\Services\WebClient\Parameters" Const strLuaKeyPath = "Software\Microsoft\Windows\CurrentVersion\Policies\System" Dim objRegistry Dim blnHasChanges ' ---------------------------------------- ' Start the application. ' ---------------------------------------- Sub Window_OnLoad On Error Resume Next ' Set up the UI dimensions. Self.resizeTo intDialogWidth,intDialogHeight Self.moveTo (Screen.AvailWidth - intDialogWidth) / 2, _ (Screen.AvailHeight - intDialogHeight) / 2 ' Retrieve the current settings. Document.all.TheBody.ClassName = "hide" Set objRegistry = GetObject( _ "winmgmts:{impersonationLevel=impersonate}!\\.\root\default:StdRegProv") Call CheckForLUA() Call GetValues() Document.All.TheBody.ClassName = "show" End Sub ' ---------------------------------------- ' Check for User Access Control ' ---------------------------------------- Sub CheckForLUA() If GetRegistryDWORD(strLuaKeyPath,"EnableLUA",1)<> 0 Then MsgBox "User Access Control (UAC) is enabled on this computer." & _ vbCrLf & vbCrLf & "UAC must be disabled in order to edit " & _ "the registry and restart the service for the WebDAV Redirector. " & _ "Please disable UAC before running this application again. " & _ "This application will now exit.", _ vbCritical, "User Access Control" Self.close End If End Sub ' ---------------------------------------- ' Exit the application. ' ---------------------------------------- Sub ExitApplication() If blnHasChanges = False Then If MsgBox("Are you sure you want to exit?", _ vbQuestion Or vbYesNo Or vbDefaultButton2, _ "Exit Application") = vbNo Then Exit Sub End If Else Dim intRetVal intRetVal = MsgBox("You have unsaved changes. " & _ "Do you want to save them before you exit?", _ vbQuestion Or vbYesNoCancel Or vbDefaultButton1, _ "Exit Application") If intRetVal = vbYes Then Call SetValues() ElseIf intRetVal = vbCancel Then Exit Sub End If End If Self.close End Sub ' ---------------------------------------- ' Flag the application as having changes. ' ---------------------------------------- Sub FlagChanges() blnHasChanges = True End Sub ' ---------------------------------------- ' Retrieve the settings from the registry. ' ---------------------------------------- Sub GetValues() On Error Resume Next Dim tmpCount,tmpArray,tmpString ' Get the radio button values Call SetRadioValue(Document.all.BasicAuthLevel, _ GetRegistryDWORD(strWebClientKeyPath, _ "BasicAuthLevel",1)) Call SetRadioValue(Document.all.SupportLocking, _ GetRegistryDWORD(strWebClientKeyPath, _ "SupportLocking",1)) ' Get the text box values Document.all.InternetServerTimeoutInSec.Value = _ GetRegistryDWORD(strWebClientKeyPath, _ "InternetServerTimeoutInSec",30) Document.all.FileAttributesLimitInBytes.Value = _ GetRegistryDWORD(strWebClientKeyPath, _ "FileAttributesLimitInBytes",1000000) Document.all.FileSizeLimitInBytes.Value = _ GetRegistryDWORD(strWebClientKeyPath, _ "FileSizeLimitInBytes",50000000) Document.all.LocalServerTimeoutInSec.Value = _ GetRegistryDWORD(strWebClientKeyPath, _ "LocalServerTimeoutInSec",15) Document.all.SendReceiveTimeoutInSec.Value = _ GetRegistryDWORD(strWebClientKeyPath, _ "SendReceiveTimeoutInSec",60) Document.all.ServerNotFoundCacheLifeTimeInSec.Value = _ GetRegistryDWORD(strWebClientKeyPath, _ "ServerNotFoundCacheLifeTimeInSec",60) ' Get the text area values tmpArray = GetRegistryMULTISZ( _ strWebClientKeyPath,"AuthForwardServerList") For tmpCount = 0 To UBound(tmpArray) tmpString = tmpString & tmpArray(tmpCount) & vbTab Next If Len(tmpString)>0 Then Document.all.AuthForwardServerList.Value = _ Replace(Left(tmpString,Len(tmpString)-1),vbTab,vbCrLf) End If blnHasChanges = False End Sub ' ---------------------------------------- ' Save the settings in the registry. ' ---------------------------------------- Sub SetValues() On Error Resume Next ' Set the radio button values Call SetRegistryDWORD( _ strWebClientKeyPath, _ "BasicAuthLevel", _ GetRadioValue(Document.all.BasicAuthLevel)) Call SetRegistryDWORD( _ strWebClientKeyPath, _ "SupportLocking", _ GetRadioValue(Document.all.SupportLocking)) ' Set the text box values Call SetRegistryDWORD( _ strWebClientKeyPath, _ "InternetServerTimeoutInSec", _ Document.all.InternetServerTimeoutInSec.Value) Call SetRegistryDWORD( _ strWebClientKeyPath, _ "FileAttributesLimitInBytes", _ Document.all.FileAttributesLimitInBytes.Value) Call SetRegistryDWORD( _ strWebClientKeyPath, _ "FileSizeLimitInBytes", _ Document.all.FileSizeLimitInBytes.Value) Call SetRegistryDWORD( _ strWebClientKeyPath, _ "LocalServerTimeoutInSec", _ Document.all.LocalServerTimeoutInSec.Value) Call SetRegistryDWORD( _ strWebClientKeyPath, _ "SendReceiveTimeoutInSec", _ Document.all.SendReceiveTimeoutInSec.Value) Call SetRegistryDWORD( _ strWebClientKeyPath, _ "ServerNotFoundCacheLifeTimeInSec", _ Document.all.ServerNotFoundCacheLifeTimeInSec.Value) ' Set the text area values Call SetRegistryMULTISZ( _ strWebClientKeyPath, _ "AuthForwardServerList", _ Split(Document.all.AuthForwardServerList.Value,vbCrLf)) ' Prompt to restart the WebClient service If MsgBox("Do you want to restart the WebDAV Redirector " & _ "service so your settings will take effect?", _ vbQuestion Or vbYesNo Or vbDefaultButton2, _ "Restart WebDAV Redirector") = vbYes Then ' Restart the WebClient service. Call RestartWebClient() End If Call GetValues() End Sub ' ---------------------------------------- ' Start the WebClient service. ' ---------------------------------------- Sub RestartWebClient() On Error Resume Next Dim objWMIService,colServices,objService Document.All.TheBody.ClassName = "hide" Set objWMIService = GetObject( _ "winmgmts:{impersonationLevel=impersonate}!\\.\root\cimv2") Set colServices = objWMIService.ExecQuery( _ "Select * from Win32_Service Where Name='WebClient'") For Each objService in colServices objService.StopService() objService.StartService() Next Document.All.TheBody.ClassName = "show" End Sub ' ---------------------------------------- ' Retrieve a DWORD value from the registry. ' ---------------------------------------- Function GetRegistryDWORD( _ ByVal tmpKeyPath, _ ByVal tmpValueName, _ ByVal tmpDefaultValue) On Error Resume Next Dim tmpDwordValue If objRegistry.GetDWORDValue( _ HKEY_LOCAL_MACHINE, _ tmpKeyPath, _ tmpValueName, _ tmpDwordValue)=0 Then GetRegistryDWORD = CLng(tmpDwordValue) Else GetRegistryDWORD = CLng(tmpDefaultValue) End If End Function ' ---------------------------------------- ' Set a DWORD value in the registry. ' ---------------------------------------- Sub SetRegistryDWORD( _ ByVal tmpKeyPath, _ ByVal tmpValueName, _ ByVal tmpDwordValue) On Error Resume Next Call objRegistry.SetDWORDValue( _ HKEY_LOCAL_MACHINE, _ tmpKeyPath, _ tmpValueName, _ CLng(tmpDwordValue)) End Sub ' ---------------------------------------- ' Retrieve a MULTISZ value from the registry. ' ---------------------------------------- Function GetRegistryMULTISZ( _ ByVal tmpKeyPath, _ ByVal tmpValueName) On Error Resume Next Dim tmpMultiSzValue If objRegistry.GetMultiStringValue( _ HKEY_LOCAL_MACHINE, _ tmpKeyPath, _ tmpValueName, _ tmpMultiSzValue)=0 Then GetRegistryMULTISZ = tmpMultiSzValue Else GetRegistryMULTISZ = Array() End If End Function ' ---------------------------------------- ' Set a MULTISZ value in the registry. ' ---------------------------------------- Sub SetRegistryMULTISZ( _ ByVal tmpKeyPath, _ ByVal tmpValueName, _ ByVal tmpMultiSzValue) On Error Resume Next Call objRegistry.SetMultiStringValue( _ HKEY_LOCAL_MACHINE, _ tmpKeyPath, _ tmpValueName, _ tmpMultiSzValue) End Sub ' ---------------------------------------- ' Retrieve the value of a radio button group. ' ---------------------------------------- Function GetRadioValue(ByVal tmpRadio) On Error Resume Next Dim tmpCount For tmpCount = 0 To (tmpRadio.Length-1) If tmpRadio(tmpCount).Checked Then GetRadioValue = CLng(tmpRadio(tmpCount).Value) Exit For End If Next End Function ' ---------------------------------------- ' Set the value for a radio button group. ' ---------------------------------------- Sub SetRadioValue(ByVal tmpRadio, ByVal tmpValue) On Error Resume Next Dim tmpCount For tmpCount = 