IIS 6: Setting up SSL - Part 3: Installing the Certificate
17 February 2011 • by Bob • IIS, SSL
In part three of my series on setting up SSL on IIS 6, I'll describe the steps that are necessary to install an SSL certificate. Simply out of convenience I broke this process into two sections:
- Installing Your Certificate (Required)
- Verifying Your Certificate (Optional)
Installing Your Certificate
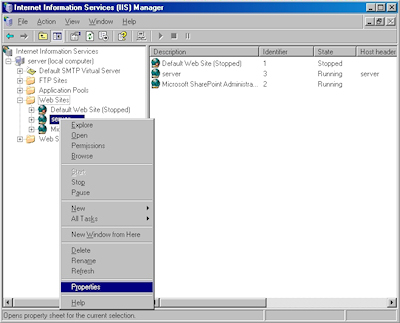
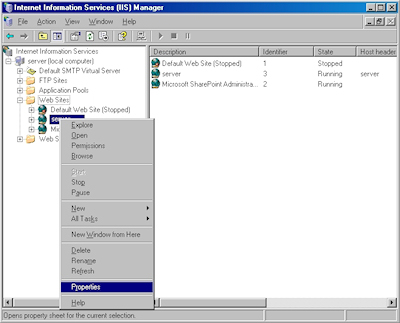
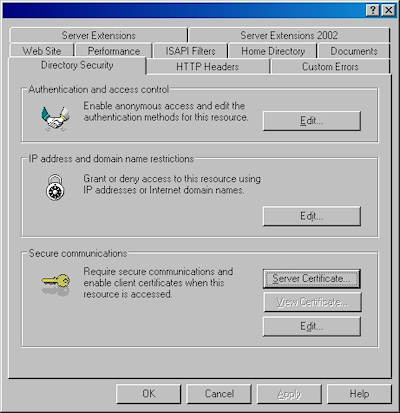
- Bring up the properties for a website:
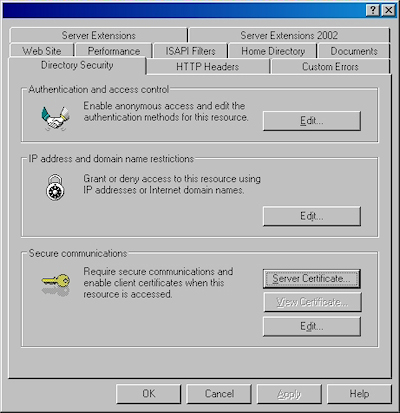
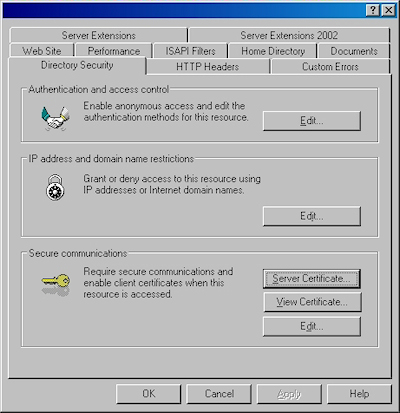
- Switch to the "Directory Security" tab and click "Server Certificate:"
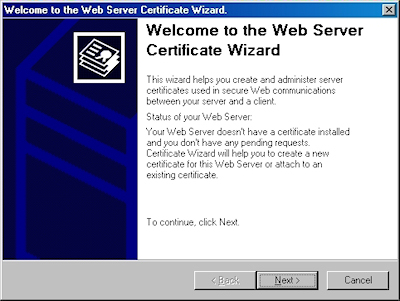
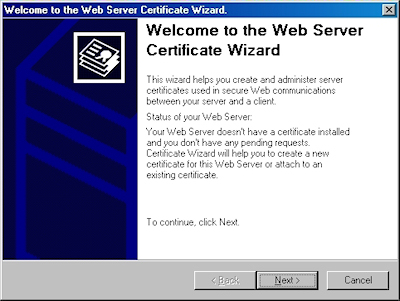
- Click "Next" to bypass the first page:
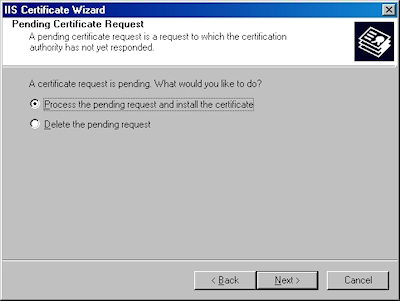
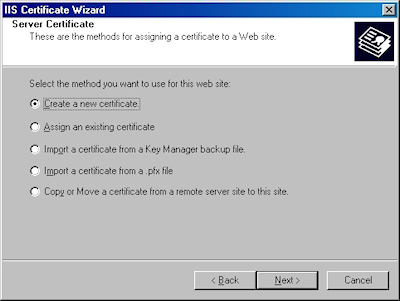
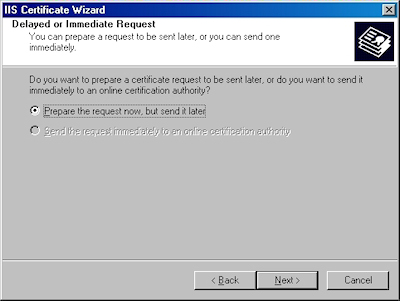
- Choose to process the request and click "Next":
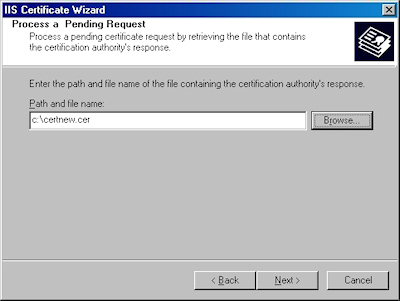
- Click "Browse" to the locate your certificate request:
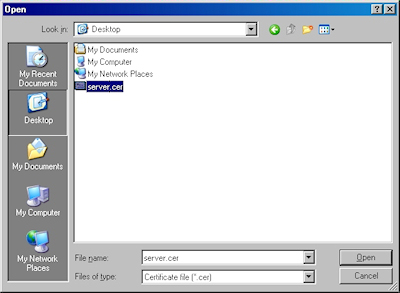
- Browse to the location of your certificate, highlight it, and click "Open":
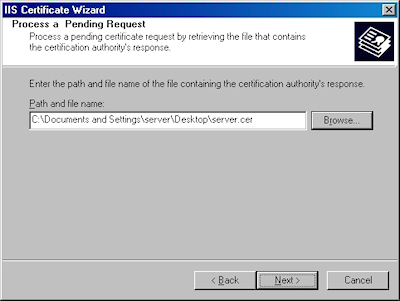
- Verify the location of your certificate and click "Next":
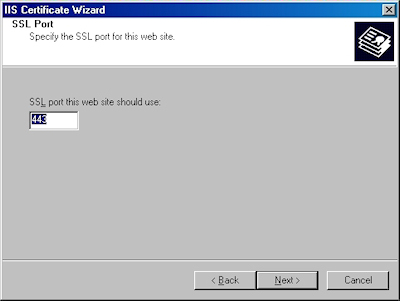
- Choose your SSL port and click "Next":
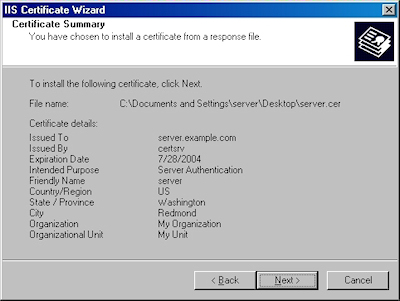
- Review the information to make sure it is correct and click "Next":
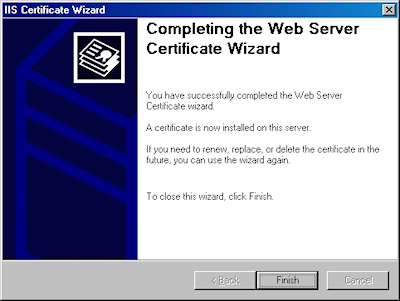
- Click "Finish" to close the wizard:
- Notice that you now have all the buttons available for SSL.