0 To (tmpRadio.Length-1) If CLng(tmpRadio(tmpCount).Value) = CLng(tmpValue) Then tmpRadio(tmpCount).Checked = True Exit For End If Next End Sub ' ---------------------------------------- ' ' ---------------------------------------- Sub Validate(tmpField) Dim tmpRegEx, tmpMatches Set tmpRegEx = New RegExp tmpRegEx.Pattern = "[0-9]" tmpRegEx.IgnoreCase = True tmpRegEx.Global = True Set tmpMatches = tmpRegEx.Execute(tmpField.Value) If tmpMatches.Count = Len(CStr(tmpField.Value)) Then If CDbl(tmpField.Value) => 0 And _ CDbl(tmpField.Value) =< 4294967295 Then Exit Sub End If End If MsgBox "Please enter a whole number between 0 and 4294967295.", _ vbCritical, "Validation Error" tmpField.Focus End Sub ' ---------------------------------------- ' ' ---------------------------------------- Sub BasicAuthWarning() MsgBox "WARNING:" & vbCrLf & vbCrLf & _ "Using Basic Authentication over non-SSL connections can cause " & _ "serious security issues. Usernames and passwords are transmitted " & _ "in clear text, therefore the use of Basic Authentication with " & _ "WebDAV is disabled by default for non-SSL connections. That " & _ "being said, this setting can override the default behavior for " & _ "Basic Authentication, but it is strongly discouraged.", _ vbCritical, "Basic Authentication Warning" End Sub ' ---------------------------------------- ' End of main code section. ' ---------------------------------------- </script> <style> body { color:#000000; background-color:#cccccc; font-family:'Segoe UI',Tahoma,Verdana,Arial; font-size:9pt; } fieldset { padding:10px; width:640px; } .button { width:150px; } .textbox { width:200px; height:22px; text-align:right; } .textarea { width:300px; height:50px; text-align:left; } .radio { margin-left:-5px; margin-top: -2px; } .hide { display:none; } .show { display:block; } select { width:300px; text-align:left; } table { border-collapse:collapse; empty-cells:hide; } h1 { font-size:14pt; } th { font-size:9pt; text-align:left; vertical-align:top; padding:2px; } td { font-size:9pt; text-align:left; vertical-align:top; padding:2px; } big { font-size:11pt; } small { font-size:8pt; } </style> </head> <body id="TheBody" class="hide"> <h1 align="center" id="TheTitle" style="margin-bottom:-20px;">WebDAV Redirector Settings</h1> <div align="center"> <p style="margin-bottom:-20px;"><i><small><b>Note</b>: See <a target="_blank" href="https://docs.microsoft.com/iis/publish/using-webdav/using-the-webdav-redirector/">Using the WebDAV Redirector</a> for additional details.</small></i></p> <form> <center> <table border="0" cellpadding="2" cellspacing="2" style="width:600px;"> <tr> <td style="width:600px;text-align:left"><fieldset title="Security Settings"> <legend> <b>Security Settings</b> </legend> These values affect the security behavior for the WebDAV Redirector.<br> <table style="width:600px;"> <tr title="Specifies whether the WebDAV Redirector can use Basic Authentication to communicate with a server."> <td style="width:300px"> <table border="0"> <tr> <td style="width:300px"><b>Basic Authentication Level</b></td> </tr> <tr> <td style="width:300px;"><span style="width:280px;padding-left:20px;"><small><i><b>Note</b>: Using basic authentication can cause <u>serious security issues</u> as the username and password are transmitted in clear text, therefore the use of basic authentication over WebDAV is disabled by default unless the connection is using SSL.</i></small></span></td> </tr> </table> </td> <td style="width:300px"> <table style="width:300px"> <tr> <td style="width:020px"><input class="radio" type="radio" value="0" name="BasicAuthLevel" onchange="VBScript:FlagChanges()" id="BasicAuthLevel0"></td> <td style="width:280px"><label for="BasicAuthLevel0">Basic Authentication is disabled</label></td> </tr> <tr> <td style="width:020px"><input class="radio" type="radio" value="1" checked name="BasicAuthLevel" onchange="VBScript:FlagChanges()" id="BasicAuthLevel1"></td> <td style="width:280px"><label for="BasicAuthLevel1">Basic Authentication is enabled for SSL web sites only</label></td> </tr> <tr> <td style="width:020px"><input class="radio" type="radio" value="2" name="BasicAuthLevel" onchange="VBScript:FlagChanges()" id="BasicAuthLevel2" onClick="VBScript:BasicAuthWarning()"></td> <td style="width:280px"><label for="BasicAuthLevel2">Basic Authentication is enabled for SSL and non-SSL web sites</label></td> </tr> </table> </td> </tr> <tr title="Specifies a list of local URLs for forwarding credentials that bypasses any proxy settings. (Note: This requires Windows Vista SP1 or later.)"> <td style="width:300px"> <table border="0"> <tr> <td style="width:300px"><b>Authentication Forwarding Server List</b></td> </tr> <tr> <td style="width:300px;"><span style="width:280px;padding-left:20px;"><small><i><b>Note</b>: Include one server name per line.</i></small></span></td> </tr> </table> </td> <td style="width:300px"><textarea class="textarea" name="AuthForwardServerList" onchange="VBScript:FlagChanges()"></textarea></td> </tr> <tr title="Specifies whether the WebDAV Redirector supports locking."> <td style="width:300px"><b>Support for WebDAV Locking</b></td> <td style="width:300px"> <table style="width:300px"> <tr> <td style="width:020px"><input class="radio" type="radio" value="1" checked name="SupportLocking" onchange="VBScript:FlagChanges()" id="SupportLocking1"></td> <td style="width:280px"><label for="SupportLocking1">Enable Lock Support</label></td> </tr> <tr> <td style="width:020px"><input class="radio" type="radio" value="0" name="SupportLocking" onchange="VBScript:FlagChanges()" id="SupportLocking0"></td> <td style="width:280px"><label for="SupportLocking0">Disable Lock Support</label></td> </tr> </table> </td> </tr> </table> </fieldset> </td> </tr> <tr> <td style="width:600px;text-align:left"><fieldset title="Time-outs"> <legend> <b>Time-outs and Maximum Sizes</b> </legend> These values affect the behavior for WebDAV Client/Server operations.<br> <table border="0" style="width:600px;"> <tr title="Specifies the connection time-out for the WebDAV Redirector uses when communicating with non-local WebDAV servers."> <td style="width:300px"><b>Internet Server Time-out</b> <small>(In Seconds)</small></td> <td style="width:300px"><input class="textbox" type="text" name="InternetServerTimeoutInSec" onchange="VBScript:FlagChanges()" onblur="VBScript:Validate(Me)" value="30"></td> </tr> <tr title="Specifies the connection time-out for the WebDAV Redirector uses when communicating with a local WebDAV server."> <td style="width:300px"><b>Local Server Time-out</b> <small>(In Seconds)</small></td> <td style="width:300px"><input class="textbox" type="text" name="LocalServerTimeoutInSec" onchange="VBScript:FlagChanges()" onblur="VBScript:Validate(Me)" value="15"></td> </tr> <tr title="Specifies the time-out in seconds that the WebDAV Redirector uses after issuing a request."> <td style="width:300px"><b>Send/Receive Time-out</b> <small>(In Seconds)</small></td> <td style="width:300px"><input class="textbox" type="text" name="SendReceiveTimeoutInSec" onchange="VBScript:FlagChanges()" onblur="VBScript:Validate(Me)" value="60"></td> </tr> <tr title="Specifies the period of time that a server is cached as non-WebDAV by the WebDAV Redirector. If a server is found in this list, a fail is returned immediately without attempting to contact the server."> <td style="width:300px"><b>Server Not Found Cache Time-out</b> <small>(In Seconds)</small></td> <td style="width:300px"><input class="textbox" type="text" name="ServerNotFoundCacheLifeTimeInSec" onchange="VBScript:FlagChanges()" onblur="VBScript:Validate(Me)" value="60"></td> </tr> <tr title="Specifies the maximum size in bytes that the WebDAV Redirector allows for file transfers."> <td style="width:300px"><b>Maximum File Size</b> <small>(In Bytes)</small></td> <td style="width:300px"><input class="textbox" type="text" name="FileSizeLimitInBytes" onchange="VBScript:FlagChanges()" onblur="VBScript:Validate(Me)" value="50000000"></td> </tr> <tr title="Specifies the maximum size that is allowed by the WebDAV Redirector for all properties on a specific collection."> <td style="width:300px"><b>Maximum Attributes Size</b> <small>(In Bytes)</small></td> <td style="width:300px"><input class="textbox" type="text" name="FileAttributesLimitInBytes" onchange="VBScript:FlagChanges()" onblur="VBScript:Validate(Me)" value="1000000"></td> </tr> </table> </fieldset> </td> </tr> <tr> <td style="text-align:center"> <table border="0"> <tr> <td style="text-align:center"><input class="button" type="button" value="Apply Settings" onclick="VBScript:SetValues()"> <td style="text-align:center"><input class="button" type="button" value="Exit Application" onclick="VBScript:ExitApplication()"> </tr> </table> </td> </tr> </table> </center> </form> </div> </body> </html>
Additional Notes
You will need to run this HTML Application as an administrator in order to save the settings and restart the Windows WebDAV Redirector. (Which is listed as the "WebClient" service in your Administrative Tools.)
This HTML Application performs basic validation for the numeric fields, and it prevents you from exiting the application when you have unsaved changes, but apart from that there's not much functionality other than setting and retrieving the registry values. How else can you get away with posting an application in a blog with only 500 lines of code and no compilation required? ;-]
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
How to determine if FTP clients are using FTPS
04 October 2011 • by Bob • FTP, LogParser
One of my colleagues here at Microsoft, Emmanuel Boersma, just reminded me of an email thread that we had several weeks ago, where a customer had asked him how they could tell if FTPS was being used on their FTP server. He had pointed out that when he looks at his FTP log files, the port number was always 21, so it wasn't as easy as looking at a website's log files and looking for port 80 for HTTP versus port 443 for HTTPS. I had sent him the following notes, and I thought that they might make a good blog. ;-)
As I mentioned earlier, we had discussed the control channel is typically over port 21 for both FTP and FTPS, so you can't rely on the port. But having said that, I mentioned that you will see certain verbs in your FTP logs that will let you know when FTPS is being used, and that’s a reliable way to check.
With that in mind, I suggested the following two methods that you can use to determine if FTPS is being used:
- If the port number is something other than 990, and you see the following verbs being used (and succeeding), then Explicit FTPS is being used:
- AUTH
- PBSZ
- PROT
- If the port is 990, then Implicit FTPS is being used. (This means the FTPS is always on.)
For example, see the highlighted data in following FTP log file excerpts:
Explicit FTPS over port 21:
#Fields: date time c-ip cs-username cs-host s-ip s-port cs-method cs-uri-stem sc-status sc-win32-status sc-substatus sc-bytes cs-bytes time-taken 2011-06-30 22:11:24 ::1 - - ::1 21 ControlChannelOpened - - 0 0 0 0 0 2011-06-30 22:11:24 ::1 - - ::1 21 AUTH TLS 234 0 0 31 10 16 2011-06-30 22:11:27 ::1 - - ::1 21 PBSZ 0 200 0 0 69 8 0 2011-06-30 22:11:27 ::1 - - ::1 21 PROT P 200 0 0 69 8 0 2011-06-30 22:11:36 ::1 - - ::1 21 USER robert 331 0 0 69 13 0 2011-06-30 22:11:42 ::1 robert - ::1 21 PASS *** 230 0 0 53 15 2808
Implicit FTPS over port 990:
#Fields: date time c-ip cs-username cs-host s-ip s-port cs-method cs-uri-stem sc-status sc-win32-status sc-substatus sc-bytes cs-bytes time-taken 2011-06-30 22:16:55 ::1 - - ::1 990 ControlChannelOpened - - 0 0 0 0 0 2011-06-30 22:16:58 ::1 - - ::1 990 USER robert 331 0 0 69 13 0 2011-06-30 22:16:58 ::1 robert - ::1 990 PASS *** 230 0 0 53 15 78 2011-06-30 22:16:58 ::1 robert - ::1 990 SYST - 500 5 51 1005 6 0 2011-06-30 22:16:58 ::1 robert - ::1 990 FEAT - 211 0 0 313 6 0 2011-06-30 22:16:58 ::1 robert - ::1 990 OPTS UTF8+ON 200 0 0 85 14 0 2011-06-30 22:16:58 ::1 robert - ::1 990 PBSZ 0 200 0 0 69 8 0 2011-06-30 22:16:58 ::1 robert - ::1 990 PROT P 200 0 0 69 8 0
FWIW – An explanation about Implicit FTPS and Explicit FTPS can be found in the following articles:
- http://blogs.msdn.com/b/robert_mcmurray/archive/2008/11/10/ftp-clients-part-2-explicit-ftps-versus-implicit-ftps.aspx
- http://www.iis.net/ConfigReference/system.applicationHost/sites/site/ftpServer/security/ssl
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
How to Use Managed Code (C#) to Create an FTP Home Directory Provider for the Days of the Week
29 September 2011 • by Bob • FTP, Extensibility
I had a question from someone that had an interesting scenario: they had a series of reports that their manufacturing company generates on a daily basis, and they wanted to automate uploading those files over FTP from their factory to their headquarters. Their existing automation created report files with names like Widgets.log, Sprockets.log, Gadgets.log, etc.
But they had an additional request: they wanted the reports dropped into folders based on the day of the week. People in their headquarters could retrieve the reports from a share on their headquarters network where the FTP server would drop the files, and anyone could look at data from anytime within the past seven days.
This seemed like an extremely trivial script for me to write, so I threw together the following example batch file for them:
@echo off pushd "C:\Reports" for /f "usebackq delims= " %%a in (`date /t`) do ( echo open MyServerName>ftpscript.txt echo MyUsername>>ftpscript.txt echo MyPassword>>ftpscript.txt echo mkdir %%a>>ftpscript.txt echo cd %%a>>ftpscript.txt echo asc>>ftpscript.txt echo prompt>>ftpscript.txt echo mput *.log>>ftpscript.txt echo bye>>ftpscript.txt ) ftp.exe -s:ftpscript.txt del ftpscript.txt popd
This would have worked great for most scenarios, but they pointed out a few problems in their specific environment: manufacturing and headquarters were in different geographical regions of the world, therefore in different time zones, and they wanted the day of the week to be based on the day of the week where their headquarters was located. They also wanted to make sure that if anyone logged in over FTP, they would only see the reports for the current day, and they didn't want to take a chance that something might go wrong with the batch file and they might overwrite the logs from the wrong day.
With all of those requirements in mind, this was beginning to look like a problem for a custom home directory provider to tackle. Fortunately, this was a really easy home directory provider to write, and I thought that it might make a good blog.
Note: I wrote and tested the steps in this blog using both Visual Studio 2010 and Visual Studio 2008; if you use an different version of Visual Studio, some of the version-specific steps may need to be changed.
In This Blog
- Step 1: Set up the Project Environment
- Step 2: Create the Extensibility Class
- Step 3: Add the Demo Provider to FTP
- Summary
Prerequisites
The following items are required to complete the procedures in this blog:
- The following version of IIS must be installed on your Windows computer, and the Internet Information Services (IIS) Manager must also be installed:
- IIS 7.0 must be installed on Windows Server 2008
- IIS 7.5 must be installed on Windows Server 2008 R2 or Windows 7
- The new FTP 7.5 service must be installed. To install FTP 7.5, follow the instructions in the following topic:
- You must have FTP publishing enabled for a site. To create a new FTP site, follow the instructions in the following topic:
- You need to create the folders for the days of the week under your FTP root directory; for example, Sunday, Monday, Tuesday, etc.
Step 1: Set up the Project Environment
In this step, you will create a project in Microsoft Visual Studio for the demo provider.
- Open Visual Studio 2008 or Visual Studio 2010.
- Click the File menu, then New, then Project.
- In the New Projectdialog box:
- Choose Visual C# as the project type.
- Choose Class Library as the template.
- Type FtpDayOfWeekHomeDirectory as the name of the project.
- Click OK.