Verifying Your Certificate
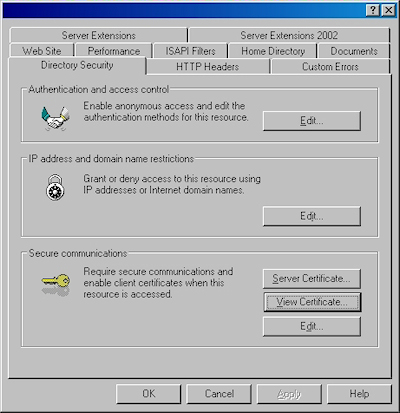
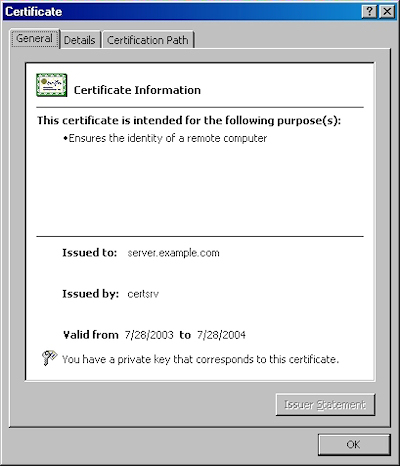
- Click the "View Certificate" button:
- On the "General" tab, if the certificate is good you will see a normal certificate icon. (If no, you will see a warning or error icon.)
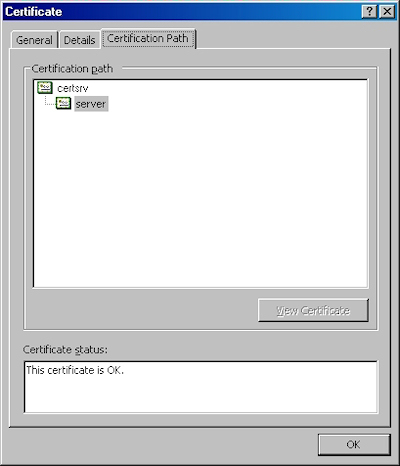
- On the "Certification Path" tab you will see your certificate hierarchy:
That wraps it up for creating, submitting, obtaining, and installing a certificate. In subsequent blogs I'll post some appendices with instructions about setting up Certificate Services on Windows Server 2003.
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
IIS 6: Setting up SSL - Part 2: Submitting a Certificate Request and Obtaining a Certificate
16 February 2011 • by Bob • IIS, SSL
In part two of my series on setting up SSL on IIS 6, I'll describe the steps that are necessary to obtain an SSL certificate. Typically you would submit your certificate request to any one of several Certificate Authorities (CA); and there are several that are available. Here are just a few:
- Thawte Digital Certificates
http://www.thawte.com/ - VeriSign Digital Certificates
http://www.verisign.com/
The steps to obtain a certificate differ for each CA, and it would be way outside the scope of my limited blogspace to include the steps for every CA on the Internet. So for my blog series I'm going to show how to use Certificate Services on Windows Server 2003 to obtain a certificate. This part of the process is broken into three steps:
Submit the Certificate Request
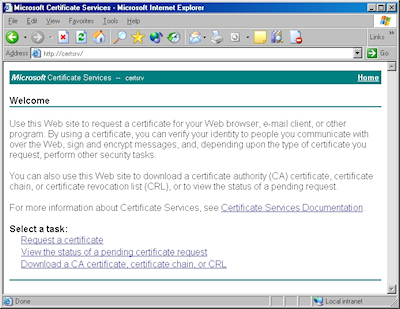
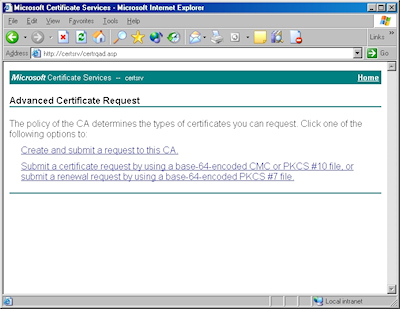
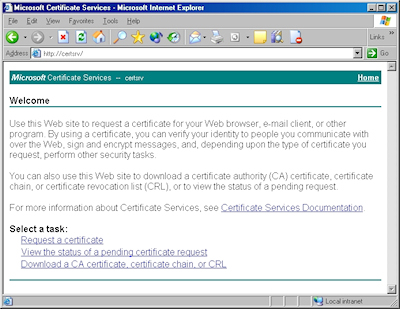
- Browse to the "Certificate Services" website, and then click the link to "Request a Certificate":
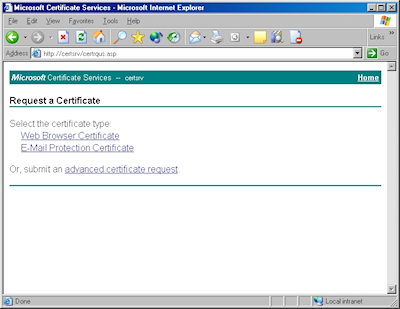
- Click the link to submit an "advanced certificate request":
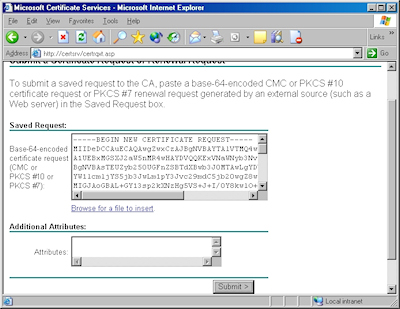
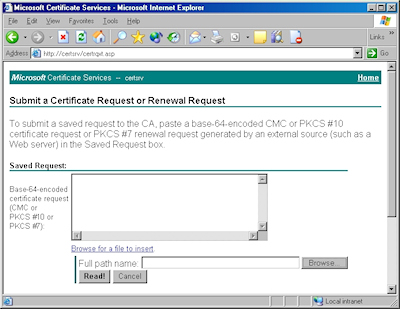
- Click the link to "Submit a certificate request by using a base-64 encoded file":
- Copy the text from your certificate request file and paste it into the "Base-64 Encoded Certificate Request" text box, then click "Submit":
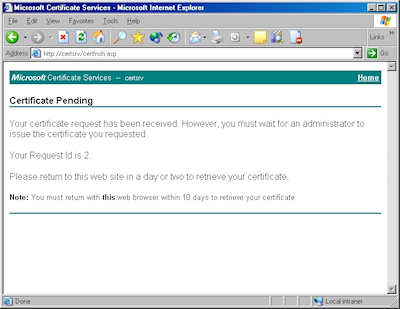
- By default, Certificate Services will return a message stating that your certificate is pending. You will need to notify your Certificate Services administrator that your certificate needs to be approved.
Note: As an alternative to copying the text from your certificate request file, when you are using Certificate Services on Windows Server 2003, you can use the application to read the file for you. To do so, you would need to change the step where you copy and paste the text to the following steps:
- Click the link to "Browse for a file to insert":
- You may be prompted whether to allow an ActiveX control to run; this warning may appear because the web application uses an ActiveX control to read the certificate request file. In order to continue, you need to click "Yes":
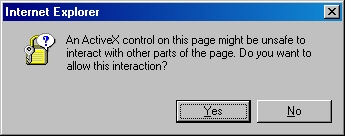
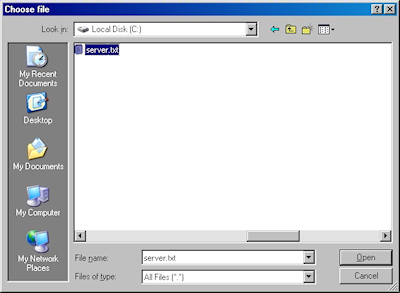
- When the subform appears, click the Browse button:
- Locate your certificate request file, and then click "Open":
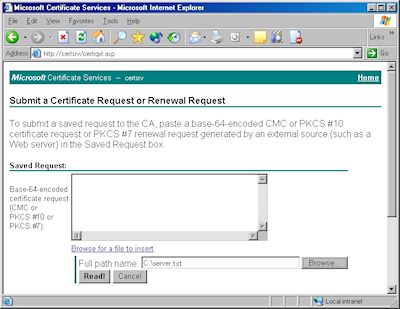
- Click the "Read" button to load the text from your certificate request file, this will insert it into the form:
- Once the text from your certificate request file has been inserted, you can submit the form as you would have done if you had copied and pasted the text manually.
Certificate Processing
At this point the Certificate Authority (CA) will consider your request. I'll post a blog later with details about processing a request using Certificate Services on Windows Server 2003.
Obtain the Certificate
When your certificate request has been processed, you need to use the following steps to save your certificate to your system before you can process it.