- When the project opens, add a reference path to the FTP extensibility library:
- Click Project, and then click FtpDayOfWeekHomeDirectory Properties.
- Click the Reference Paths tab.
- Enter the path to the FTP extensibility assembly for your version of Windows, where C: is your operating system drive.
- For Windows Server 2008 and Windows Vista:
- C:\Windows\assembly\GAC_MSIL\Microsoft.Web.FtpServer\7.5.0.0__31bf3856ad364e35
- For 32-bit Windows 7 and Windows Server 2008 R2:
- C:\Program Files\Reference Assemblies\Microsoft\IIS
- For 64-bit Windows 7 and Windows Server 2008 R2:
- C:\Program Files (x86)\Reference Assemblies\Microsoft\IIS
- For Windows Server 2008 and Windows Vista:
- Click Add Folder.
- Add a strong name key to the project:
- Click Project, and then click FtpDayOfWeekHomeDirectory Properties.
- Click the Signing tab.
- Check the Sign the assembly check box.
- Choose <New...> from the strong key name drop-down box.
- Enter FtpDayOfWeekHomeDirectoryKey for the key file name.
- If desired, enter a password for the key file; otherwise, clear the Protect my key file with a password check box.
- Click OK.
- Note: FTP 7.5 Extensibility does not support the .NET Framework 4.0; if you are using Visual Studio 2010, or you have changed your default framework version, you may need to change the framework version for this project. To do so, use the following steps:
- Click Project, and then click FtpDayOfWeekHomeDirectory Properties.
- Click the Application tab.
- Choose .NET Framework 3.5 in the Target framework drop-down menu.
- Save, close, and re-open the project.
- Optional: You can add a custom build event to add the DLL automatically to the Global Assembly Cache (GAC) on your development computer:
- Click Project, and then click FtpDayOfWeekHomeDirectory Properties.
- Click the Build Events tab.
- Enter the appropriate commands in the Post-build event command linedialog box, depending on your version of Visual Studio:
- If you are using Visual Studio 2010:
net stop ftpsvc
call "%VS100COMNTOOLS%\vsvars32.bat">null
gacutil.exe /if "$(TargetPath)"
net start ftpsvc - If you are using Visual Studio 2008:
net stop ftpsvc
call "%VS90COMNTOOLS%\vsvars32.bat">null
gacutil.exe /if "$(TargetPath)"
net start ftpsvc
- If you are using Visual Studio 2010:
- Save the project.
Step 2: Create the Extensibility Class
In this step, you will implement the extensibility interfaces for the demo provider.
- Add the necessary references to the project:
- Click Project, and then click Add Reference...
- On the .NET tab, click Microsoft.Web.FtpServer.
- Click OK.
- Add the code for the authentication class:
- In Solution Explorer, double-click the Class1.cs file.
- Remove the existing code.
- Paste the following code into the editor:
using System; using System.Collections.Generic; using System.Collections.Specialized; using Microsoft.Web.FtpServer; public class FtpDayOfWeekHomeDirectory : BaseProvider, IFtpHomeDirectoryProvider { // Store the path to the default FTP folder. private static string _defaultDirectory = string.Empty; // Override the default initialization method. protected override void Initialize(StringDictionary config) { // Retrieve the default directory path from configuration. _defaultDirectory = config["defaultDirectory"]; // Test for the default home directory (Required). if (string.IsNullOrEmpty(_defaultDirectory)) { throw new ArgumentException( "Missing default directory path in configuration."); } } // Define the home directory provider method. string IFtpHomeDirectoryProvider.GetUserHomeDirectoryData( string sessionId, string siteName, string userName) { // Return the path to the folder for the day of the week. return String.Format( @"{0}\{1}", _defaultDirectory, DateTime.Today.DayOfWeek); } }
- Save and compile the project.
Note: If you did not use the optional steps to register the assemblies in the GAC, you will need to manually copy the assemblies to your IIS 7 computer and add the assemblies to the GAC using the Gacutil.exe tool. For more information, see the following topic on the Microsoft MSDN Web site:
Step 3: Add the Demo Provider to FTP
In this step, you will add your provider to the global list of custom providers for your FTP service, configure your provider's settings, and enable your provider for an FTP site.
Adding your Provider to FTP
- Determine the assembly information for your extensibility provider:
- In Windows Explorer, open your "C:\Windows\assembly" path, where C: is your operating system drive.
- Locate the FtpDayOfWeekHomeDirectory assembly.
- Right-click the assembly, and then click Properties.
- Copy the Culture value; for example: Neutral.
- Copy the Version number; for example: 1.0.0.0.
- Copy the Public Key Token value; for example: 426f62526f636b73.
- Click Cancel.
- Add the extensibility provider to the global list of FTP authentication providers:
- Open the Internet Information Services (IIS) Manager.
- Click your computer name in the Connections pane.
- Double-click FTP Authentication in the main window.
- Click Custom Providers... in the Actions pane.
- Click Register.
- Enter FtpDayOfWeekHomeDirectory for the provider Name.
- Click Managed Provider (.NET).
- Enter the assembly information for the extensibility provider using the information that you copied earlier. For example:
FtpDayOfWeekHomeDirectory,FtpDayOfWeekHomeDirectory,version=1.0.0.0,Culture=neutral,PublicKeyToken=426f62526f636b73 - Click OK.
- Clear the FtpDayOfWeekHomeDirectory check box in the providers list.
- Click OK.
Note: If you prefer, you could use the command line to add the provider to FTP by using syntax like the following example:
cd %SystemRoot%\System32\Inetsrv
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"[name='FtpDayOfWeekHomeDirectory',type='FtpDayOfWeekHomeDirectory,FtpDayOfWeekHomeDirectory,version=1.0.0.0,Culture=neutral,PublicKeyToken=426f62526f636b73']" /commit:apphost
Configuring your Provider's Settings
At the moment there is no user interface that allows you to configure properties for a custom home directory provider, so you will have to use the following command line:
cd %SystemRoot%\System32\Inetsrv
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpDayOfWeekHomeDirectory']" /commit:apphost
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpDayOfWeekHomeDirectory'].[key='defaultDirectory',value='C:\Inetpub\ftproot']" /commit:apphost
Note: The highlighted area contains the value that you need to update with the root directory of your FTP site.
Enabling your Provider for an FTP site
At the moment there is no user interface that allows you to enable a custom home directory provider for an FTP site, so you will have to use the following command line:
cd %SystemRoot%\System32\Inetsrv
appcmd.exe set config -section:system.applicationHost/sites /+"[name='My FTP Site'].ftpServer.customFeatures.providers.[name='FtpDayOfWeekHomeDirectory']" /commit:apphost
appcmd.exe set config -section:system.applicationHost/sites /"[name='My FTP Site'].ftpServer.userIsolation.mode:Custom" /commit:apphost
Note: The highlighted areas contain the name of the FTP site where you want to enable the custom home directory provider.
Summary
In this blog I showed you how to:
- Create a project in Visual Studio 2010 or Visual Studio 2008 for a custom FTP home directory provider.
- Implement the extensibility interface for custom FTP home directories.
- Add a custom home directory provider to your FTP service.
When users connect to your FTP site, the FTP service will drop their session in the corresponding folder for the day of the week under the home directory for your FTP site, and they will not be able to change to the root directory or a directory for a different day of the week.
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
Proud Microsoft Dad Moments
23 September 2011 • by Bob • Family
This past August my middlest daughter married her fiancé in a small ceremony that was as unique as the two of them. That being said, one moment of entertainment occurred during the service when my daughter recited her self-composed vows by reading them from her Windows Phone.

As a Microsoft Dad, this was too amusing to keep to myself, so I forwarded a photo to some of the folks in the Windows Phone division, and the story was picked up by the Windows Blog team, which published my daughter's description of the event as "First Person: With this phone, I thee wed"
"The wedding was in a little white chapel, up against a mountain, near the ocean. We wanted a simple, elegant wedding that represented us. We went through all the different weddings we'd seen - do we want to mix the sand? light a unity candle? - but we decided that wasn't really us. So we cut out all the things that weren't really us, and wrote our own vows.
"My phone is the thing I always have on me, so when I needed to write my vows I used Office on my phone. Whenever I thought of something I wanted to add, I could just jot it down. When it came to the day of, I thought maybe I should write it on a piece of paper. Then the minister said, 'Why not just read it off your phone?'
"My husband didn't know I was going to read off my phone. He said his vows off paper, and when it was my turn I looked at the pastor and she pulled out my phone and handed it to me. Everyone laughed - it made it a little more lighthearted, so we weren't bawling.
"My husband laughed, because I'm on my phone all the time, and he's on his. So I'm sure he wished he had thought of it. Now the vows are saved on my phone, and every time I want to go back and read them, I can. Meanwhile, his piece of paper is floating around somewhere - I don't even know where it is."
(photo: ©Rebecca Calvo Photography)
The Decline and Fall of the American Empire
17 September 2011 • by Bob • History, Politics
When you study history, you are invariably introduced to Carroll Quigley's seven stages in The Evolution of Civilizations. In chapter 5 of his book, Quigley describes the seven states in the history of a civilization; these are:
- Mixture: The mixture of diverse, smaller societies to form a unique, larger whole.
- Gestation: The gestation of that large society, specifically in the development of a method for accumulating an economic surplus and investing it in methods of expansion.
- Expansion: A period of vigorous expansion in population, territory, technological competence, wealth, knowledge, etc.
- Conflict: A period of major conflict between societal elements or geographical areas within the civilization.
- Empire: The development of a universal empire ruling over the entire civilization, which far from being a golden age represents a precursor to decay and collapse.
- Decay: The decay of the civilization as exemplified in the ossification of institutions and structures within the empire.
- Collapse/Invasion: The collapse of the civilization, usually through invasion by a younger civilization that is in the expansion phase.
Every great civilization has gone through this formula - with no exceptions.
From my perspective, the history of the United States has emerged in the following way:
- Our Mixture phase was pre-1750s as European settlers began to arrive and colonize the East Coast.
- Gestation followed the 1750s through the early 1800s as the colonists won their independence from European rule and began to establish a new nation.
- Expansion was from the early 1800s through the 1860s as the new nation pushed west toward the Pacific Ocean.
- Conflict was from 1860s through the latter 1890s as the United States grappled with the Civil War and its aftermath.
- Empire was from the early 1900s through the latter 1950s as the reunified United States fought a series of World Wars and established itself as a dominant world power.
- Decay began in the late 1950s and early 1960s as the generation born during the post-WWII Baby Boom spat on the prosperity that had been fought for and freely given to them, and all vestiges of ethical and moral standards were removed from public education. This period was marked by dramatic rises in crime rates, drug proliferation, corruption, divorce, unemployment, abortions-on-demand, corporate greed, and worst of all - the political ineptitude which prevents anything from being done about it.
According to Mr. Quigley's formula, all that the United States have left to face are Collapse and Invasion; civilizations do not recover once they have entered the Decay phase.
What is tragically ironic is that the people who vociferously claim to be trying to save the United States, namely Progressives and Liberals, are actually doing the most damage. As Quigley illustrates in his book, when members of a civilization become so preoccupied with arguing about what they perceive are their "rights" instead of contributing to society and adhering to an ethical set of standards or morals, the fabric of civilization unravels, and eventually implodes as an emerging civilization invades and conquers.
In this present day and age, people are rushing headlong into their inevitable demise; all the while they are wearing blinders which prevent them from seeing what is obvious to the less-outspoken of their peers. It is a sad manifestation of The Emperor's New Clothes; and even though the irony is missed by those who are too foolish to see themselves as members of the deceived, future generations will have the perspective granted by history with which to judge this time period with impartiality (and thereby with greater accuracy).
Several hundred years from now, historians of that coming era will look back with amazement as they analyze how the American civilization was ripped apart by the selfish desires of those who claimed to be acting in the best interests of society.
In closing, I think the rock group Rush expressed that sentiment quite well in their song "A Farewell to Kings":
A Farewell To Kings
When they turn the pages of history
When these days have passed long ago
Will they read of us with sadness
For the seeds that we let grow
We turned our gaze
From the castles in the distance
Eyes cast down
On the path of least resistance
Cities full of hatred, fear and lies
Withered hearts and cruel tormented eyes
Scheming demons dressed in kingly guise
Beating down the multitude
And scoffing at the wise
:-(
FTP and LDAP - Part 2: How to Set Up an Active Directory Lightweight Directory Services (AD LDS) Server
16 September 2011 • by Bob • FTP, Extensibility
This blog is designed as a complement to my FTP and LDAP - Part 1: How to Use Managed Code (C#) to Create an FTP Authentication Provider that uses an LDAP Server blog post. In this second blog, I'll walk you through the steps to set up an Active Directory Lightweight Directory Services (AD LDS) server, which you can use with the custom FTP LDAP Authentication provider that I discussed in my last blog.
In This Blog
Step 1: Installing AD LDS
The following steps will walk you through installing Active Directory Lightweight Directory Services on a computer that is running Windows Server 2008.
Adding the AD LDS Role
- Open the Windows Server 2008 Server Manager, click Roles in the navigation pane, and then click Add Roles.