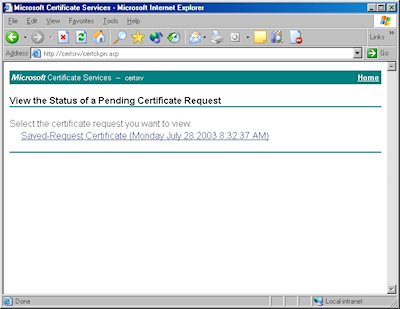
- Browse to the "Certificate Services" website, and then click the link to "View the status of a pending certificate request":
- Click the link for your approved request.
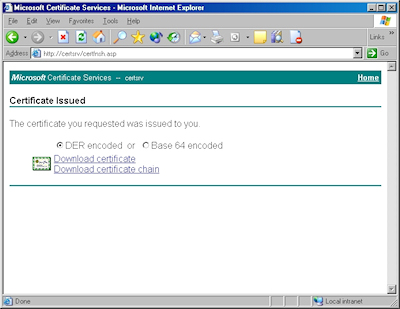
- Click the link to "Download CA certificate":
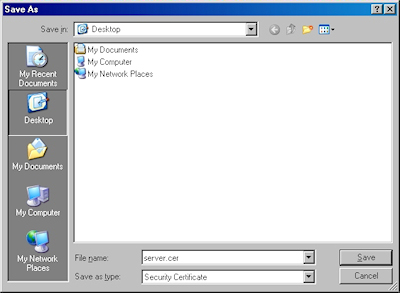
- When prompted, click "Save":
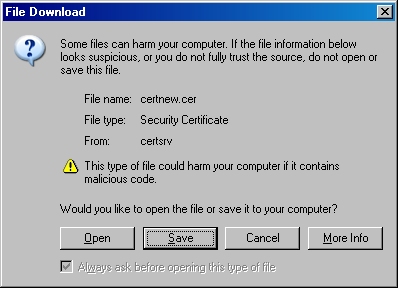
- Save the file to somewhere convenient, like your desktop:
In the next post of this blog series, I'll show you how to install your certificate on IIS 6.
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
IIS 6: Setting up SSL - Part 1: Making a Request
14 February 2011 • by Bob • IIS, SSL
In part one of my series on setting up SSL on IIS 6, I'll describe all of the steps that are necessary to request an SSL certificate for a website. Once you have completed your certificate request, you would send that to a Certificate Authority (CA) for approval. In subsequent blog posts I'll discuss submitting a certificate to a CA - specifically Certificate Services on Windows Server 2003 - and then I'll discuss obtaining a certificate and installing it on your IIS server. But for now, let's get started with a creating certificate request. To do so, use the following steps.
- Bring up the properties for a website:
- Switch to the "Directory Security" tab and click "Server Certificate:"
- Click "Next" to bypass the first page:
- Choose to "Create a new certificate" and click "Next":
- Choose to "Prepare the request now, but send later" and click "Next":
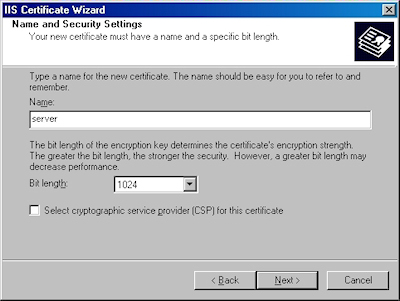
- Enter a friendly "Name" for the request, and your desired "Bit length". Click "Next":
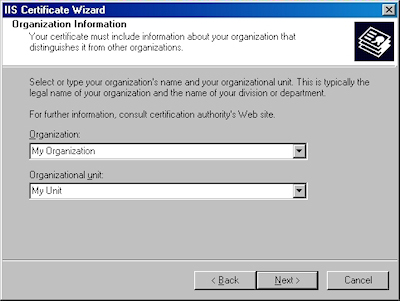
- Enter your "Organization" and "Organization unit", then click "Next":
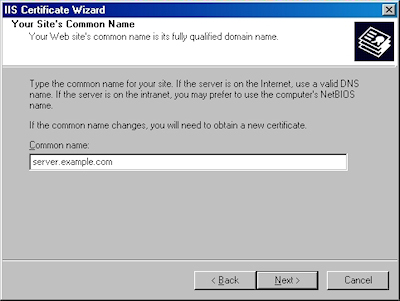
- Enter the "Common name" for your site then click "Next":
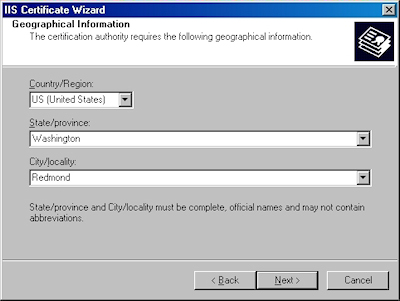
Note: This must be the actual web address that users will browse to when they hit your site. - Enter your "Country", "State", and "City", then click "Next":
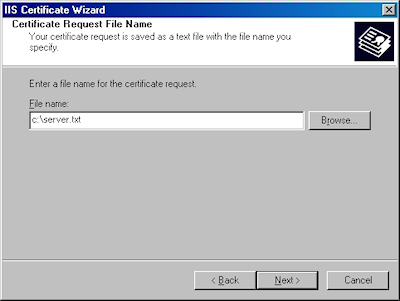
- Enter the "File name" for your request, then click Next:
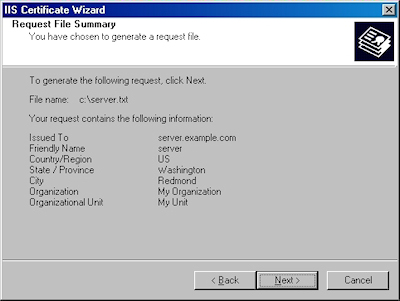
- Review the information for your request, then click Next:
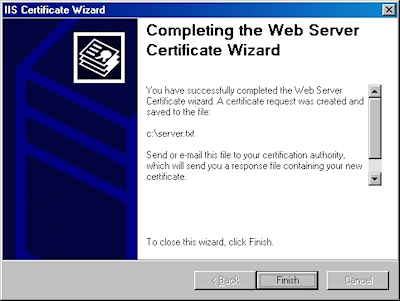
- Click "Finish" to exit the wizard.
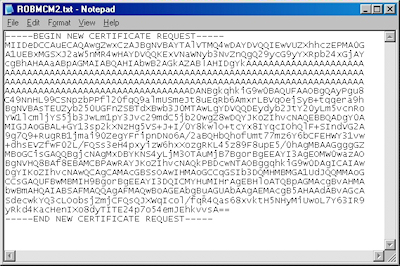
FYI: If you were to open your request file in Notepad, it will look something like the following:
In the next post of my blog series, I'll show you how to use Certificate Services on Windows Server 2003 to obtain a certificate.
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
More 511th Jokes and Humor
05 February 2011 • by Bob • Military
This 11th entry from the annals of 511th MI Company history is a continuation of the jokes that I introduced in my last post. As a quick reminder, these entries were all collected from the voluminous number of utterly useless messages that we sent back and forth between the EW platoons over the ASAS datalink system in the TRQ-32s.
The Official EW2 List of Things "Not to Do with Coffee"
- Don't make oatmeal with coffee
- Don't drink mess hall coffee after eating red lifesavers
- Don't drink mess hall coffee, period
- Don't let Paski near a full cup of coffee while on pos, unless you want to wear it
- Don't pour coffee on your Lt.
- Don't share coffee with your T&A team, unless you plan to resupply them forever
- Don't let Alex, Fred, or J.J. near a full pot of coffee and an ASAS Datalink
- Don't wash your field socks in coffee
- Don't use coffee as brake, hydraulic, or windshield wiper fluid (However, you can use it for rust removal)
- Don't yodel with your mouth full of coffee
- Don't puke, piss, or pop pimples in a pot of coffee
- Don't deploy to the field without lots of it
(J.J. Simmons and Bob McMurray, "Caravan Guard" 1989)
A Story
[Note: As if we hadn't picked on 1LT Stahl enough, I wrote the following story about him. (Of course, D.A.T. means "Dumb Ass Tanker".)]
Once upon a time, all was well in E.W. land. The birds were singing and the jammers were jamming. Happiness just seemed to flow from everything about the EWites. Their lives were simple yet full of good cheer. They truly loved the work that they did and fancied to themselves that maybe it was important for some reason.
But then one day, "IT" came to town. The dreaded D.A.T.-Beast that they had all heard rumors of. There was no way to stop it. No way to prepare. No time to run or hide. It fell upon the helpless EWites and viscously attacked them. It tore at their very hearts as if it derived joy from seeing others suffer. It held no concept of the work that they tried so hard to do. It scarred their precious COMSEC habits. It had no life of its own, and thus it began to feed on the lives of others like some inhuman vampire of man's very essence.
It possessed no concept of right or wrong. It sought only self-importance and personal gain - the incredible irony to the role in which it chose to masquerade itself; an Army officer. By design the title should reflect an attitude of responsibility, accompanied by a genuine sense of caring for the well-being of its subordinates. But the Beast held not one endearing trait as a leader of men. A thoughtless, soulless specter shaped like a man. An empty, hollow shell that somehow tried to crush the will of others to bring itself some sadistic form of pleasure.
In its arrogance and pride, it has the audacity to raise its head in a flare of self-righteous temper and cry, "How dare you question my judgment?" when its imperfections are exposed. But therein lies its tragic flaw; for no puffed up ego that rests upon one's shoulders can lay low enough to duck through every door. Sooner or later it comes crashing to the ground at the wrong time yet in the right place, and if all luck prevails the Beast will die in some strange way. The hope remains that this mass of flesh that torments man will indeed fall prey to the traps that it laid for others, and some as yet unseen force will attack and purge this cancerous ego infection from the Beast, leaving enough to mold into a shape more closely resembling a man.
(Bob "Fred" McMurray, "Bold Lancer" 1989)
The World: Man's Future Foretold...
Life as we know it, has ended.
The nations of the world have all been devastated by a massive nuclear war.
Civilization is no more.
The peoples of the world are massing together in an effort to reclaim their lives.
The leader of the masses has been designated Emperor of the World.
The Emperor has maintained order in America the ten years since WWIII.
Very few oppose the emperor; those who do wish for a quick death.
Damnation of the rebels is personally levied by the hand of the emperor:
J.J. Slayer.
Are you damned in this Hell???????
(J.J. Simmons, Caravan Guard, 1989)
Bad DF-Ville (Sung to the tune of Margaritaville)
Wasting away again in Bad DF-Ville,
Searching for my lost OPFOR freq.
Some people say that there's an LT to blame,
But I know, that it's all TCAE's fault.
DF's and fixes, we all know what we're missin'.
We don't have a clue where the enemy stays.
"Gimme a grid square...I don't care where,"
That's all we hear from the TCAE goons.
But it don't matter, ignore the radio chatter.
Don't even bother, you'll be jumping real soon.
Wasting away again in Bad DF-Ville,
Searching for my lost OPFOR freq.
Some people say that the Blue LT is to blame,
But I know, that it's all TCAE's fault.
(Bill McCollum, Hohenfels 1990)
That wraps it up for this post, but I have a few more jokes in my files to post in the future.
511th Jokes and Humor
03 February 2011 • by Bob • Military
This post marks the 10th installment in my series on the 511th MI Company. So far I have posted all of the lists that I had collected, and I've included some stories along the way. Today's post is a little different - I also collected a bunch of jokes that the ESM squads from the two EW platoons sent back and forth over the TRQ-32's ASAS system. I thought that it might be amusing to let everyone see what we thought was funny at the time. ;-]
In the text file that I had used to collect these jokes I had added the following dedication:
These works best represent the attitudes and feelings shared by most who have sat rack upon the "Pos of Sorrow" at one time or another. They are not always intended to offend, though they sometimes do, but rather to show a rare moment of humor in what might otherwise be a dull and boring life.
To all who wear the Blackhorse, I say with the utmost of heartfelt sincerity and emotion, "Get out of the Army while you still can!"
For each of the jokes that were sent, I managed to write down who sent them and what field problem we were deployed on when I collected them.
Selected Titles from the J. Irwin Rumplemeyer Memorial Book Club
There are many titles to chose from when you join the J. Irwin Rumplemeyer Memorial Book Club. Famous authors, quality works.
- Trotting across Zaire
- I suck, you suck (Speak for yourself, Spanky)
- The Spankmeister of Fulda Gap
- Thermonuclear Racquetball: Applied theories
- Opussum Huntin' with Billy Bob Redneck
- The Chairborne Rangers: Tales from the Orderly Room
- How to make two small hats from a brassiere
- John Carter, Warlord of Mars versus Andy Griffith
- Roadkill: It's not just for breakfast anymore
- Tremble your way to fitness
- Eat right, stay fit, and die anyway
- Getting the point across with Plastique
- The Donner Party Cookbook: Frontier recipes with a twist
- It's not easy being a complete Putz: Biography of an XO
- The Black and Decker home facial reconstruction kit
- The Petroleum Jelly Diet
- What every 98G should know, but doesn't ask. (Who cares!)
- Dude, get a clue.
- Coming of age, new NCO's speak out.
- Gandhi, story of an abused child.
- Does Fu Man Chu?
- Thatcher and Reagan: Portrait of a lust affair
- The life and times of 34 extremely short Saints
- True Confessions: I was a Democrat!!
- "Is safe sex in a car, intercourse with the seatbelts on?"
- How to net with a 32(V) and get a date at the same time
- Sex and the 98G, or Wahhh!!
- Spanking: An in-depth study of milk and ************
- Milk: It's not just for drinking!
- Field Duty: It's not just a job, it's boring!!!!!
- Toxic Dumps: A guide to vacationing in America
(By Dave Paski, "Bold Lancer" 1989)
Note: I believe that Paski's "Biography of an XO" book was in reference to 1LT Stahl, who was thrust on the 511th for several months as Company XO until our CO managed to find a way to push him off on some other unsuspecting Company.
The 10 Top Heavy Metal Albums of All Time
- Burl Ives - "Chainsaw Lust"
- Slim Whitman - "Satan and a Six Pack"
- Roger Whitaker - "Dance, Bitch, Dance"
- Boxcar Willy - "Hobo Hell"
- Mormon Tabernacle Choir - "Sacrifice Two out of Three Wives"
- Boston Pops - "Belial's Orchestra"
- Mitch Miller - "Backwards Singalongs"
- Roy Clark - "Even **** Rot"
- Engelbert Humperdink - "Vanity for my Soul"
- Buck Owens - "I hope that Roy Clark rots"
(J.J. Simmons, "Bold Lancer" 1989)
The F.B.I.'s Latest Wanted Dead List
- Lt. McNeil (Alias "Spanky") - Wanted for impersonating an Officer
- Sgt. Smith - Wanted for impersonating a mature person
- Sgt. Degrood - Wanted for impersonating Dumbo
- Spc. Paski - Wanted for impersonating Sgt. Smith
- Spc. Dodge - Wanted for impregnating sheep
(J.J. Simmons, "Bold Lancer" 1989)
Five Reasons Why Not to Yodel in the Woods
- The Boars only like country
- It causes diarrhea in rodents
- It causes spontaneous itching in embarrassing places
- Burl Ives would sue
- It turns Bill Magan on
(J.J. Simmons, "Caravan Guard" 1989)
That's it for now - I'll post more in future notes.
Manually Localizing FPSE 2002 for Windows Server 2008 and Windows Vista
02 February 2011 • by Bob • FrontPage
The FrontPage Server Extensions from Ready-to-Run Software, Inc. (RTR), are available and supported only in the English language. But that being said, the localized language files for FPSE 2002 are available for download from Microsoft, and if you're willing to do a little work, you can configure the FPSE 2002 administration pages for your website to be displayed in sixteen different languages. (The specific list of languages is provided later in this blog.)
Please note that this information is being presented "as-is" and is not officially supported by Microsoft or RTR.
Downloading and Installing the Localized FPSE 2002 Files
Download the self-extracting MSGS.EXE page that contains the FPSE 2002 language files from the following URL:
Extract the FPSE 2002 files by double-clicking the MSGS.EXE file and specifying an output folder.
By default, the installation package will install all of the localized files to the FPSE 2002 parent folder that is located at:
%ProgramFiles%\Common Files\Microsoft Shared\Web Server Extensions\50
If you run the installation package on your server and accept the default path, then all of the languages will be available on your server.