- Check the box for Active Directory Lightweight Directory Services, and then click Next.

- Read the information on the Introduction to Active Directory Lightweight Directory Services page, and then click Next.

- Verify the Confirmation Installation Settings, and then click Next.

- The installation will start; this may take several minutes to complete.

- When the installation has completed, click Close.

Creating an AD LDS instance
Note: Before completing these steps I created a local user account named "LdapAdmin" that I would specify the administrative account for managing my LDAP instance. This user account was only a member of the local "Users" group, and not a member of the local "Administrators" group.
- Click Start, then click Administrative Tools, and then click Active Directory Lightweight Directory Services Setup Wizard.

- When the Active Directory Lightweight Directory Services Setup Wizard appears, click Next.

- Select A unique instance, and then click Next.

- Enter a name for your instance, for example "MyTestInstance," and then click Next.

- Verify the port numbers for LDAP connections, and then click Next.

- Choose Yes, create an application directory partition, and then enter a unique partition name by using X.500 path syntax. For example: "CN=MyServer,DC=MyDomain,DC=local". When you have finished entering your partition name, click Next.

- Verify the paths to the AD LDS files for this instance, and then click Next.

- Choose an account for your service account. (Note: Because I was creating a standalone LDAP server, I chose to use the network service account.) Once you have chosen an account, click Next.

- If you choose to use the network service account, the AD LDS wizard will prompt you about replication. Click Yes to continue.

- Choose an account as your AD LDS administrator. (Note: In my situation I chose the LdapAdmin account that I had created earlier; I did this so that I wouldn't be storing the credentials for an administrative account.) Once you have chosen an account, click Next.

- Choose one of the following LDIF files to import; these will be used to create user accounts. Note: I tested my FTP LDAP authentication provider with both LDIF files.
- Verify your installation options, and then click Next.

- When prompted for your AD LDS credentials, enter the credentials for the account that you chose to administer your AD LDS instance.

- The wizard will begin to install the requisite files and create your instance; this may take several minutes to complete.


- When the wizard has completed, click Finish.

Step 2: Using ADSI Edit to add Users and Groups
Connecting to your AD LDS Server
- Click Start, and then Administrative Tools, and then ADSI Edit.
- Click Action, and then click Connect to...

- When the Connection Settingsdialog box is displayed:
- Enter the LDAP path for your AD LDS server in the Select or type a Distinguished Name or Naming Contexttext box. For example:
- CN=MyServer,DC=MyDomain,DC=local
- Enter the server name and port in the Select or type a domain or servertext box. For example:
- MYSERVER:389
- The preceding steps should create the following path in the Pathtext box:
- LDAP://MYSERVER:389/CN=MyServer,DC=MyDomain,DC=local

- Click the Advanced button; when the Advanceddialog box is displayed:
- Check the Specify Credentials box.
- Enter the user name and password for your AD LDS server.
- Click OK.

- Enter the LDAP path for your AD LDS server in the Select or type a Distinguished Name or Naming Contexttext box. For example:
- Click OK.
Adding a User Object
- Expand the tree until you have highlighted the correct LDAP path for your server. For example:
- CN=MyServer,DC=MyDomain,DC=local.

- Click Action, and then New, and then Object...

- Highlight the appropriate user class, and then click Next.

- Enter the common name for your user, and then click Next. For example: enter FtpUser for the common name.

- Click Finish.

- Right-click the user that you created, and then click Properties.

- Select msDS-UserAccountDisabled in the list of attributes, and then click Edit.

- Select False, and then click OK.

- Select userPrincipalName in the list of attributes, and then click Edit.

- Enter your user's common name for the value, and then click OK. For example: enter FtpUser for the common name.

- Click OK to close the user properties dialog box.
- Right-click the user that you created, and then click Reset Password...

- Enter and confirm the password for your user.

- Click OK.
Adding Users to Groups
- Retrieve the Distinguished Name (DN) for a user:
- Add the user to a group:
- Expand the tree until you have highlighted a group in your server. For example, you could use the built-in CN-Users group.

- Right-click the group, and then click Properties.

- Select member in the list of attributes, and then click Edit.

- When the editor dialog box is displayed, click Add DN...

- When the Add Distinguished Name (DN) dialog box appears, paste the user DN syntax that you copied earlier. For example: CN=FtpUser,CN=MyServer,DC=MyDomain,DC=local.

- Click OK to close the Add DN dialog box.