However, if you only want to have one or more specific languages available, you would need to specify an alternate output folder for the extraction process. Under the output folder that you specified, you will see three folders: admisapi, bin, and isapi. Each of these folders will contain several subfolders, each of which contains the files for each of the localized languages. Each language that you want to have available on your server will need to be copied to their corresponding folders under the FPSE 2002 parent folder at:
%ProgramFiles%\Common Files\Microsoft Shared\Web Server Extensions\50
You may copy all of the localized files to your FPSE directories, or you can select a single language by locating just the appropriate localized subfolders. For example, if you extracted the FPSE 2002 files to your C:\Temp folder and you wanted just the German language files, you would need to select the following folders:
C:\Temp\admisapi\1031
C:\Temp\bin\1031
C:\Temp\isapi\_vti_adm\help\1031
And you would copy those folders to the following paths:
%ProgramFiles%\Common Files\Microsoft Shared\Web Server Extensions\50\admisapi\1031
%ProgramFiles%\Common Files\Microsoft Shared\Web Server Extensions\50\bin\1031
%ProgramFiles%\Common Files\Microsoft Shared\Web Server Extensions\50\isapi\_vti_adm\help\1031
Specifying the Language for an FPSE 2002 Website
Open the service.cnf file for one of your websites in Windows Notepad; this file will be kept in the _vti_pvt folder for a website. For example, for the Default Web Site this file would be at:
C:\Inetpub\wwwroot\_vti_vt\service.cnf
Choose the language abbreviation for your desired language from the list below. For example, if you were using German your abbreviation would be "de-de."
| Language Description | LCID | Abbreviation |
| Arabic - Saudi Arabia | 1025 | ar-sa |
| Chinese - Taiwan | 1028 | zh-tw |
| German - Germany | 1031 | de-de |
| English - United States | 1033 | en-us |
| French - France | 1036 | fr-fr |
| Hebrew | 1037 | he |
| Italian - Italy | 1040 | it-it |
| Japanese | 1041 | ja |
| Korean | 1042 | ko |
| Dutch - Netherlands | 1043 | nl-nl |
| Portuguese - Brazil | 1046 | pt-br |
| Swedish - Sweden | 1053 | sv-se |
| Thai | 1054 | th |
| Chinese - China | 2052 | zh-cn |
| Chinese - Hong Kong SAR | 3076 | zh-hk |
| Spanish – Spain (Modern) | 3082 | es-es |
In the service.cnf file, locate the vti_defaultlanguage entry and change the value to the abbreviation for your desired language. If this value does not exist, you will need to add it. For example, if you were using the German language the syntax would be:
vti_defaultlanguage:SR|de-de
When you open the FPSE 2002 administration pages for your website, you should now see it in your localized language. (Note: You may need to refresh your browser's cache to see it correctly.)
That's all that there is to it. Once again, please note that the version of the FPSE 2002 from RTR is only supported in English; so if you are having any issues, you will need to change the value of the vti_defaultlanguage entry back to "en-us" before you contact RTR for support.
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
More 511th History: The Infamous AAFES Bag Incident
01 February 2011 • by Bob • Military
Here's a story that typifies why I liked MAJ Quinn, and it provides a great illustration of the old adage that good things come to those who wait. Sorry that it's a little longer than most of my other posts.
Part 1 - The Mail Run
In October of 1990, the 511th MI Company deployed to Mt. Meissner for the month. Duty was pretty typical: you'd spend a few days pulling rotations in the vault chasing bad guys or on guard duty, and then you'd have a day off. Time off at Mt. Meissner didn't offer many activities; your options were mostly limited to playing racquetball, watching stale videotapes of AFN programming in the lounge, reading a book, playing cards, or hiking. I think that by this time the no alcohol policy might have been put into effect, seeing as how someone from another unit had flipped their vehicle off the mountain in an alcohol-related incident, so the guys that drank were deprived of that as well.
I think that I was reading a book on one of my days off when SGT DeGrood dropped by the room and asked if I'd be willing to ride shotgun back to Fulda for a mail run. The military had a two-person requirement for military vehicles, so DeGrood simply needed someone to fill the vacant seat. Even though it was my day off, I didn't have anything better to do, so I agreed to go along for the ride. Bear in mind, I was married and I lived off-post, so we wouldn't be picking up my mail on this run - this was just for the single guys' mail. I just figured, "what the heck," so I got into uniform and we drove off in MI-59.
As we approached Fulda, DeGrood mentioned that he'd like to drop by the finance office on Downs Barracks to cash a check. That sounded fine to me - I was just along for the ride. After he cashed his check, we climbed back into MI-59 - and the darn thing wouldn't start. We popped the hood and we checked what we could, but we couldn't figure out what was wrong - this day was obviously not turning out as we had expected. We had few options, so we figured that we could walk down to the PX area and catch the shuttle back to Sickels Airfield where the 511th was located, ostensibly to get the wrecker to tow MI-59 to the Motor Pool (MOPO) for repairs. It took us a few minutes to walk down to the shuttle stop, and DeGrood sat down on the bench near the stop while I leaned against the sign for the shuttle.
I had been looking towards the PX, which was in a different direction than where DeGrood was sitting. When I turned around, I saw the Regimental Commander (RCO), COL Bacevich, approaching the shuttle stop. I snapped to attention and saluted as I rendered the greeting of the day, but DeGrood was looking at the ground, apparently lost in thought. The RCO came to a stop right in front of DeGrood, who suddenly noticed that someone was in front of him and he looked up. When he recognized the RCO, he immediately jumped to attention and saluted.
COL Bacevich asked what the @#$% was DeGrood doing there, and DeGrood started to explain that he was waiting for the shuttle to the airfield when the RCO cut him off. I don't remember what the RCO was yelling at him, but I attempted to interject and explain that our vehicle had died and we needed to get the wrecker from the airfield, and then the RCO started yelling at me. I don't recall his exact words, but he said some pretty awful things and made some completely baseless accusations about DeGrood and me wasting time when we should be on duty. Bear in mind - all of this was in front of a large crowd at the shuttle stop and pretty humiliating. Eventually the RCO ordered DeGrood and me to walk back to the airfield and have our CO (CPT Quinn) call him and explain our behavior. I have no idea what expression was on my face, but I looked at DeGrood, and he looked back at me with that half-grin that he always had - that same grin that he made right after he made a joke about your wife or something. We looked at each other for a second, then we both turned back to the RCO and said, "Yes, sir." Then we started the long walk back to the airfield.
Truth be told, the walk to Sickels airfield and the 511th was perhaps a mile at the most, but it was aggravating because there was a principle involved; I was pretty offended, as was DeGrood, but I think that after we got over the initial shock of what had just happened we started to make a few jokes about the situation.
We eventually arrived at the 511th, and as we were walking down the road that led from the airfield HQ to the 511th barracks, we could see that CPT Quinn was holding a staff meeting in the cafeteria. CPT Quinn caught sight of us, and since we were obviously on foot when we were supposed to be in Mt. Meissner, he walked out to greet us and said, "This has got to be a good story." We filled him in on the details about what had just happened, and we let him know that the RCO was expecting a call. CPT Quinn said not to worry about it, and that he would take care of everything.
So now DeGrood and I went back into vehicle recovery mode. We went to the MOPO to get some of the maintenance guys to take the wrecker over to Downs Barracks and pick up MI-59. After we towed it back to the MOPO, we worked with the maintenance guys until MI-59 was back up and running. By this point it was evening - and the one bright point of my day was that my wife dropped by to pick up our mail so I got to see her for a few minutes.
Once we had MI-59 ready to go and we had packed it with the mail for everyone at Mt. Meissner, I dropped by CPT Quinn's office to let him know that we were leaving. CPT Quinn said that he had called COL Bacevich and tried to explain what the situation was, but the RCO had cut him off and said something to the effect that "CPT Quinn's NCOs had AAFES shopping bags," so he was upset that we were shopping in the PX when we were supposed to be on duty. I explained to CPT Quinn that we didn't have any shopping bags - and CPT Quinn had met us as we were walking up the the barracks empty-handed, so he knew that we were telling the truth. CPT Quinn remarked that "in that case, the RCO is simply out to save face - and he'll lie about it if he has to."
Then CPT Quinn advised us to avoid the RCO if at all possible - that's when I had to drop a bombshell: the RCO was scheduled to visit Mt. Meissner within the next few days. CPT Quinn asked if we could stay out of sight, but I informed him that I had already been scheduled to deliver the operations briefing. CPT Quinn told me, "That had better be one damn good briefing," and then he told DeGrood to stay hidden as much as possible.
Part 2 - Payback
After a few days, DeGrood and I were still pretty upset. We had talked a couple of times about whether there was anything that we could do from a legal perspective - but unfortunately the Army is what it is. If someone abuses their power and position, more often than not they get away with it.
Eventually the day arrived for the RCO's visit to Mt. Meissner. At some point they brought the RCO, his staff & entourage, and CPT Quinn to the vault, where I proceeded to give them a detailed briefing on everything that we had been doing at Mt. Meissner. I followed my briefing by giving everyone a tour of the vault area and the antenna fields, then I took them on a brief tour of the main buildings and barracks areas, and I ended the tour in the cafeteria.
COL Bacevich stuck out his hand and thanked me for a great briefing and tour, then he turned to CPT Quinn and asked, "So this is where your NCOs claim that they're making their mail runs from?" I was momentarily speechless, which wasn't like me in those days - usually I spoke without thinking. But the statement caught me totally off guard. Apparently it had caught CPT Quinn off guard as well, and he asked, "What?" The RCO cracked a smile and said, "You know, those two NCOs that I caught goofing off on duty the other day." I could not believe this - not only had the RCO completely failed to notice who I was - but he was now recounting his warped version of the story to CPT Quinn right in front of me.
At this point - I have no idea what came over me other than a complete lack of respect for my sense of self-preservation and I said, "Sir, I was one of those two NCOs." COL Bacevich was momentarily surprised, but then he picked up his story again by saying, "So you're one of those two NCOs that I caught shamming on duty?" I was suddenly emboldened by his arrogance, and I managed to keep my cool as I said something like, "No, sir - I wasn't even on duty that day. I was only in uniform because I volunteered to ride shotgun so that the single guys could get their mail." I continued to tell the real story of how MI-59 had broken down next the the finance office, how we wanted to take the shuttle to the airfield to get the wrecker, how we were humiliated in front of our peers by him, and how wrongly he had treated the entire situation.
The more that I spoke, the lower COL Bacevich's eyes sank towards the ground, and the further his staff and entourage backed away from him. I don't recall how long I spoke or everything that I said - but I know that I chose my words carefully (for a change) and I did my best to say everything in a respectful manner, even though I was making it clear to everyone in attendance that the RCO had behaved like a complete ass.
Once I had finished, COL Bacevich stared at the ground in front of me for a little bit, then he looked up at his entourage for help - but no one would make eye contact with him. He resumed staring at the ground, shifted in his feet a little, then he mumbled, "That's not the way that I understood the story the other day."
And then, before I could do anything about it, my mouth opened on its own and the following words spilled out: "That's okay, sir - let bygones be bygones. I've gotta get back to work. Thanks!" And I left the cafeteria. I swear that my brain was not involved in that final process - which is probably pretty obvious to everyone who reads this. It wasn't one of my most eloquent speech endings - but once it was said there was no taking it back.
I went back to the vault, where I met up with DeGrood (who was now out of hiding) and everyone else. As I was telling everyone what had just happened, CPT Quinn entered the vault. He walked up to me and kind of cocked his head to one side - like a dog trying to figure something out. After a brief pause he asked, "'Let bygones be bygones?' What the hell does that mean?" I replied, "Honestly, sir - I have no idea what that meant." CPT Quinn laughed, then asked if I still wanted to pursue anything against COL Bacevich. I replied that my desire for retribution had been satisfied; the RCO had humiliated me without cause, and I had humiliated him with cause.
Part 3 - Epilogue
In another of those weird, full-circle occurrences - the story didn't end there. DeGrood and I had orders to PCS back to the states when we finished up at Mt. Meissner, but fate was about to play a dirty trick on us. The Army was gearing up for the first Gulf War, and I was days away from having my household goods picked up and shipped to the states when the Army issued orders to freeze everyone at their present duty station. I did not react well to this news - but CPT Quinn was kind enough to attempt to see if anything could be done. Unfortunately, nothing could be done; this was an Army-wide policy, and the only exception to policy was if your household goods had been picked up - and I fell short by six days.
DeGrood and I were both in the same boat - we were both days away from our PCS dates and our orders were rescinded. But it wasn't just hard on DeGrood and me - there were several people who were about to ETS that were frozen in station as well. SPC Meyer's father had a heart attack, and while his father was recuperating his poor mother was trying to work their family farm by herself. I watched Meyers descend from his normal, outgoing, optimistic, happy-go-lucky self to a person who was withdrawn and quiet. I can't imagine what those months were like for him.
The 11th ACR was not going to be deployed to the Gulf, so we went into a holding pattern while every other unit in Germany that was being deployed started gutting us for everything that we had. (Radios, vehicle parts, etc.) It was around this time that CPT Quinn allowed me to go home on leave for Christmas to help alleviate some of my misery. Since my wife and I hadn't been home in three years, I have always appreciated that gesture more than he ever knew.
Skipping ahead a few months, the first Gulf War had ended, and the military started letting people ETS and PCS again. Meyers was finally able to go home, and I was really happy for him. Eventually the day arrived when DeGrood and I got our new orders - I was going to PCS on something like July 4th of 1991, and DeGrood was leaving within a couple days of my departure.
That was when the Army played its next wildcard - the 11th ACR received orders to deploy to the Gulf for post-war activities, and regimental HQ announced that anyone with a PCS date later than July 1st would have their orders rescinded. I could not believe it - for the second time in my tour at Fulda I was within days of my PCS date and I wasn't going to be allowed to transition. DeGrood didn't make the cutoff date, either - so the two of us went to see MAJ Quinn (who had obviously been promoted from CPT). MAJ Quinn said that he would try to get an exception to policy for the two of us. True to his word, he got back to us shortly after our discussion with good news - he got all the paperwork that we needed; all that we had to do was get COL Bacevich to sign our papers.
(You can see the irony here, can't you?)
So early on a Friday morning DeGrood and I made our way over to regimental HQ in order to see COL Bacevich and request that he sign our paperwork and let us PCS back to the states. We both vividly remembered our history with the RCO, but we were hoping that he didn't remember. When we arrived at the RCO's office he was busy, so his secretary asked us to wait. After a while she said that if we wanted to leave the forms with her, she would make sure that the RCO signed them, and we could pick them up that afternoon. Neither DeGrood nor I wanted to actually see the RCO, so this sounded like a great plan. We left our paperwork and promised to return that afternoon.
The hours ticked by, and the two of us decided to drop by regimental HQ and see if the RCO had signed our paperwork. We arrived at the RCO's office, and only the RCO's secretary was there. (The absence of the RCO was great news.) The secretary said that the RCO had signed our paperwork, and she handed everything back to us. That's when we noticed that DeGrood's paperwork was signed - and mine wasn't. (I swear that I am not making this up.) The secretary remarked that our papers must have stuck together, so she asked if I would leave my paperwork in her office over the weekend and she would make sure that it was signed first thing Monday morning. I hesitantly agreed - but what else was I going to do?
As DeGrood and I left the RCO's office, DeGrood turned to me - and he flashed that same half-grin again. He said, "You know what happened, don't you? I stayed hidden at Mt. Meissner and you pulled that stunt of yours - he's never forgotten your name." Of course that thought was already running through my mind, so I can't say that I found DeGrood's joke all that funny at the time, but many years have gone by and it makes me smile now.
So here's the end of the story - I spent an agonizing weekend worrying what would happen, but I showed up at the RCO's office on Monday to see if he had signed my paperwork. Those who were assigned to the 511th at that time realize that I didn't go to the post-war Gulf with them, so the short answer is - yes, the RCO signed my paperwork.
To this day I do not know if the RCO had actually managed to forget that smart-mouthed NCO who embarrassed him, or if he simply decided to let bygones be bygones.
120 Things the 511th Learned During Hohenfels 1990
31 January 2011 • by Bob • Military
This 8th installment in my posts from the history of the 511th is the list of things that we learned at Hohenfels 1990, which was written by EW2. I have it in my notes that we nicknamed this field problem "Operation Lost Cause," which still seems appropriate.
Before I get to the list, I have to point one thing out - some of the comments in this list were really, really harsh with regard to their treatment of CPT Quinn. Actually, CPT Quinn was one of my favorite commanders - I mean, any commander that would let his subordinates tackle him and throw him in the mud pit in front of his family and peers has got to be pretty cool, right? I actually think that CPT Quinn (later MAJ Quinn) did more for the morale of the company than MAJ Bute ever did. For as much as everyone looked up to LTC Lesser as our best mission-focused commander, he sometimes didn't seem to care all that much about the morale of his subordinates; this was evidenced when MAJ Bute found a pile of awards which were buried in the company commander's desk that LTC Lesser had never handed out to soldiers before he left the 511th. (Some awards had to be mailed to people that had already ETS'd.) So I disagree with what was said about CPT Quinn, but I can try to put things in perspective - we had no history with CPT Quinn when we went on this deployment, and we had something of a bad first impression. But just because I do not agree with some of these statements doesn't mean that I should start cutting things out of the list - so for the sake of posterity I present the list with all of the comments that I would personally consider unnecessary. (Although I did cut out the profanity.)