- Click OK to close the group's properties dialog box.
- Expand the tree until you have highlighted a group in your server. For example, you could use the built-in CN-Users group.
More Information
For additional information about working with AD LDS instances, see the following URLs:
- Manage an AD LDS Instance Using ADSI Edit
http://technet.microsoft.com/en-us/library/cc794959.aspx - Managing Directory Security Principals in the .NET Framework 3.5
http://msdn.microsoft.com/en-us/magazine/cc135979.aspx
Enabling the Custom FTP LDAP Authentication Provider for an FTP site
While this is technically outside the scope of setting up the LDAP server, I'm reposting the notes from my last blog about adding the FTP LDAP Authentication provider and adding authorization rules for FTP users or groups.
- Add the custom authentication provider for an FTP site:
- Open an FTP site in the Internet Information Services (IIS) Manager.
- Double-click FTP Authentication in the main window.
- Click Custom Providers... in the Actions pane.
- Check FtpLdapAuthentication in the providers list.
- Click OK.
- Add an authorization rule for the authentication provider:
- Double-click FTP Authorization Rules in the main window.
- Click Add Allow Rule... in the Actions pane.
- You can add either of the following authorization rules:
- For a specific user:
- Select Specified users for the access option.
- Enter a user name that you created in your AD LDS partition.
- For a role or group:
- Select Specified roles or user groups for the access option.
- Enter the role or group name that you created in your AD LDS partition.
- Select Read and/or Write for the Permissions option.
- For a specific user:
- Click OK.
Once these settings are configured and users connect to your FTP site, the FTP service will attempt to authenticate users from your LDAP server by using the custom FTP LDAP Authentication provider.
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
FTP and LDAP - Part 1: How to Use Managed Code (C#) to Create an FTP Authentication Provider that uses an LDAP Server
16 September 2011 • by Bob • FTP, Extensibility
Over the past few years I've created a series of authentication providers for the FTP 7.5 service that ships with Windows Server 2008 R2 and Windows 7, and is available for download for Windows Server 2008. Some of these authentication providers are available on the http://learn.iis.net/page.aspx/590/developing-for-ftp-75/ website, while others have been in my blog posts.
With that in mind, I had a question a little while ago about using an LDAP server to authenticate users for the FTP service, and it seemed like that would make a great subject for another custom FTP authentication provider blog post.
The steps in this blog will lead you through the steps to use managed code to create an FTP authentication provider that uses a server running Active Directory Lightweight Directory Services (AD LDS) that is located on your local network.
Note: I wrote and tested the steps in this blog using both Visual Studio 2010 and Visual Studio 2008; if you use an different version of Visual Studio, some of the version-specific steps may need to be changed.
In This Blog
- Step 1: Set up the Project Environment
- Step 2: Create the Extensibility Class
- Step 3: Add the Demo Provider to FTP
- Summary
Prerequisites
The following items are required to complete the procedures in this blog:
- The following version of IIS must be installed on your Windows computer, and the Internet Information Services (IIS) Manager must also be installed:
- IIS 7.0 must be installed on Windows Server 2008
- IIS 7.5 must be installed on Windows Server 2008 R2 or Windows 7
- The new FTP 7.5 service must be installed. To install FTP 7.5, follow the instructions in the following topic:
- You must have FTP publishing enabled for a site. To create a new FTP site, follow the instructions in the following topic:
- You must have an AD LDS server available on your local network. Note: See my How to Set Up an Active Directory Lightweight Directory Services (AD LDS) Server blog post for more information.
Note: To test this blog, I used AD LDS on Windows Server 2008; if you use a different LDAP server, you may need to change some of the LDAP syntax in the code samples. To get started using AD LDS, see the following topics:
- AD LDS Getting Started Step-by-Step Guide
http://technet.microsoft.com/en-us/library/cc770639.aspx - Create a New AD LDS Instance
http://technet.microsoft.com/en-us/library/cc816778.aspx
I tested this blog by using the user objects from both the MS-User.LDF and MS-InetOrgPerson.LDF Lightweight Directory interchange Format (LDIF) files.
Important
To help improve the performance for authentication requests, the FTP service caches the credentials for successful logins for 15 minutes by default. This means that if you change the password in your AD LDS server, this change may not be reflected for the cache duration. To alleviate this, you can disable credential caching for the FTP service. To do so, use the following steps:
- Open a command prompt.
- Type the following commands:
cd /d "%SystemRoot%\System32\Inetsrv" Appcmd.exe set config -section:system.ftpServer/caching /credentialsCache.enabled:"False" /commit:apphost Net stop FTPSVC Net start FTPSVC
- Close the command prompt.
Step 1: Set up the Project Environment
In this step, you will create a project in Visual Studio 2008 for the demo provider.
- Open Microsoft Visual Studio 2008.
- Click the File menu, then New, then Project.
- In the New Projectdialog box:
- Choose Visual C# as the project type.
- Choose Class Library as the template.
- Type FtpLdapAuthentication as the name of the project.
- Click OK.
- When the project opens, add a reference path to the FTP extensibility library:
- Click Project, and then click FtpLdapAuthentication Properties.
- Click the Reference Paths tab.
- Enter the path to the FTP extensibility assembly for your version of Windows, where C: is your operating system drive.
- For Windows Server 2008 and Windows Vista:
- C:\Windows\assembly\GAC_MSIL\Microsoft.Web.FtpServer\7.5.0.0__31bf3856ad364e35
- For 32-bit Windows 7 and Windows Server 2008 R2:
- C:\Program Files\Reference Assemblies\Microsoft\IIS
- For 64-bit Windows 7 and Windows Server 2008 R2:
- C:\Program Files (x86)\Reference Assemblies\Microsoft\IIS
- For Windows Server 2008 and Windows Vista:
- Click Add Folder.
- Add a strong name key to the project:
- Click Project, and then click FtpLdapAuthentication Properties.
- Click the Signing tab.
- Check the Sign the assembly check box.
- Choose <New...> from the strong key name drop-down box.
- Enter FtpLdapAuthenticationKey for the key file name.
- If desired, enter a password for the key file; otherwise, clear the Protect my key file with a password check box.
- Click OK.
- Note: FTP 7.5 Extensibility does not support the .NET Framework 4.0; if you are using Visual Studio 2010, or you have changed your default framework version, you may need to change the framework version. To do so, use the following steps:
- Click Project, and then click FtpLdapAuthentication Properties.
- Click the Application tab.
- Choose .NET Framework 3.5 in the Target framework drop-down menu.
- Save, close, and re-open the project.
- Optional: You can add a custom build event to add the DLL automatically to the Global Assembly Cache (GAC) on your development computer:
- Click Project, and then click FtpLdapAuthentication Properties.
- Click the Build Events tab.
- Enter the appropriate commands in the Post-build event command linedialog box, depending on your version of Visual Studio:
- If you are using Visual Studio 2010:
net stop ftpsvc
call "%VS100COMNTOOLS%\vsvars32.bat">null
gacutil.exe /if "$(TargetPath)"
net start ftpsvc - If you are using Visual Studio 2008:
net stop ftpsvc
call "%VS90COMNTOOLS%\vsvars32.bat">null
gacutil.exe /if "$(TargetPath)"
net start ftpsvc
- If you are using Visual Studio 2010:
- Save the project.
Step 2: Create the Extensibility Class
In this step, you will implement the authentication and role extensibility interfaces for the demo provider.
- Add the necessary references to the project:
- Click Project, and then click Add Reference...
- On the .NET tab, click Microsoft.Web.FtpServer.
- Click OK.
- Repeat the above steps to add the following references to the project:
- System.Configuration
- System.DirectoryServices
- System.DirectoryServices.AccountManagement
- Add the code for the authentication class:
- In Solution Explorer, double-click the Class1.cs file.
- Remove the existing code.
- Paste the following code into the editor:
using System; using System.Collections.Specialized; using System.Configuration.Provider; using System.DirectoryServices; using System.DirectoryServices.AccountManagement; using Microsoft.Web.FtpServer; public class FtpLdapAuthentication : BaseProvider, IFtpAuthenticationProvider, IFtpRoleProvider { private static string _ldapServer = string.Empty; private static string _ldapPartition = string.Empty; private static string _ldapAdminUsername = string.Empty; private static string _ldapAdminPassword = string.Empty; // Override the default initialization method. protected override void Initialize(StringDictionary config) { // Retrieve the provider settings from configuration. _ldapServer = config["ldapServer"]; _ldapPartition = config["ldapPartition"]; _ldapAdminUsername = config["ldapAdminUsername"]; _ldapAdminPassword = config["ldapAdminPassword"]; // Test for the LDAP server name (Required). if (string.IsNullOrEmpty(_ldapServer) || string.IsNullOrEmpty(_ldapPartition)) { throw new ArgumentException( "Missing LDAP server values in configuration."); } } public bool AuthenticateUser( string sessionId, string siteName, string userName, string userPassword, out string canonicalUserName) { canonicalUserName = userName; // Attempt to look up the user and password. return LookupUser(true, userName, string.Empty, userPassword); } public bool IsUserInRole( string sessionId, string siteName, string userName, string userRole) { // Attempt to look up the user and role. return LookupUser(false, userName, userRole, string.Empty); } private static bool LookupUser( bool isUserLookup, string userName, string userRole, string userPassword) { PrincipalContext _ldapPrincipalContext = null; DirectoryEntry _ldapDirectoryEntry = null; try { // Create the context object using the LDAP connection information. _ldapPrincipalContext = new PrincipalContext( ContextType.ApplicationDirectory, _ldapServer, _ldapPartition, ContextOptions.SimpleBind, _ldapAdminUsername, _ldapAdminPassword); // Test for LDAP credentials. if (string.IsNullOrEmpty(_ldapAdminUsername) || string.IsNullOrEmpty(_ldapAdminPassword)) { // If LDAP credentials do not exist, attempt to create an unauthenticated directory entry object. _ldapDirectoryEntry = new DirectoryEntry("LDAP://" + _ldapServer + "/" + _ldapPartition); } else { // If LDAP credentials exist, attempt to create an authenticated directory entry object. _ldapDirectoryEntry = new DirectoryEntry("LDAP://" + _ldapServer + "/" + _ldapPartition, _ldapAdminUsername, _ldapAdminPassword, AuthenticationTypes.Secure); } // Create