Without further adieu, here's the list:
Things we learned at Hohenfels '90
- CPT Quinn is a ********, more follows.
- TRQ-30 antennas make great chock blocks. (Right 1LT Innocenti?)
- We must jump at midnight because we need the practice.
- Yes, the TRQ-32 does have a maximum load capacity.
- No matter how bad chow gets, it can always get worse.
- Jumping can be fun if you do it daily.
- T&A teams have short tempers.
- The sludge at the bottom of mess hall coffee really isn't toxic. (???)
- EW2 can run two weeks without air conditioning in the TRQ-32 while EW1 can't last two minutes.
- CPT Quinn is an *******, more follows.
- One should pull guard if there is nothing else to do.
- When all else fails, kick Myers out of the truck.
- The TRQ-30 is the ultimate intercept device. (Not!!!)
- Pork every night gets old pretty quickly.
- D.A. is incapable of reasonable thought early in the morning, or later for that matter.
- Morale gets pretty ugly with no sleep after four weeks in the field and two more to go.
- CPT Quinn is a moron, more follows.
- You don't "Out" Black-6, he "Out's" you.
- Cooks don't appreciate "101 things to do with pork" cookbooks.
- Cooks can actually read!!!
- Everyone wakes up in a wonderful mood after a night jump.
- The 533rd M.I. BN sucks as OPFOR support.
- It's better to be called an ******* than a D.A.T.
- CPT Quinn should be a D.A.T., more follows.
- It's fun to chase boars through the woods wearing Night Vision Goggles.
- The TRQ-32 can be quite an effective jammer. (Not!!!)
- The better that we seem to be doing, the more we get f***** with.
- SGT Degrood sets up a mean camo net. (For a cheeser anyway...)
- Blanco can't I.C.D.; "Please go to MOPP4..."
- Blanco will eat anything.
- CPT Quinn is a devious *******, more follows.
- Breakfast is always more enjoyable when you eat it at lunch.
- Frosted mini-wheats are worth killing for.
- We work better when the C.O. is in Fulda.
- CPT Quinn has twisted, God-image delusions of himself, more follows.
- The 533rd can play both OPFOR and OCE's, because that's fair.
- Always build a hooch in case it rains.
- 24 hour OP's are essential in an eight-hour war.
- Boots look better without polish. (Just ask D.A.)
- Miles gear can still be entertaining without blanks. (Silent but deadly.)
- Everbody wants to be a jammer.
- M-8 alarms work better without batteries.
- Duerkson can I.C.D. while sleeping 500 yards from a jammer.
- Whitfield can never get enough sleep.
- J.J. should come to the field, even if he is clearing.
- It's amazing how much handcopying English isn't like handcopying Russian.
- It always pays to have a radio mechanic and your armorer look at your generator.
- MOPP2 is much more fashionable than MOPP1. (Booties are cute.)
- Too bad cigars don't keep away officer pests like they do insects.
- The new style in EW2 sleepware is the Hoff Stealth Tent.
- Landline for field phones only serves as trip wires.
- Chow is appreciated more if it's been held a few hours, even more if it's cooked.
- CPT Quinn is a ******-******** ***-****** from a festering ***-****, (and Duerkson should know!), more follows.
- We all need more driver's training when Service's brakes go out.
- There is a difference between the hood and brake release.
- You can learn a lot from Taboo Freqs.
- Comm's work better with a fill in the Vinson.
- You can do a lot of damage with an M-60 and no miles equipment.
- Our officers would get us killed if this were real combat.
- If you can lie, you can I.C.D.
- BCG's look better on Duerkson than real glasses would.
- D.A. is secretly a Leprosy carrier.
- 98C's should always man Trojan when 98G's go to the field.
- Alex is the world's biggest shammer, McGee takes a close second.
- Never offer D.A. a dip, he'll take the whole can.
- It pays to buy quart-sized coffee mugs.
- CPT Quinn is a putz, more follows.
- The only thing worth buying at the shoppette is the Blonde.
- (This is a number not seen at Hohenfels.)
- The TRQ-32's DF antennas look much better with chem-lites dangling from them.
- Officers don't like lists of things we've learned.
- Fred can make mistakes, too.
- Sleep deprivation is good for the soul.
- You can go for days without shaving, and even then only an officer will notice.
- You can get a TRQ-32 level anywhere if you have enough rocks.
- If McCollum died, EW1's TRQ-32 squad would be lost forever.
- We don't need a TCAE now that we have CPT Quinn.
- We all love CPT Quinn's radio procedures, more follows.
- It's amazing how much you can not give a s*** about.
- You don't need to start the radio watch vehicle all that often.
- We need more camo nets. (Not!!!)
- You're in the war even if you're not in the box.
- Married guys don't really want to see their wives.
- Everyone has to stay in the field, but CPT Quinn gets to go home anyway.
- Uncle Martin is a coffee-waster.
- 1LT Innocenti really has no idea what the hell is going on.
- Listening to OCE nets gives you an edge on the battle.
- Miles gear gets comfortable the more that you wear it. (Not!!!)
- You can handcopy on the move even if you can't drink coffee.
- It's fun to be the 1LT's driver. (Not!!!)
- OCE's are friendly people.
- We're all having a great time.
- The RCO can live to eat his words. ("EW support sucks in Hohenfels...")
- You can still drive vehicles with Class III leaks and broken windshields.
- "4-LO" is a wonderful gear.
- Life is not complete without shaving.
- We just came here to feed the bugs.
- Life was easier with Babbs.
- EW2 is invisible to armed OPFOR task forces.
- There is no such thing as down time.
- If you don't want to lose at Mumbly-Peg, play with Jeff Morris.
- Hedgehogs sound deceptively large at night.
- Night Vision Goggles and flashlights don't mix.
- 1LT Innocenti does do a good impression of a Mexican.
- 1LT Innocenti and Flores do know where the bad parts of Houston are. (Wonder why?)
- OPFOR sucks.
- Reconning can be fun.
- Rocks don't make good baseballs, but "out-of-bounds" markers make great bats.
- After five weeks with Whitfield you can still hate Rap Music.
- You can read a lot of books when you're bored to tears.
- When all else fails, scream at the OCE's.
- Fred is a self-proclaimed geek.
- Myers knows lots of useless facts.
- It helps to count the number of days you have left in Fulda.
- 1LT Innocenti has no life.
- OPFOR has no sense of humor.
- Whitfield will take a Humvee where no man has gone before.
- We make life harder on ourselves by not whining as hard as EW1.
- We all have bad attitudes.
- If you are winning at Hohenfels, you must be cheating.
One brief explanation for point #12 - there was some steep hill in Hohenfels that EW1 couldn't get their TRQ-32 to climb, no matter who was behind the wheel. Then a few days later EW2 tried to take the hill; several people from EW2 made the attempt with our TRQ-32, but to no avail. That is - until I got behind the wheel, and I ordered Steve "Felix" Myers to get out of the truck. In hindsight, I completely realize that it was just as much luck as skill that enabled me to get that motorized mammoth up the mountain - but that didn't stop me from having the coolest bragging rights for the next few weeks. (FWIW - D.A. Morris was there, and he also failed to get the TRQ-32 up the hill despite several attempts, so he can vouch for my story - just in case you have reason to doubt my sincerity. ;-] )
Life after FPSE (Part 6)
31 January 2011 • by Bob • FrontPage, IIS, WebDAV
In this latest installment on my series about configuring your server for hosting without the FrontPage Server Extensions (FPSE), I'd like to discuss a couple of WebDAV best practices that I like to use.
Blocking FPSE-related Folders with Request Filtering
In my How to Migrate FPSE Sites to WebDAV walkthough, I discuss the following FPSE-related folders:
| Folder | Notes |
| _fpclass | Should contain publicly-available FrontPage code - but should be secured. |
| _private | The FrontPage Server Extensions often keep sensitive data files in this folder, so it should be secured to prevent browsing. |
| _vti_bin | This is the virtual directory for the FrontPage Server Extensions executables. This path is configured to allow executables to function, and since we are migrating sites to WebDAV it should be secured to prevent browsing. |
| _vti_cnf | The FrontPage Server Extensions keep sensitive metadata files in this folder, so it should be deleted or secured to prevent browsing. |
| _vti_log | The FrontPage Server Extensions keep author logs in this folder, so it should be deleted or secured to prevent browsing. |
| _vti_pvt | This folder holds several files that contain various metadata for your website, and should be secured. |
| _vti_txt | This folder contains the text indices and catalogs for the older FrontPage WAIS search. Since later versions of FrontPage only used Index Server, it is safe to delete this folder, but at the very least it should be secured to prevent browsing. |
| fpdb | FrontPage keeps databases in this folder, so it should be secured to prevent browsing. |
One of the actions that I usually take on my servers is to lock down all of these folders for my entire server using Request Filtering. To do so, open a command prompt and enter the following commands:
cd %WinDir%\System32\inetsrv
appcmd.exe set config -section:system.webServer/security/requestFiltering /+"hiddenSegments.[segment='_vti_cnf']" /commit:apphost
appcmd.exe set config -section:system.webServer/security/requestFiltering /+"hiddenSegments.[segment='_fpclass']" /commit:apphost
appcmd.exe set config -section:system.webServer/security/requestFiltering /+"hiddenSegments.[segment='_private']" /commit:apphost
appcmd.exe set config -section:system.webServer/security/requestFiltering /+"hiddenSegments.[segment='_vti_log']" /commit:apphost
appcmd.exe set config -section:system.webServer/security/requestFiltering /+"hiddenSegments.[segment='_vti_pvt']" /commit:apphost
appcmd.exe set config -section:system.webServer/security/requestFiltering /+"hiddenSegments.[segment='_vti_txt']" /commit:apphost
appcmd.exe set config -section:system.webServer/security/requestFiltering /+"hiddenSegments.[segment='fpdb']" /commit:apphost
Note: You should only enter the following commands if you are sure that you will not be using FPSE anywhere on your server!
cd %WinDir%\System32\inetsrv
appcmd.exe set config -section:system.webServer/security/requestFiltering /+"hiddenSegments.[segment='_vti_bin']" /commit:apphost
These settings will prevent any of the FPSE-related paths from being viewed over HTTP from a web browser; web clients will receive an HTTP Error 404.8 - Not Found message when they attempt to access those paths. But that being said - when you enable WebDAV for a website by using the Internet Information Services (IIS) Manager, it will configure the Request Filtering settings that enable WebDAV clients to access those paths through WebDAV requests, even though access from a web browser is still blocked. (All of this is made possible through the built-in integration between WebDAV and Request Filtering.
Two Sites are Better Than One
In part 4 of this blog series I discussed why I like to set up two websites when using WebDAV; as a quick review, here is the general idea for that environment:
- The first website (e.g. www.example.com) is used for normal HTTP web browsing
- The second website (e.g. authoring.example.com) is used for for WebDAV authoring
There is a list of several reasons in that blog post why using two sites that point to the same content can be beneficial, and I won't bother quoting that list in this blog post - you can view that information by looking at that post.
But that being said, one of the items that I mentioned in that list was using separate application pools for each website. For example:
- The first application pool (e.g. www.example.com) is configured to use delegated configuration
- The second application pool (e.g. authoring.example.com) is configured to ignore delegated configuration
This configuration helps alleviate problems from uploading invalid Web.config files that might otherwise prevent HTTP access to your website. By way of explanation, the WebDAV module attempts to validate Web.config files when they are uploaded over WebDAV - this is done to try and prevent crashing your HTTP functionality for a website and being unable to fix it. Here's what I mean by that: IIS 7 allows configuration settings to be delegated to Web.config files, but if there is a mistake in a Web.config file, IIS 7 will return an HTTP Error 500.19 - Internal Server Error message for all HTTP requests. Since WebDAV is HTTP-based, that means that you won't be able to fix the problem over WebDAV. (If the WebDAV module didn't perform any validation, that means that your website would become unusable and unrepairable if you had uploaded the bad Web.config file over WebDAV.) To help alleviate this, the WebDAV module performs a simple validation check to prevent uploading invalid Web.config files. But if you save an invalid Web.config file through some other means, like the local file system or over FTP, then you will have no way to repair the situation through WebDAV.
This leads us back to the idea that you can implement when you are using two websites - you can configure the application pool for the WebDAV-enabled website to ignore delegated configuration settings; so it doesn't matter if you have an invalid Web.config file - you will always be able to fix the problem over WebDAV. To configure an application pool to ignore delegated configuration settings, open a command prompt and enter the following commands:
cd %WinDir%\System32\inetsrv
appcmd.exe set config -section:system.applicationHost/applicationPools /[name='authoring.example.com'].enableConfigurationOverride:"False" /commit:apphost
Note: you need to update the highlighted section of that example with the name of your website, such as "Default Web Site," etc.
When you have two websites configured in this example and you have an invalid Web.config file that is causing the HTTP 500 error for the www.example.com website, you can still connect to authoring.example.com via WebDAV and fix the problem.
More Information
For additional information on the concepts that were discussing in this blog, see the following topics:
- Life after FPSE (Part 4) - This blog post discusses a couple of WebDAV-related topics, and includes my list of additional reasons why configuring two websites when you are using WebDAV can be advantageous.
- Adding Application Pools - This topic contains the detailed information about the enableConfigurationOverride setting for an application pool.
- Using the WebDAV Redirector - This walkthrough discusses mapping drives to WebDAV-enabled websites.
I hope this helps.
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/
IIS 6: Setting up SSL - Overview
31 January 2011 • by Bob • IIS
Many years ago I wrote a series of instructions that used dozens of screenshots in order to show my coworkers how to set up and enable Secure Sockets Layer (SSL) communications in IIS 5, which I eventually turned into a blog series on one of my personal blog sites. A few years later I wrote a sequel to that series of instructions for my coworkers, and I wanted to turn that into a series of walkthroughs in the IIS.net website. Sometime ago I proposed the idea to Pete Harris, who was in charge of IIS.net at the time, but then I changed jobs and we scrapped the idea. We followed up on the idea a short time ago, but we just couldn't find a place where it made sense to host it on IIS.net, so Pete suggested that I turn it into another blog series. With that in mind, over a series of several blog entries I will show how to configure SSL on IIS 6.
Note: This first post will leverage a lot of the content from the overview that I wrote for my IIS 5 blog series, but subsequent posts will reflect the changes in IIS 6.
Much like IIS 5, setting up SSL on IIS 6 is pretty simple. SSL is a Public Key/Private Key technology, and setting up SSL is essentially obtaining a Public Key from a trusted organization. The basic process for working with SSL is reduced to the following actions:
- Creating a Certificate Request
- Obtaining a Certificate from a Certificate Authority
- Installing the Certificate
While not necessary, installing certificate services on your computer is helpful when troubleshooting SSL issues, and I'll discuss that later in this blog series.
Creating a Certificate Request
This is a series of steps that need to be performed on the web server, and they differ widely depending on the server and version. A web administrator is required to enter information about their organization, their locality, etc. This information will be used to validate the requester.
Obtaining a Certificate from a Certificate Authority
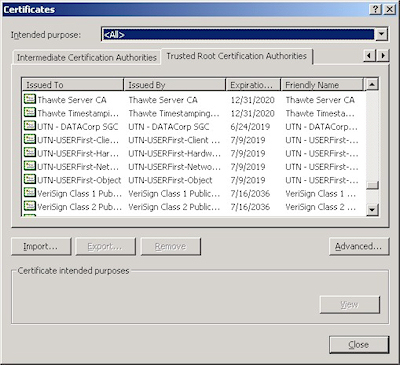
This is when a web administrator submits their request for a certificate to a Certificate Authority (CA), which is a trusted organization like VeriSign or Thawte. For a list of trusted organizations, see the following section in Internet Explorer.
You can choose to trust a new CA by obtaining the Root Certificate from the CA. (I'll post an Obtaining a Root Certificate blog with more information later.)
Installing the Certificate
After a request has been processed by a CA, the web administrator needs to install the certificate on the web server. Once again, this series of steps needs to be performed on the web server, and the steps differ depending on the web server and version.
For the Future...
In future blogs I'll go through the steps for creating certificate requests, obtaining certificates from a CA, and installing certificates. Following that, I'll discuss setting up a CA for testing SSL in your environment.
Note: This blog was originally posted at http://blogs.msdn.com/robert_mcmurray/