a DirectorySearcher object from the cached DirectoryEntry object. DirectorySearcher userSearcher = new DirectorySearcher(_ldapDirectoryEntry); // Specify the the directory searcher to filter by the user name. userSearcher.Filter = String.Format("(&(objectClass=user)(cn={0}))", userName); // Specify the search scope. userSearcher.SearchScope = SearchScope.Subtree; // Specify the directory properties to load. userSearcher.PropertiesToLoad.Add("distinguishedName"); // Specify the search timeout. userSearcher.ServerTimeLimit = new TimeSpan(0, 1, 0); // Retrieve a single search result. SearchResult userResult = userSearcher.FindOne(); // Test if no result was found. if (userResult == null) { // Return false if no matching user was found. return false; } else { if (isUserLookup == true) { try { // Attempt to validate credentials using the username and password. return _ldapPrincipalContext.ValidateCredentials(userName, userPassword, ContextOptions.SimpleBind); } catch (Exception ex) { // Throw an exception if an error occurs. throw new ProviderException(ex.Message); } } else { // Retrieve the distinguishedName for the user account. string distinguishedName = userResult.Properties["distinguishedName"][0].ToString(); // Create a DirectorySearcher object from the cached DirectoryEntry object. DirectorySearcher groupSearcher = new DirectorySearcher(_ldapDirectoryEntry); // Specify the the directory searcher to filter by the group/role name. groupSearcher.Filter = String.Format("(&(objectClass=group)(cn={0}))", userRole); // Specify the search scope. groupSearcher.SearchScope = SearchScope.Subtree; // Specify the directory properties to load. groupSearcher.PropertiesToLoad.Add("member"); // Specify the search timeout. groupSearcher.ServerTimeLimit = new TimeSpan(0, 1, 0); // Retrieve a single search result. SearchResult groupResult = groupSearcher.FindOne(); // Loop through the member collection. for (int i = 0; i < groupResult.Properties["member"].Count; ++i) { string member = groupResult.Properties["member"][i].ToString(); // Test if the current member contains the user's distinguished name. if (member.IndexOf(distinguishedName, StringComparison.OrdinalIgnoreCase) > -1) { // Return true (role lookup succeeded) if the user is found. return true; } } // Return false (role lookup failed) if the user is not found for the role. return false; } } } catch (Exception ex) { // Throw an exception if an error occurs. throw new ProviderException(ex.Message); } } }
- Save and compile the project.
Note: If you did not use the optional steps to register the assemblies in the GAC, you will need to manually copy the assemblies to your IIS 7 computer and add the assemblies to the GAC using the Gacutil.exe tool. For more information, see the following topic on the Microsoft MSDN Web site:
Step 3: Add the Demo Provider to FTP
In this step, you will add your provider to the list of providers for your FTP service, configure your provider for your LDAP server, and enable your provider to authenticate users for an FTP site.
Adding your Provider to FTP
- Determine the assembly information for your extensibility provider:
- In Windows Explorer, open your "C:\Windows\assembly" path, where C: is your operating system drive.
- Locate the FtpLdapAuthentication assembly.
- Right-click the assembly, and then click Properties.
- Copy the Culture value; for example: Neutral.
- Copy the Version number; for example: 1.0.0.0.
- Copy the Public Key Token value; for example: 426f62526f636b73.
- Click Cancel.
- Add the extensibility provider to the global list of FTP authentication providers:
- Open the Internet Information Services (IIS) Manager.
- Click your computer name in the Connections pane.
- Double-click FTP Authentication in the main window.
- Click Custom Providers... in the Actions pane.
- Click Register.
- Enter FtpLdapAuthentication for the provider Name.
- Click Managed Provider (.NET).
- Enter the assembly information for the extensibility provider using the information that you copied earlier. For example:
FtpLdapAuthentication,FtpLdapAuthentication,version=1.0.0.0,Culture=neutral,PublicKeyToken=426f62526f636b73 - Click OK.
- Clear the FtpLdapAuthentication check box in the providers list.
- Click OK.
Configuring your Provider's Settings
- Determine the connection information for your LDAP server; there are four pieces of information that you will need to know in order to configure the extensibility provider to talk to your LDAP server:
- Server Name and TCP/IP Port: This is the name (or IP address) of the server that is hosting your LDAP service; the port is usually 389. These will be added to your provider using the "SERVERNAME:PORT" syntax.
- LDAP Partition: This is the LDAP path within your LDAP service to your data, for example: "CN=ServerName,DC=DomainName,DC=DomainExtension."
- LDAP Username: This is a username that has access to your LDAP server; this is not the name of an account that you will use for FTP access, and it does not have to be a Windows account.
- LDAP Password: This is the password that is associated with the LDAP username.
- Using the information from the previous steps, configure the options for the provider:
- At the moment there is no user interface that enables you to add properties for a custom authentication module, so you will have to use the following command line. You will need to update the highlighted areas with the information from the previous steps and the information for your LDAP server:
cd %SystemRoot%\System32\Inetsrv
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpLdapAuthentication']" /commit:apphost
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpLdapAuthentication'].[key='ldapServer',value='MYSERVER:389']" /commit:apphost
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpLdapAuthentication'].[key='ldapPartition',value='CN=MyServer,DC=MyDomain,DC=local']" /commit:apphost
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpLdapAuthentication'].[key='ldapAdminUsername',encryptedValue='MyAdmin']" /commit:apphost
appcmd.exe set config -section:system.ftpServer/providerDefinitions /+"activation.[name='FtpLdapAuthentication'].[key='ldapAdminPassword',encryptedValue='MyPassword1']" /commit:apphost - Note: The highlighted areas are the values for the ldapServer, ldapPartition, ldapAdminUsername, and ldapAdminPassword settings, which configure your network environment for your LDAP server.
- At the moment there is no user interface that enables you to add properties for a custom authentication module, so you will have to use the following command line. You will need to update the highlighted areas with the information from the previous steps and the information for your LDAP server:
Enabling your Provider for an FTP site
- Add the custom authentication provider for an FTP site:
- Open an FTP site in the Internet Information Services (IIS) Manager.
- Double-click FTP Authentication in the main window.
- Click Custom Providers... in the Actions pane.
- Check FtpLdapAuthentication in the providers list.
- Click OK.
- Add an authorization rule for the authentication provider:
- Double-click FTP Authorization Rules in the main window.
- Click Add Allow Rule... in the Actions pane.
- You can add either of the following authorization rules:
- For a specific user:
- Select Specified users for the access option.
- Enter a user name that you created in your AD LDS partition.
- For a role or group:
- Select Specified roles or user groups for the access option.
- Enter the role or group name that you created in your AD LDS partition.
- Select Read and/or Write for the Permissions option.
- For a specific user:
- Click OK.
Summary
In this blog I showed you how to:
- Create a project in Visual Studio 2010 or Visual Studio 2008 for a custom FTP authentication provider.
- Implement the extensibility interface for custom FTP authentication.
- Add a custom authentication provider to your FTP service.
When users connect to your FTP site, the FTP service will attempt to authenticate users from your LDAP server by using your custom authentication provider.
Additional Information
The PrincipalContext.ValidateCredentials() method will validate the user name in the userName parameter with the value of the userPrincipalName attribute of the user object in AD LDS. Because of this, the userPrincipalName attribute for a user object is expected to match the name of the user account that an FTP client will use to log in, which will should be the same value as the cn attribute for the user object. Therefore, when you create a user object in AD LDS, you will need to set the corresponding userPrincipalName attribute for the user object. In addition, when you create a user object in AD LDS, the msDS-UserAccountDisabled attribute is set to TRUE by default, so you will need to change the value of that attribute to FALSE before you attempt to log in.
For more information, see my follow-up blog that is titled FTP and LDAP - Part 2: How to Set Up an Active Directory Lightweight Directory Services (AD LDS) Server.
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
The Days Grow Shorter...
15 September 2011 • by Bob • Ponderings
Back in the 1980s I was a big fan of the Canadian Power Trio named "Triumph." As far as arena rock was concerned, few bands could put on a show that was anywhere near as entertaining as a Triumph concert. It wasn't just about being a fan - there are any number of great bands out there who could put on a good show if you already liked them; but Triumph put on a killer show whether you liked them or not.
At the height of their popularity, Triumph recorded what was to become one of their greatest hits, which was a song that was titled "Fight the Good Fight." Many guitar players - myself included - spent a good deal of time learning that song, and I always enjoyed playing it live in the various rock bands that I played in throughout my teenage years.
As the first official day of Autumn is just around the corner here in Seattle, the opening lines to "Fight the Good Fight" seem to take on special meaning:
"The days grow shorter,
And the nights are getting long.
Feels like we're running out of time."
As I look out of my office window, that's exactly what I see:
Our short-lived Pacific Northwest Summer appears to have come to a close, and the clouds seem like they're here for the duration. The sun is setting a little earlier each day, and within a few months the choleric combination of miserable mists and depressing dusk will shorten the average day to six hours or less of daylight. And yet the most discouraging fact that I have to wrestle with today is the knowledge that the weather will be this way for the next nine months.
[I exhale a deep sigh...] ![]()
Three months from now is the Winter Solstice, at which time we will confront the shortest day of the year; after that, we will at least have the small consolation that each day will be a little longer than the last, but we still won't see much of the sun until sometime next June or July.
[I heave another deep sigh...] ![]()
I wonder how much a plane ticket to Hawaii would cost in January? ![]()